What Is Spear Phishing?
Spear phishing is a form of cyber attack targeted at a particular person or small set of individuals. In these scams, bad actors research their chosen targets and attempt to convince them to surrender sensitive data or financial information. Spear phishing attacks may also aim to infect user devices with malware, allowing attackers to steal the data they need to carry out further attacks on an organization.
Spear phishing scams succeed in part because the perpetrators research their targets so as to pose as trustworthy sources. With the rise of technologies like machine learning, which can help attackers create more compelling messages, spear phishing is an increasingly dangerous threat. Phishing can be conducted across any of the many communication apps employees use on a day to day basis, giving cybercriminals more opportunities to successfully exploit gaps in users’ security awareness. Organizations must contend with a growing attack surface as they use mobile devices with multiple communication apps.
In this post, we explore this spear phishing definition in depth so you can better understand how these attacks work and adopt effective strategies to protect your organization.
How does spear phishing work?
Spear phishing campaigns begin with personal information. Bad actors may start by exploring email addresses harvested in previous data breaches and then refine their targeting efforts through online research.
Company websites often provide a general picture of an organization’s processes, business partners, technologies, ongoing initiatives, and other insights that can make it easier for bad actors to construct a credible scam. Business-friendly social media platforms such as Twitter and LinkedIn also allow threat actors to observe the different roles and relationships in an organization and determine who to target and imitate. Personal profiles on Facebook and Instagram may reveal sensitive information about the target that attackers can exploit in their messages.
By combining information from these sources, attackers can gain an accurate and detailed understanding of who they’re targeting, and use that to create a plausible narrative.
Spear phishing emails typically use emotive language to invoke urgent actions—whether there’s a malicious file that a ‘colleague’ needs you to review today, or a false security alert from an attacker impersonating your bank, complete with a link to change your password. This urgency usually comes with a prompt to break company policies and protocols, like making financial transactions or revealing information without following typical compliance procedures.
Despite the lengths bad actors go to when impersonating others, the details often give the game away. Check for the following tells:
- Look out for incorrect email addresses—ones similar to official company accounts, but with slight differences that aren’t immediately obvious at a quick glance like typos or foreign domains.
- Language is also a telling sign, as cyber criminals may use expressions that sound unnatural for the person or organization they’re impersonating.
- Spear phishing emails may also contain files with unusual extensions that encourage you to enable macros, despite being fairly uncommon in day-to-day file sharing among colleagues.
- Always remember to hover over hyperlinks included in an email - this will be a good indication of whether you are being directed to a legitimate site or not
Spear phishing vs. phishing
The difference between phishing and spear phishing comes down to scope. In regular phishing campaigns, attackers cast a wide net and go after as many targets and companies as possible with relatively low-effort tactics. Spear phishing campaigns, by contrast, take aim at particular targets with the goal of breaching specific organizations, involving more careful research and preparation.
Mass phishing scams frequently involve using toolkits to set up false login pages for popular account services, from which bad actors harvest credentials, but these scams may also attempt to spread malware indiscriminately to users through malicious links and files.
Spear phishing campaigns often take a more nuanced approach. They can use falsified company documents infected with malware, or set up convincing credential theft sites to steal sensitive data and intellectual property or to breach payment systems. Attackers in spear phishing messages may also opt to use social engineering to manipulate users into transferring large sums of money.
Mass phishing attacks are becoming more sophisticated, as threat actors are able to host malicious documents on legitimate sites such as Box and Google Drive—as opposed to just sending them as email attachments. Some phishing attacks even attempt to exploit API and session tokens to access email and file-sharing accounts. But spear phishing scams remain more threatening to the average user than mass phishing, as the personal touch of these attacks makes them more likely to succeed.
What is whaling?
Whaling is a type of spear phishing attack that targets executive-level employees. In whaling attacks, criminals usually attempt to pose as C-suite figures to coerce a less senior victim into making payments or sharing confidential data.
For a few reasons, executive employees are more lucrative targets for scammers than junior staff members:
- They tend to have more access to funds and valuable information, making it worth the time invested in researching and writing targeted communications.
- Under the pressure of balancing many responsibilities, executives may also be more susceptible to opening a whaling email without detecting the subtle signs of a scam.
A similar kind of attack, known as a business email compromise, involves bad actors taking over senior-level business accounts and targeting HR teams. In these attacks, cyber criminals may pose as suppliers and request that invoices are paid to a different account, or, while impersonating an employee, try to convince HR to update their payroll details to the attacker’s account.
What motivates spear phishing attacks?
While some spear phishing attacks may directly extort targets for money, it’s more common for organizations to experience detrimental data loss as result of a breach. Proofpoint’s 2020 State of the Phish report noted that over 50% of the companies surveyed listed data loss as the most damaging result of a successful attack.
