How Okta + AWS SSO Simplifies Admin and Adds CLI Support
Millions of users across an array of enterprises depend on the cloud infrastructure of Amazon Web Services (AWS) and the seamless convenience of Okta Single Sign-On (SSO) to power their web and mobile platforms. The demand for cloud-enabled identity and access management (IAM) has exploded across the business landscape. And as organisations move more of their business online, there is an exponentially growing need to securely and seamlessly connect a global workforce to virtual workspaces.
A large number of AWS customers already use Okta to securely authenticate their users. This integration is one of Okta's Top 3 apps according to our 2020 Business@Work Report. Okta monitors data to see which apps in the Okta Integration Network are most popular among our users, and as other apps rose and fell over the last three years, AWS has consistently remained in the top three.
But larger, complex organisations may find it challenging to administer identities within their AWS environment; specifically, when the organisation has many AWS accounts and sophisticated permission sets. For enterprises, IT admins are the ones asked to quickly provision users and groups to AWS IAM roles and accounts. This task can be challenging because it requires expertise, and time-consuming because it is a manual process. Moreover, this task continues to grow in complexity as work shifts to home, and the number of identities and projects multiply.
We heard you, and are happy to announce a new integration with AWS SSO! This update supplies deep support for AWS organisations through a new AWS capability explicitly designed to solve this problem. With this release, Okta end users get the convenience of the sign-in experience they know from Okta with single-click access to assigned AWS accounts. For administrators, this makes it easier to get started granting AWS access to your existing Okta users and groups, and simplifies AWS multi-account access management through AWS SSO permission sets.
See how Okta integrates with the new AWS SSO portal in this quick demo:
What’s new + benefits of the integration
One-click access from Okta to all of your AWS resources
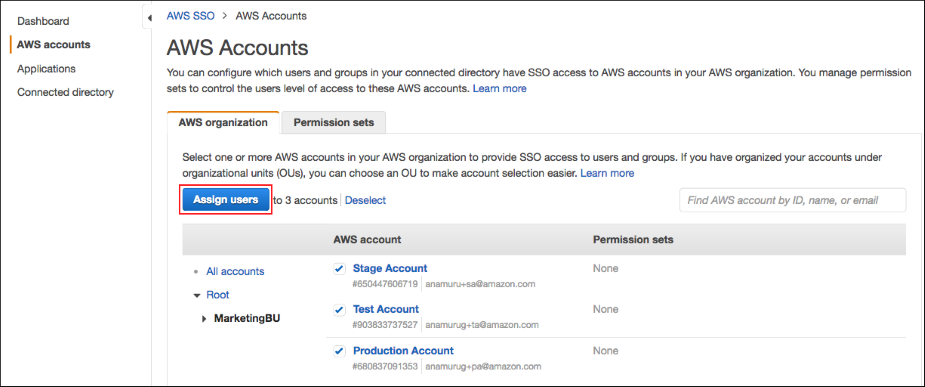
Customers can now connect Okta to AWS SSO, providing a user portal to access all their assigned AWS resources. By federating Okta with AWS SSO, end users can sign-in to AWS SSO with a single click. This seamlessly maps those authorised users into the appropriate AWS accounts and resources (e.g., Amazon EC2, Amazon S3) managed by the AWS Management Console, as shown below.
Centralised management of permissions in AWS SSO
With AWS SSO, customers can centrally manage fine-grained authorisation to access AWS accounts and resources. AWS admins can create flexible permissions, aligned with roles and projects, and assign them to users and groups. This frees up the administrative burden of requiring setup in each individual AWS account.
For example, you can give your security team administrative-level access to your AWS accounts running your security tools, but only grant them auditor-level access to other AWS accounts for monitoring purposes.
By centrally managing users and groups in AWS SSO, AWS admins will have full visibility of who has access to what in every AWS account, and when those permissions were assigned. This helps your audit and compliance teams meet your internal and regulatory compliance requirements. It’s a win-win-win: Enterprise teams get the secure, frictionless access to cloud infrastructure, IT managers reduce the time-consuming nature of manual provisioning into cloud infrastructure—and your enterprise assets stay safe.
