Demo: Active Directory Integrations
Transcript
Details
Speaker 1: Many Okta customers, especially the larger ones, use AD as their data store. Fortunately Okta can easily connect to an AD domain that's behind a firewall. It doesn't matter how complex the environment is. Whether you have a single domain, multiple domains, untrusted domains, or multiple forests, you simply install an AD agent in that network and you don't need to make any firewall hold or network changes. Let's see how easy this is.
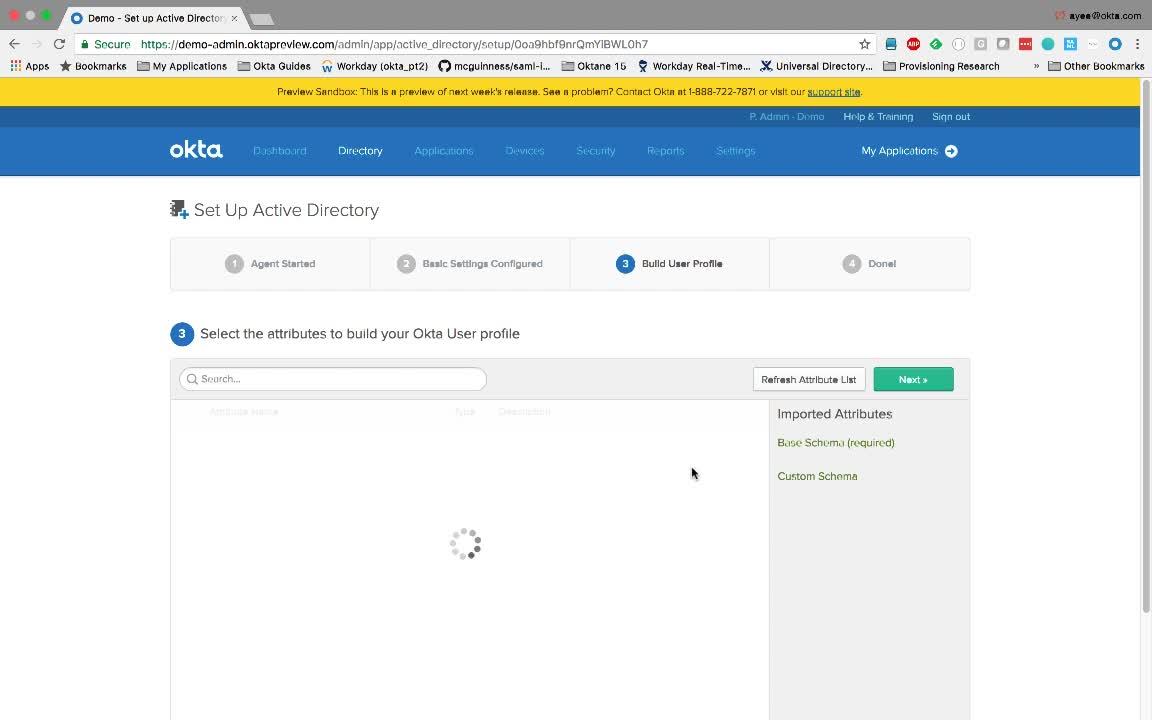
Speaker 1: Within Okta, you'll see here that I don't have any directories set up. I've already gone ahead and clicked on this Add Active Directory button which downloaded the agent to my desktop. Let's go ahead and set this up in my virtual machine. Okta is now asking me to authenticate and authorize this agent. I've now installed the agent. Let's go back to Okta and finish the configuration. First Okta asked me to identify the OUs from which I'd like to import the users and groups from, and it also asks me to select an Okta username format. I'll stick with the defaults.
Speaker 1: Next Okta asked me to identify the attributes that I would like to import from Active Directory. Again, I'll stick with the defaults. I'll go ahead and make a few more changes that automatically confirm and activate new users. Before we import users and groups, let's discuss how Okta provides ultimate flexibility with two deployment models. The first is called Just In Time or JIT Provisioning, and this is good for creating user accounts on an on demand model. It's tailored for large directories. The second model is called scheduled imports and this brings in new user accounts, deactivated accounts as well as updates on a scheduled basis. I'll go ahead and click Save.
Speaker 1: Okay. Let's go ahead and run an import and see how the group can be used in Okta. So, Okta has brought in new users and groups. And let's confirm this. We're interested in a group called HR Application. We see here that Okta imported that group, and it has two users in there. We will now assign this group to a popular HR application called Workday. Doing so will grant users in the group single sign on access to this application. We've granted access and the users can now access the application. In Okta, groups are also commonly used to do a number of other things. They can be used to set app entitlements, and as you can see here, they can be used to set password policies, sign on policies, multifactor policies, mobile configurations, and WIFI configurations. It's easy to configure, yet quite powerful.
Discover how to effectively use Okta’s Active Directory integration, including using AD as a data store and being able to access it behind a firewall. Learn how the admin gets linked to the directory instance, and how the application group can be used to enable access for users in that group.