Data is a valuable commodity to many, meaning spear phishing attacks have various perpetrators. Hackers and hacktivists may work on behalf of governments to obtain intelligence for national or ideological interests, or may be affiliated with companies engaging in industrial espionage. Criminal organizations and lone cybercriminals may also devise spear phishing campaigns for their own ends, whether to resell confidential data to other sources or in preparation for further attacks on the target organization.
What are some spear phishing examples?
Organizations of all sizes and in any industry can become targets for spear phishing.
In perhaps the most high-profile case in recent years, volunteers and employees of Hillary Clinton’s presidential campaign fell victim to spear phishing attacks. The attackers successfully stole login credentials, which allowed them to further compromise the Democratic National Committee (DNC) network and steal documents, monitor employees, and spread malicious code. More recently, a spear phishing campaign has targeted aerospace and military companies in Europe and the Middle East.
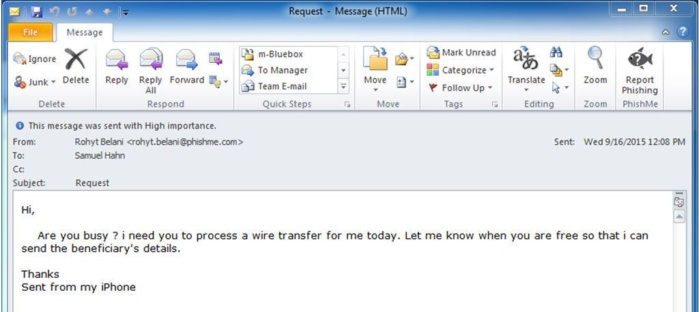
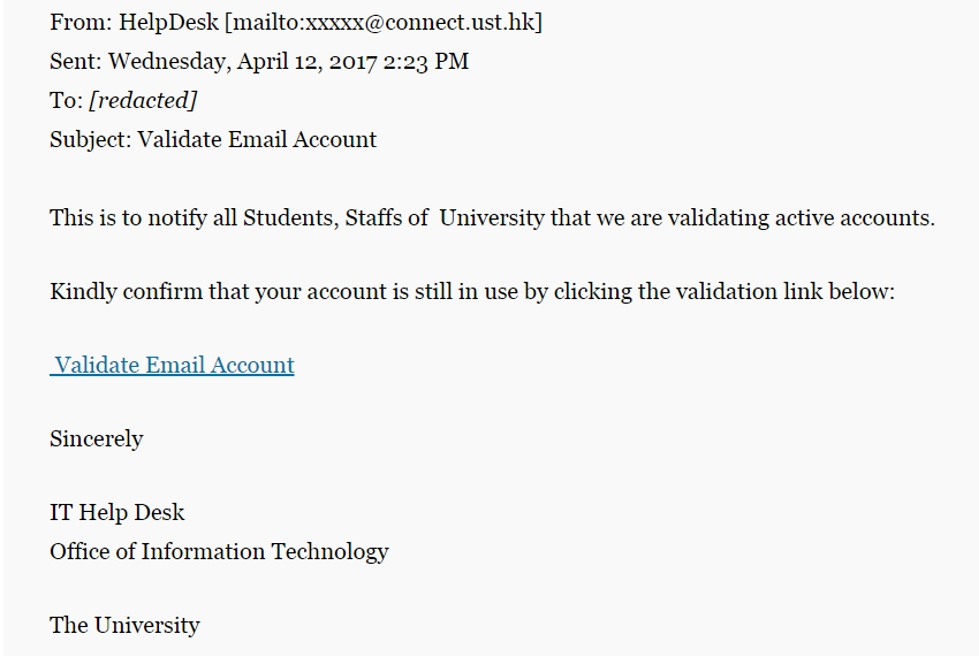
As seen in the spear phishing email examples below, targeted messages tend to feature a few telltale signs:
- Email domains that don’t match the user’s name or purported organization
- Grammatical and terminology inconsistencies
- Situations of urgency and secrecy—e.g., same-day money transfers.
Source: CSO Online via Cofense
Source: Proofpoint
What tools do cybercriminals use for spear phishing?