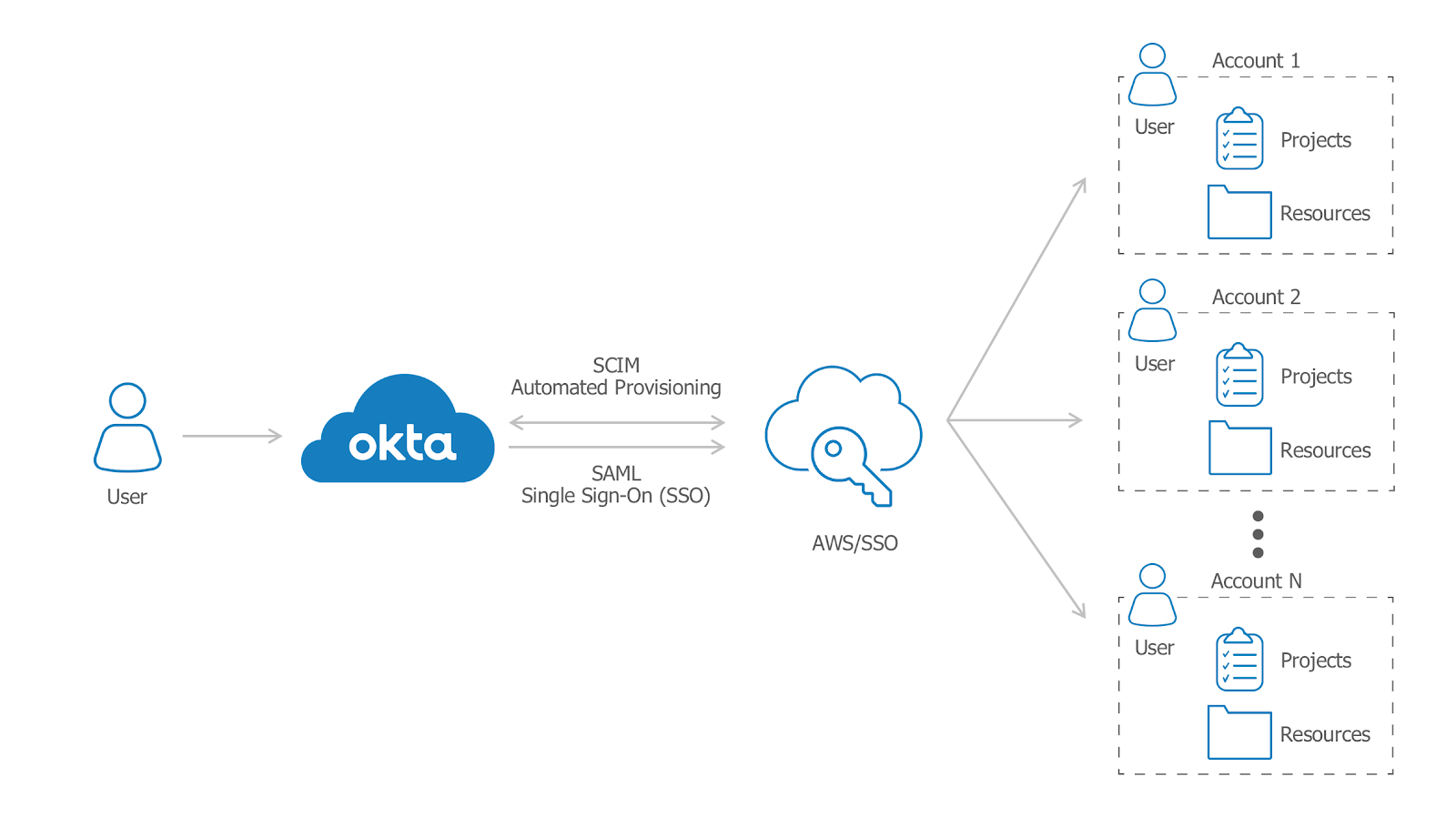
Automated provisioning with Okta Lifecycle Management
With Okta Lifecycle Management (LCM), users can be automatically synchronised between Okta and AWS. Additionally, using the Group Push feature, existing Okta groups and their membership can be pushed to AWS SSO. This means as users are onboarded in Okta—including those mastered from an HR system or through an existing directory integration—they’re simultaneously provisioned in AWS SSO. This, in turn, assigns access to specific AWS accounts and resources, based on permissions sets mapped to that user’s group membership.
For example, imagine a user is in a particular Okta group who’s been assigned permissions to manage a particular Amazon EC2 instance is later removed from that group. Thanks to the deep Okta + AWS SSO integration, that person, on removal from the original group, would instantly and automatically lose permission to manage that EC2 instance as well. No lag, no IT admin followup necessary, no outstanding security risk of an unauthorised user retaining access to group AWS resources.
