The Ultimate Guide to FIDO2 and WebAuthn Terminology
In March 2019, the World Wide Web Consortium (W3C) announced that WebAuthn is now the official web standard for password-free login. With support from a broad set of applications (Microsoft Edge, Chrome, Firefox, Mobile), widespread adoption of WebAuthn is expected in coming years. In a previous blog post we went through some examples of how WebAuthn can benefit your customer experience as well as strengthen your security posture.
In this blog post, we will explore some of the critical technical building blocks and protocols that helped achieve the new standard.
What is FIDO2?
FIDO2 is a project that was executed by the FIDO Alliance and World Wide Web Consortium (W3C). The standard itself consists of the W3C Web Authentication (WebAuthN) browser API standard and the FIDO Client to Authenticator Protocol (CTAP). FIDO2 builds on previous work done by the FIDO alliance for the Universal 2nd Factor (U2F) authentication standard.
FIDO2 represents the building blocks to go beyond basic log-on and specifically the first strong authentication standard for the web.

What is CTAP?
CTAP or Client to authenticator protocol enables FIDO2-capable devices to interface to external/roaming authenticators over Bluetooth, USB or Near field communication (NFC).
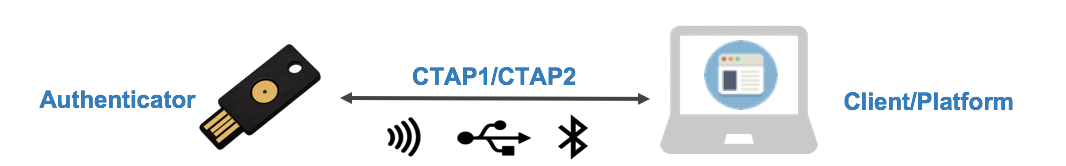
CTAP enforces a secure device-to-device authentication channel. The device to device communication is typically between a user owned cryptographic roaming authenticator — such as a smartphone or a hardware key — and a client platform such as a laptop.
This CTAP protocol is used in scenarios where an end-user interacts with a relying party (a website or a native app) on some platform (e.g Mac) which prompts the user to interact with a roaming authenticator (e.g a smartphone).
CTAP1 is an older standard where the external authenticator is expected to be able to provide the second factor of authentication. CTAP2 allows the external authenticator to be used as both a first and second factor of authentication and eliminates the dependency on passwords.
What are authenticators?
The authenticator is a device that, when needed, is able to obtain a user gesture such as a password or biometric input among other functions.
Going one layer deeper, a platform authenticator is an authenticator that is integrated with a device such as a laptop. As a virtue of being tightly coupled with a device, they do not need a secure transport protocol such as USB, NFC or Bluetooth to obtain the user gesture. Common examples of platform authenticators include TouchID, FaceID, Windows Hello etc.
A roaming authenticator is a portable authenticator that can connect to any laptop over a secure transport protocol. These authenticators must support the CTAP protocol. Common examples of roaming authenticators include YubiKeys, Bluetooth-enabled smartphone applications, etc.

A comprehensive list of FIDO2 authenticators is maintained on the FIDO alliance website.
What is the role of browsers?
A WebAuthn supported browser must be able to perform the following functions:
- Compose messages for operations
- Process extensions
- Provide User interface for authenticators that lack the ability
- Manage error handling and housekeeping
Most modern browsers already support the WebAuthn API. Here is a handy list of browsers that support the standard.
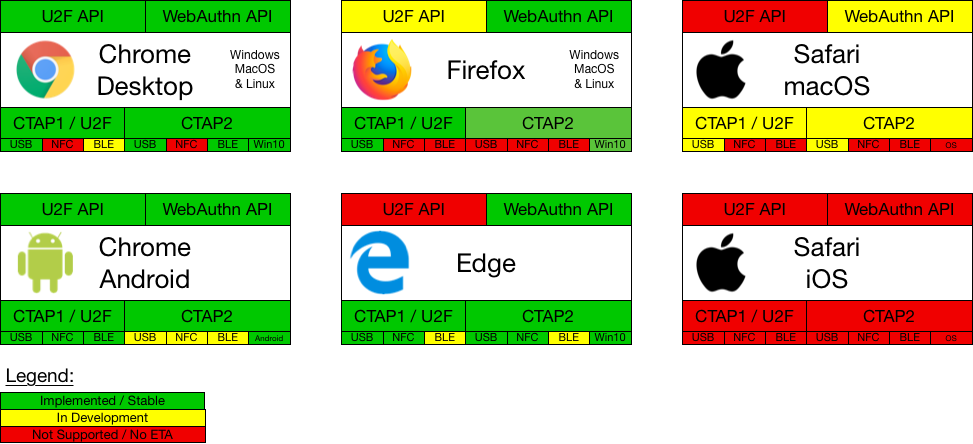
Image Source: https://github.com/apowers313/fido2-webauthn-status
What are relying parties (a.k.a) web server?
Relying parties are applications that can authenticate using strong credentials presented using the FIDO2 standard. Depending on the type of application, the webauthn client can be the native application that makes the webauthn call. Or it can be the web browser that brokers the call.
What are U2F and UAF ?
Universal 2nd Factor or (U2F) is an open authentication standard that strengthens and simplifies two-factor authentication using specialised USB or NFC devices and is built using the standard public key cryptography.
Universal Authentication Factor (UAF) is a framework to replace passwords for primary authentication and is a true passwordless experience.
With Both UAF and U2F, the web service requests authentication with a local device, and the web service then accepts this authentication and allows the user to sign-in.

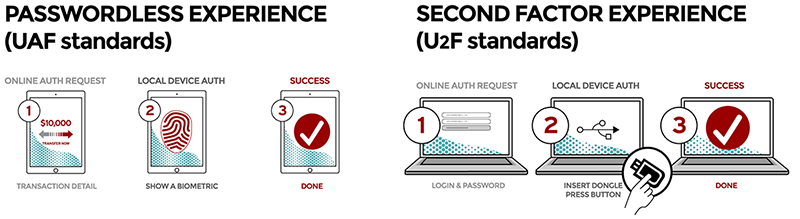
Image Source: The FIDO Alliance
What’s next?
Now that we have explained some of the basic terminology, check out the next post in this series exploring what the user registration, authentication and account recovery flow looks like. In the meantime to learn more check out the session below from Oktane19, which goes into depth explaining Webauthn.

