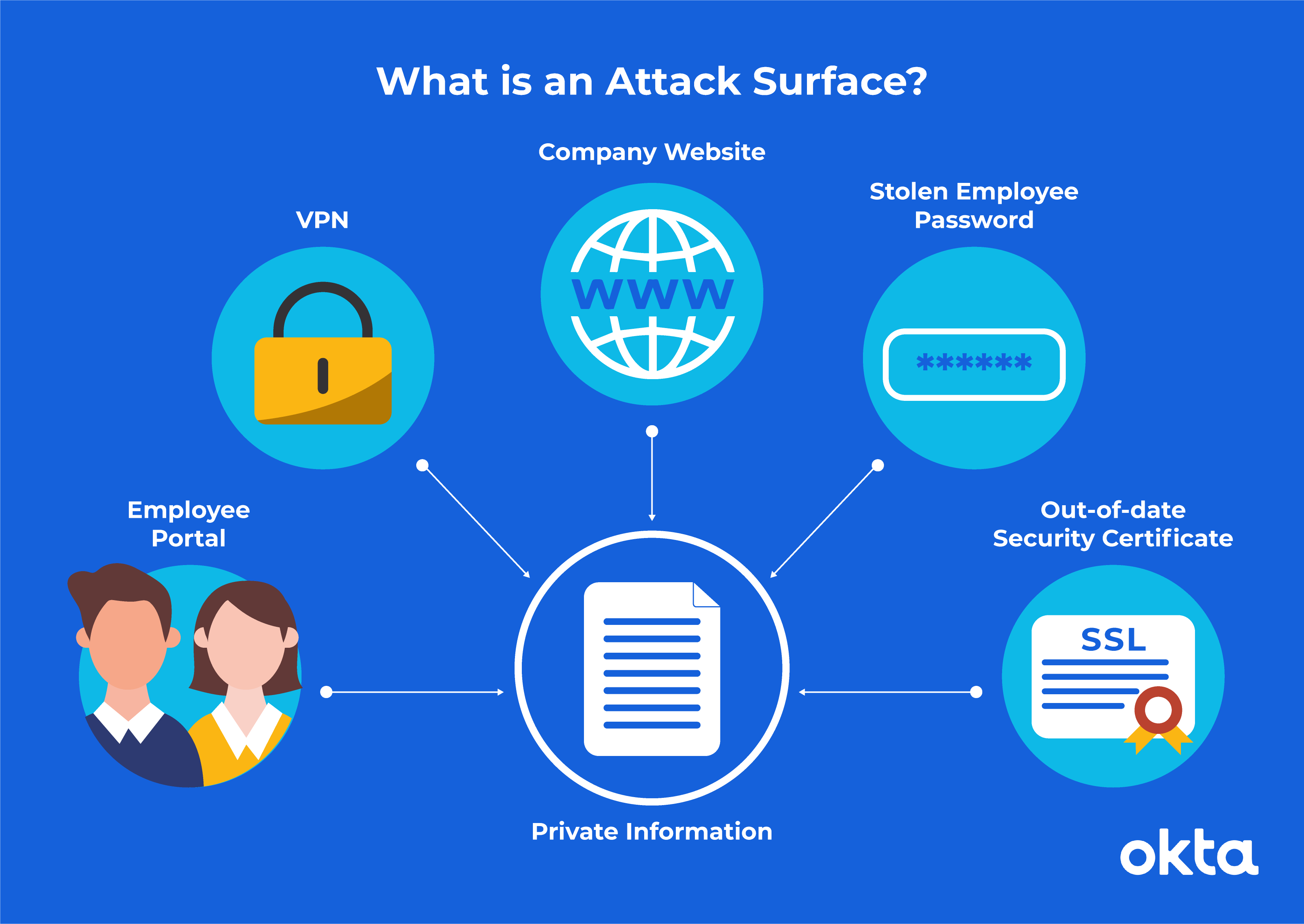
A hacker with that data could move past your firewalls and access:
- Employee records. Social security numbers, home addresses, evaluations, and other private data sit inside Human Resources folders. Hackers want to get their hands on this personal information.
