The (Security) Times, They Are A-Changin’ – Make Way for MFA and the New Security Era
Three years ago, a WIRED cover story declared the password dead. This was just after the famous personal identity hack of the reporter, Mat Honan.
"Today, nothing you do, no precaution you take, no long or random string of characters can stop a truly dedicated and devious individual from cracking your account," the article explained. "The age of the password has come to an end; we just haven't realised it yet."
Fast forward three years and, yep, we have realized this new era of security. Many companies fell victim to data breaches since that 2012 WIRED cover story, and security has quickly risen to the top of businesses' minds. It's become crystal clear that passwords alone are not enough protection.
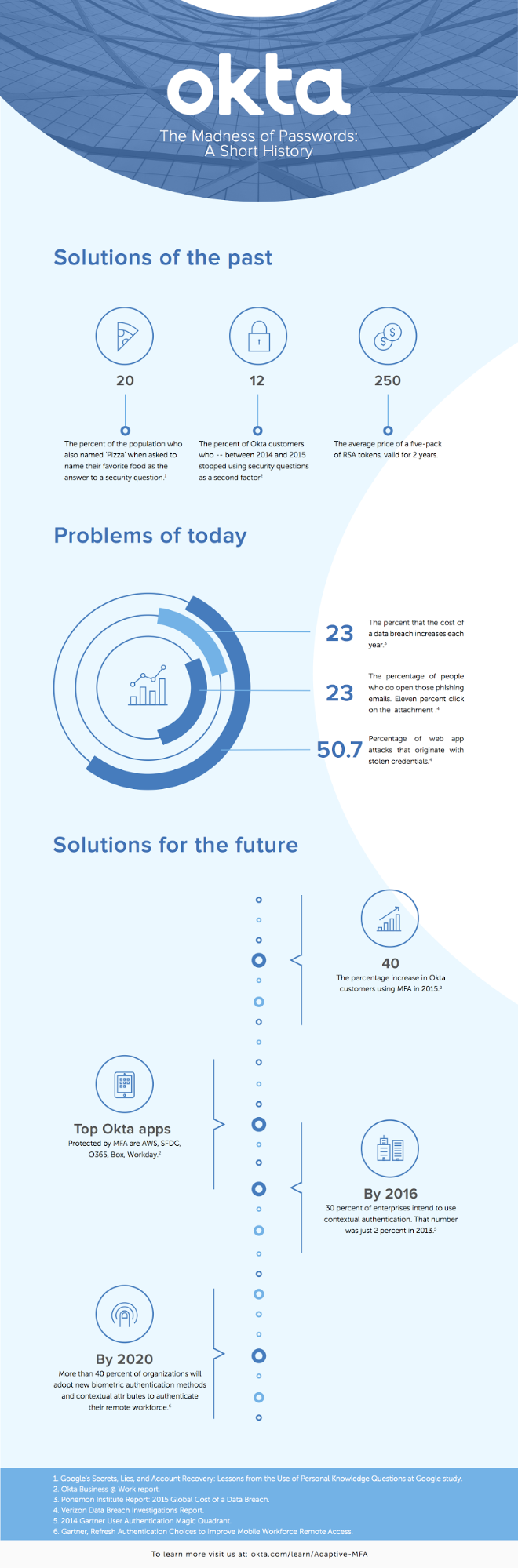
In fact, 51 percent of top executives are concerned about security as a challenge in adopting digital technologies. And they're doing something about it: As our Businesses @ Work report found, the classic "security question" (What's your mother's maiden name?) is becoming less and less popular as a form of verification, dropping 14 percent since April 2014. We've also seen a 40 percent increase year-over-year of companies moving to protect their apps with MFA.
If the WIRED story got anything wrong, it's the myth that you need to make a tradeoff between convenience and privacy. At Okta, we believe strong security doesn't have to come at the expense of great user experience, as long as you have the right tools in place – including MFA to protect your apps and corporate assets.
There are four key ingredients to a security environment that's both effective and convenient for users:
Contextual access: Access policies should allow, restrict, require step-up authentication, or deny access based on the user, device and other considerations like network, location or type of application. For example, a company should automatically require step-up authentication if an employee requests access from a device they've never used before.
Wide selection of second factors (that people actually want to use): Encourage easy, secure access for everyone by offering user-friendly factors like push notifications, SMS, and hardware tokens like YubiKey.
Proactive protection: Data-driven proactive security is the best kind of security. By controlling access based on historical user behavior, organizations can detect suspicious activity and also avoid unnecessary verification prompts. For example, there's no need to require a remote employee to verify his identity every day from his home office – but it is wise to prompt for MFA if he or she logs in from a new remote location.
Integration with all apps and VPNs: For ultimate security, integrate with a broad set of apps and network infrastructure – both cloud and on-premises – to centrally enforce MFA and protect applications that don't natively support second factors. Data breaches cost an average of $3.8 million, so eliminate all coverage gaps to reduce your chances of getting hacked.
An IT environment that's not only secure, but also user-friendly? You can have it all. Learn more here: https://www.okta.com/au/learn/adaptive-mfa/.