5 Reasons You Want an Out-of-the-Box Identity Service
Whether you’re building a new app or migrating a legacy app to the cloud, you face a choice: build everything in-house or selectively use out-of-the-box services to make the job easier and faster.
Out-of-the-box services like Twilio, for messaging, and Braintree, for payments, have gained popularity because they help lean dev teams remain agile and keep operational costs down.
While easy to overlook, identity and access management is a huge potential pitfall that can slow down release dates as much as 6 months or more. In addition to product launch delays, poorly built access management leads to the security vulnerabilities and the bad customer experience stats shown below.

For this reason, there’s significant value in using a secure identity service to manage customer identity and access management. Any third-party solution must be both secure and developer friendly so that organizations can avoid these pitfalls.
In order to gauge the value of going with a solution vs. building internally, here are 5 modern auth challenges that must be overcome when building internally.
1. The basics have become complex
At a very high level, identity and access management has three parts: authentication, authorization, and user management. Before, the move to modern app development auth was much more simple: customers could login or register with a straightforward form submission.
Their user information was stored in Active Directory or an LDAP system, and the app handled authentication and authorization internally.
However, the trend towards API-first app development, microservices, and continuous delivery has decentralized access management. Orgs now require a secure identity layer to operate in the cloud in order to deliver seamless experiences to customers.
WS-Federation and SAML are no longer the go-to standards for single sign on (SSO) experiences. Therefore, orgs must hire or train their devs on new standards like Oauth 2.0 and OIDC. It is becoming increasingly common for projects to grind to a halt around issues with identity.
2. The bar for customer experience is sky high
For many enterprise organizations, it is no longer enough to build better experiences than traditional competitors. Customers demand the same high quality, seamless, and secure experiences they enjoy from the tech giants like Netflix, Amazon, and Google.

This means building seamless auth experiences across channels, which requires a single access layer. In addition to having a 360-degree view of the customer, you need many capabilities including: SSO support, customer data partitioning, token authentication, multi-factor authentication, social login, passwordless, progressive profiling, LDAP/AD integration, and application security.
3. More digital experiences means a wider attack surface
User data breaches are public, and incredibly expensive in terms of monetary penalties and brand damage. Applications have become key targets because they are a treasure trove of personally identifiable information (PII), and sensitive data like social security numbers, credit card numbers, medical records, and more.
Development practices often outpace the capabilities of security. For example, orgs rarely have mature API security programs—even though 95% plan on investing in APIs in the near future.
Making matters worse, customers are notoriously bad at protecting themselves, often reusing passwords for more than one site. If you try to solve those problems with security measures that are too restrictive, users will face too much friction.
Finally, standards keep changing. It was long thought that strong passwords were preferable. Passwords that were simple (ex: short, no special characters, and numbers) are easier to guess using automated programs, such as bots. But that thinking is changing due to the correlation between strong password policies and rampant password reuse.
Today, simple passwords with a second factor are preferred to strong passwords with no second factor. However, SMS verification falls in and out of favor. Biometric factors are great for some people, but others aren’t comfortable having their biometric data on the internet.
4. The best ability is availability
Customers need to be able to get access regardless of the load on the application. The user management backend database must not only be secure, but also highly available, otherwise the application breaks and the customer experience is ruined.
The challenge facing enterprises that are less mature in their cloud strategy is the lack of expertise in building effective high availability systems. Outages are more likely to occur while at the early end of the cloud maturity curve.
5. Someone has to account for scale
Once apps go into production, one of the biggest challenges is predicting load. It’s common for applications to become victims of their own success and go offline due to unpredictable popularity. Authentication and password encryption can be very resource intensive, putting undue pressure on systems during times of heavy usage.
Companies must consider the loads across their various production, QA, development, continuous integration, and disaster recovery environments. At the same time, they must buffer for overprovisioning, which unduly drives up costs and impacts ROI. High volume applications can require dozens (if not more) servers just to handle user management.
A secure identity service
Building auth internally comes with significant pitfalls that can increase time-to-market, costs, and risks. However, there is a way to support lean development, launch seamless customer experiences out of the box, and improve security without unnecessary end-user friction.
Okta provides a digital identity layer comprised of APIs, SDKs, and out-of-the-box customizable components. We serve as building blocks to increase speed-to-market, lower development costs, and focus in-house developers on the core features of the application.
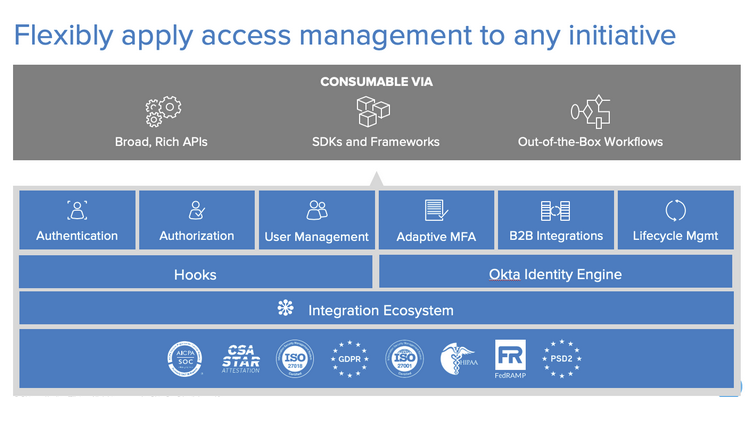
With a secure identity service, developers are freed up to spend more time on core functionality and less time on security. Plus, it’s easier to launch applications that are secure out of the box. Customers can have seamless experiences, they engage more, and your project realizes greater ROI.
To learn more about the advantages of a modern identity solution, including a cost benefit analysis, download this white paper: Build vs. Buy: Key considerations and the advantages of a pre-built identity.