- Product development information. Your product launch could fail before it starts if your competitors learn about your innovations in advance.
- Financial records. Private salary data, rental agreements, vendor contracts, and more could move out of your protection and into the public sphere.
- Patent-protected data. Your secret sauce or black-box innovation is hard to protect from hackers if your attack surface is large.
Once past your firewalls, hackers could also place malware into your network. Spyware could follow your employees throughout the day, recording each keystroke. A ticking time bomb of data destruction could await the next online decision.
Hacks like this are incredibly expensive. Experts say hack damage costs companies $400 billion per year.
What Are Attack Vectors?
Attack vectors are the landmarks on an attack surface. Each one represents vulnerabilities, such as access points, protocols, and services.
You may think you have only one or two crucial vectors. But chances are, you have dozens or even hundreds within your network.
For example, experts outlined current attack vectors of large companies and found problems with:
- Vulnerable web components. A quarter of the top 10,000 Alexa domains had servers running at least one component that was considered weak.
- Expired certificates. The largest companies had about 300 of these vulnerabilities.
- Public dev sites. More than 700 of these were web accessible, making them susceptible to attacks.
Attack vectors are unique to your company and your circumstances. No two organizations will have the same attack surface. But problems commonly stem from these sources:
|
Attack Vector
|
Issue
|
Solution
|
|
APIs
|
APIs can supercharge business growth, but they also put your company at risk if they are not properly secured.
|
Secure all APIs by using tokens, encryption, signatures, and other means to keep your organization protected.
|
|
Distributed denial of service (DDoS)
|
A DDoS attack floods a targeted server or network with traffic in an attempt to disrupt and overwhelm a service rendering inoperable.
|
Protect your business by reducing the surface area that can be attacked. This is done by restricting direct access to infrastructure like database servers. Control who has access to what using an identity and access management system.
|
|
Encryption
|
If your protocols are weak or missing, information passes back and forth unprotected, which makes theft easy.
|
Confirm all protocols are robust and secure.
|
|
Insiders
|
A disgruntled employee is a security nightmare. That worker could share some or part of your network with outsiders. That person could also hand over passwords or other forms of access for independent snooping.
|
Work with HR to put protocols in place, so you’re ready if this situation occurs.
|
|
Malware
|
This is a nasty type of software designed to cause errors, slow your computer down, or spread viruses. Spyware is a type of malware, but with the added insidious purpose of collecting personal information.
|
Keeping abreast of modern security practices is the best way to defend against malware attacks. Consider a centralized security provider to eliminate holes in your security strategy.
|
|
Passwords
|
Weak passwords (such as 123456!) or stolen sets allow a creative hacker to gain easy access. Once they’re in, they may go undetected for a long time and do a lot of damage.
|
Set up requirements to ensure all passwords are strong, or use multi-factor, or even passwordless authentication.
|
|
Phishing
|
A seemingly simple request for email confirmation or password data could give a hacker the ability to move right into your network. Many phishing attempts are so well done that people give up valuable info immediately.
|
Your IT team can identify the latest phishing attempts and keep employees apprised of what to watch out for.
|
|
Ransomware
|
Hackers move into your network, lock it down, and ask for money to release it. In 2019, more than 205,000 organizations faced a demand just like this.
|
Identify where your most important data is in your system, and create an effective backup strategy. Added security measures will better protect your system from being accessed.
|
Identify where your most important data is in your system, and create an effective backup strategy. Added security measures will better protect your system from being accessed.
Even your home office isn't safe from an attack surface threat. The average household has 11 devices connected to the internet, reporters say. Each one represents a vulnerability that could lead to a subsequent breach and data loss.
If a majority of your workforce stays home throughout the workday, tapping away on a home network, your risk explodes. An employee may be using a corporate device for personal projects, and company data may be downloaded to a personal device.
Each office in which a person works and each device that accesses the network should be assessed.
Attack Surface Analysis: Step by Step
To reduce your attack surface and hacking risk, you must understand your network's security environment. That involves a careful, considered research project.
An attack surface analysis will help you identify immediate risks and potential future risks.
Your attack surface analysis won't fix every problem you find. Instead, it gives you an accurate to-do list to guide your work as you attempt to make your company safer and more secure.