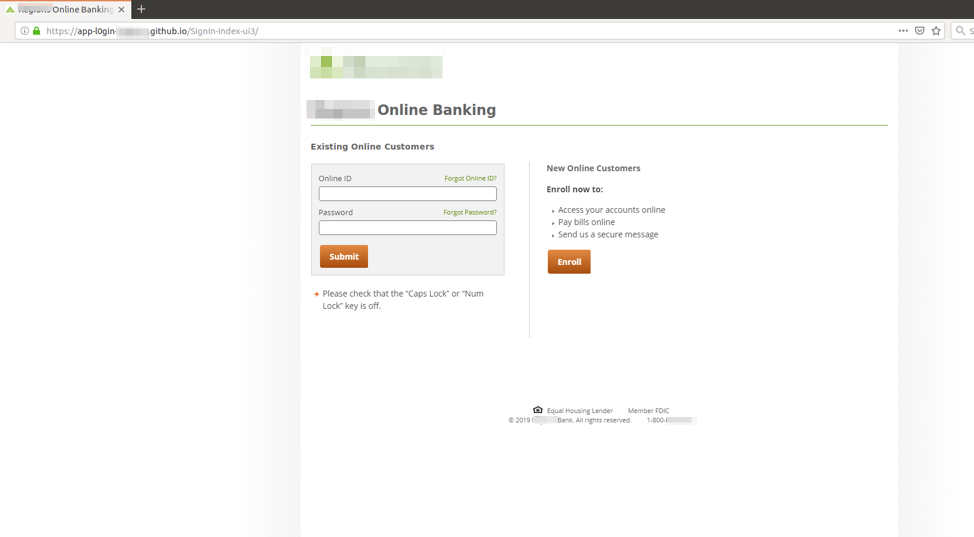
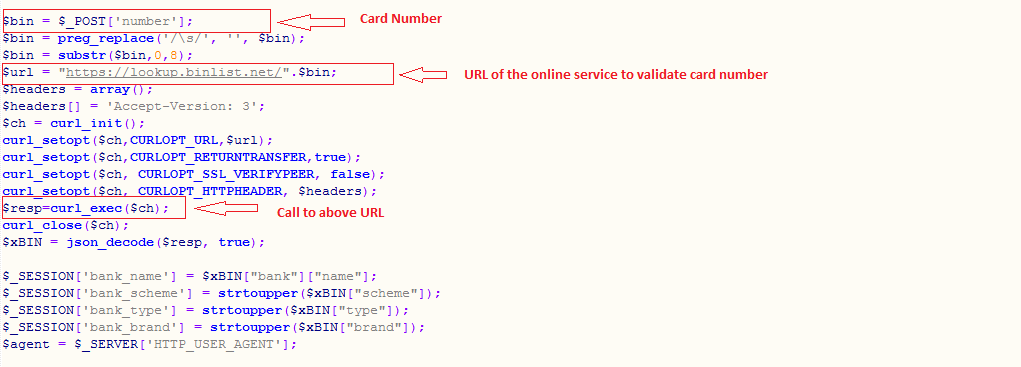
Many phishing campaigns will use toolkits to convincingly replicate the legitimate websites of banks, email providers, and other account services. Phishing kits are essentially the backend to an attack—a fraudulent website built on basic code, made with just enough effort to sway victims into sharing their credentials and other data.
Source: Proofpoint
Source: ZScaler
More sophisticated attacks may involve advanced phishing kits, including tools that scrape social media profiles for information to help bad actors personalize their messages. However, spear phishing often comes down to emotional manipulation—how effectively cyber criminals can convince targets to click a link, download a file, or send over financial details and other prized information. For that, attackers rarely need more than an email account and a basic toolkit.
Why is spear phishing effective?
Spear phishing plays on the human psyche. When attackers use detailed levels of personalization, strike a convincing tone, pose as superiors, or present the target with an emotional or urgent cause, they exploit our natural tendencies to trust others, comply with authority figures, and solve problems.
Bad actors also make efforts to deceive security systems. Spam detection systems struggle to filter out phishing messages that convincingly imitate business emails, and cyber criminals can get around blocking lists by sending legitimate emails and traffic for a period of time, making their IP addresses and email domains appear trustworthy.
How to prevent spear phishing
Knowing how spear phishing works is the first step in securing your company against attack. With a primary goal of limiting your attack exposure, here are some tips to protect your organization:
- Reduce your attack surface. This can include confirming financial transactions and account changes over the phone, ensuring payments go through multiple steps of internal approval, and establishing a process for users to report suspicious emails.
- Offer active education. Issue phishing simulation tests to identify staff who need security training, and run periodic sessions with the whole organization to keep phishing awareness top of mind.
- Promote online privacy. Successful spear phishing starts with research—encourage your teams to change their social media privacy settings to limit what others can see.
- Be critical. Establish a baseline process of confirming directions before clicking on links. Encourage teams to speak in person to corroborate anything that feels off.
- Tag all out-of-organization emails as “external.” This simple step can let your teams have a visual cue in their email subject lines that they should take a second look at the email’s contents.
- Leverage protective software. Stay up to date with the most effective software for malware and antivirus protection, data loss prevention, and multi-factor authentication.
Getting your organization aligned on spear phishing protection is an ongoing process—but one that can save you money and time down the road. With preparation and vigilance, your teams can present less of an easy target.
Spear phishing is one of five identity attacks that exploit password authentication. Check out our whitepaper to learn about the other four.