Securing Office 365 in 3 Easy Steps
Five months is a long time in the business world—never mind five years. That’s why it’s so impressive that Microsoft’s Office 365 has consistently ranked as the #1 application in our Businesses @ Work Report. It’s now 2020, and Office 365 is still the most popular workplace app by a large margin.
Unfortunately, that success doesn’t come without risks. As Office 365 has become a fixture of modern workplaces, cybercriminals are increasingly determined to compromise it. By breaching Office 365 in one organisation, they believe they’ll open the door to hundreds of others—making the app an important threat vector to secure.
Securing your Office 365 starts with 3 steps
Hackers have a vast toolkit of tactics they use to breach an organisation’s networks, but phishing is the most common approach when it comes to compromising Office 365 accounts. In fact, 56% of new application users are targeted by phishing attempts—and these attempts often work. That’s why it’s so critical for companies to protect their users and their data, without compromising user experience. Here’s how:
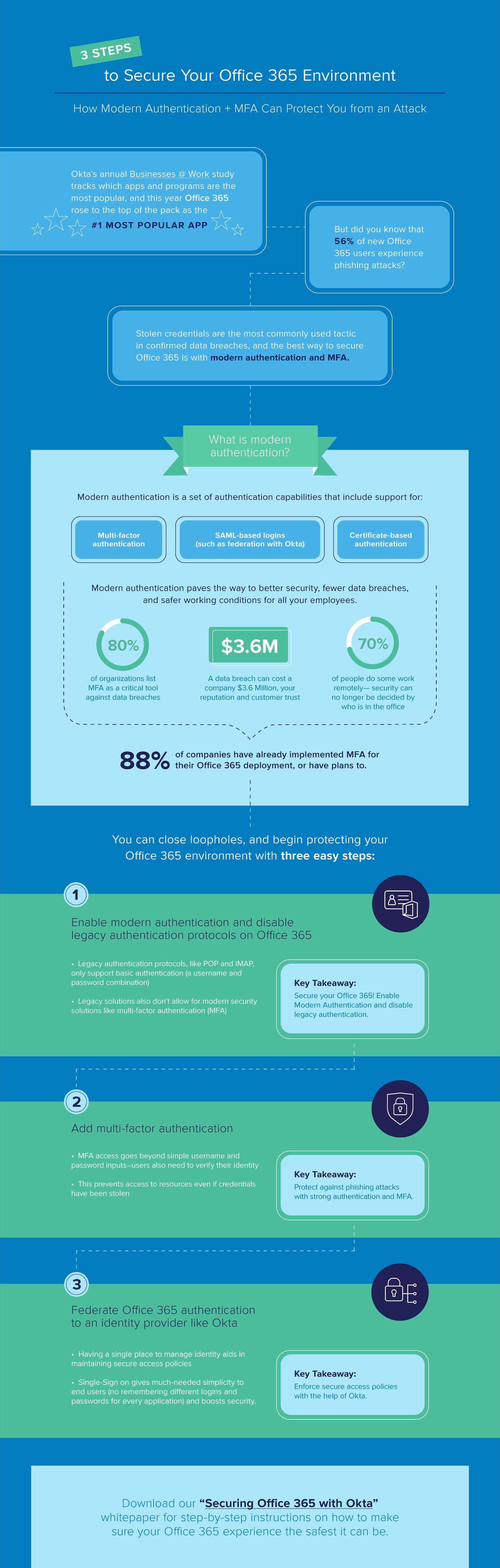
We should point out that Office 365 accommodates several different authentication methods and protocols, and not all of them support MFA. If Office 365 is mission-critical to your operations, it’s best to take a holistic approach to defend it. This can include disabling legacy authentication in favor of modern solutions, federating with an identity provider like Okta to enable SAML-based logins, and adopting additional measures such as SSO to eliminate the threat of bad passwords.
A detailed look at defending your Office 365
Threat actors are constantly refining their attack methods—and we’ve come up with ways to close your security gaps around Office 365. For best practices, check out our Securing Office 365 with Okta whitepaper here, and find out how you can stop cybercriminals in their tracks.