Follow this roadmap as you complete your attack surface analysis:
- Identify vulnerabilities. Your attack surface includes all of your access points, including each terminal. But it also includes paths for data that move into and out of applications, along with the code that protects those critical paths. Passwords, encoding, and more are all included.
- Pinpoint user types. Who can access each point in the system? Don't focus on names and badge numbers. Instead, think about user types and what they need on an average day.
- Perform a risk assessment. Which spots have the most user types and the highest level of vulnerability? These areas should be addressed first. Use testing to help you uncover even more problems.
- Secure your reporting. How will you know when you're dealing with a data breach? What does your company do in response to a threat? Look over your rules and regulations for additional issues to check.
In large companies, this process is measured in months, not hours. Be as thorough as you can. The more you uncover, the safer your company will be.
Attack Surface Reduction Strategies
Mapping guides your cleanup project. Move methodically from the most vulnerable point to the least.
Typical attack surface reduction techniques involve:
- Access. Look over network usage reports. Ensure that the proper people have rights to sensitive documents. Lock down areas with unauthorized or unusual traffic.
- Cleanup. When do you walk through your assets and look for expired certificates? If you don't have a routine cleanup schedule created, it's time to write one and then stick to it.
- Code. Are you running code that's out of date or no longer necessary?
- Passwords. Do your employees follow password best practices? Do they know what to do if they lose their passwords or usernames?
- Scans. Do you check your network health regularly? How are you alerted when problems appear?
This is a short list that helps you understand where to begin. You may have many more items on your to-do list based on your attack surface analysis.
Reduce Attack Surface in 5 Steps
With immediate cleanup completed, look for ways to tighten your protocols so you'll have less cleanup work after future attack surface analysis projects.
Follow these five steps to get started:
- Assume zero trust. No user should have access to your resources until they've proven their identity and the security of their device. It's easier to loosen these requirements and allow people to see everything, but a mindset that puts security first will keep your company safer.
- Create strong user access protocols. In an average company, people move in and out of influence with alarming speed. Each person needs access to your network to do good work, but those rights should be removed as soon as the person is no longer part of your organization. Pair with Human Resources to solidify password policies.
- Use strong authentication policies. Consider layering strong authentication atop your access protocols. Use attribute-based access control or role-based access access control to ensure data can be accessed by the right people.
- Protect your backups. Replicas of code and data are a common part of a typical company's attack surface. Use strict protection protocols to keep these backups safe from those who might harm you.
- Segment your network. The more firewalls you build, the harder it will be for hackers to get into the core of your business with speed. Do it right, and you can drive security controls down to just a single machine or user.
Never underestimate the importance of reporting. Even when you've taken all of these steps, you must monitor your network regularly to ensure that nothing has broken or grown obsolete. Build time into each workday to assess the current threats.
To learn if you’re protecting your company, view our checklist: 12 Key Steps for Protection Against Data Breaches.
References
Unwitting Workers Give Hackers Keys to Fortune 500 Firms' Networks: Study. (October 2014). NBC.
Companies Lose $400 Billion to Hackers Each Year. (September 2015). Inc.
Attack Surface Area Larger Than Most Businesses Believe. (June 2020). Dark Reading.
Pandemic Giving Ransomware 'Greater Attack Surface' as Tactics Shift, Ex-FBI Agent Says. (August 2020). State Scoop.
Attack Surface Analysis Cheat Sheet. CheatSheets Series.
Ransomware Attacks Grow, Crippling Cities and Businesses. (February 2020). The New York Times.
Cyberattacks Now Cost Companies $200,000 on Average, Putting Many Out of Business. (March 2020). CNBC.
The Proposed Solution. (2015). How to Defeat Advanced Malware.
U.S. Households Have an Average of 11 Connected Devices, and 5G Should Push That Even Higher. (December 2019). Variety.
Beware This Sinister New ‘Dark Side’ $1 Million Cyber Threat, You Must. (August 2020). Forbes.
Why Every Small Business Should Care About Cyberattacks, in 5 Charts. Vox.
5 Ways to Reduce Your Attack Surface. (August 2018). Security.