Frictionless, Streamlined Developer Experience Through CLI
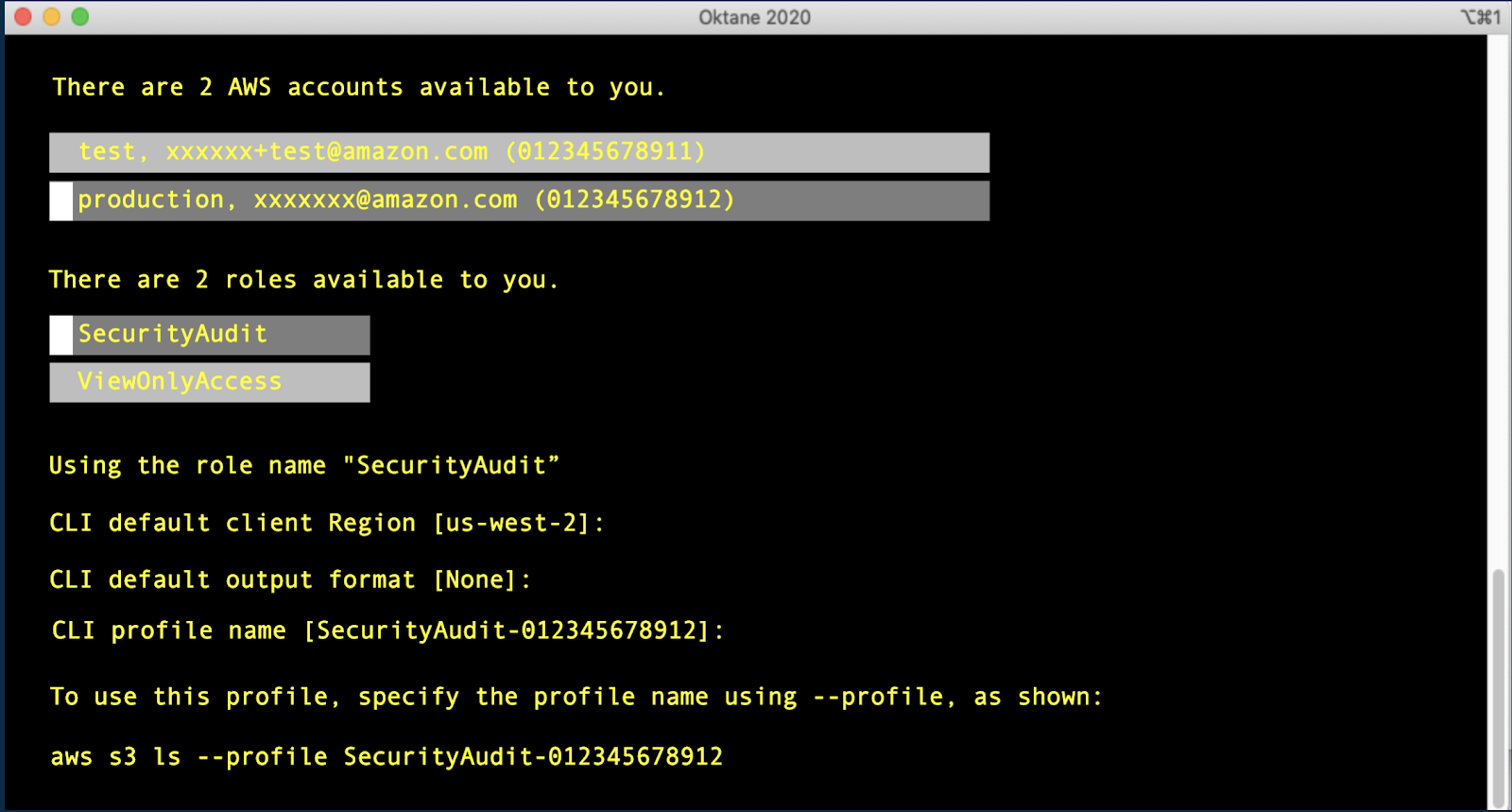
Developers will also benefit from the efficiencies of the increased support for the AWS Command Line Interface (CLI) in the AWS SSO integration. The AWS CLI is a powerful tool that enables developers and DevOps teams to manage multiple AWS services and automate commands via scripting. With the Okta and AWS SSO integration, developers can now sign-in with their Okta credentials and Okta Multi-Factor Authentication (MFA).
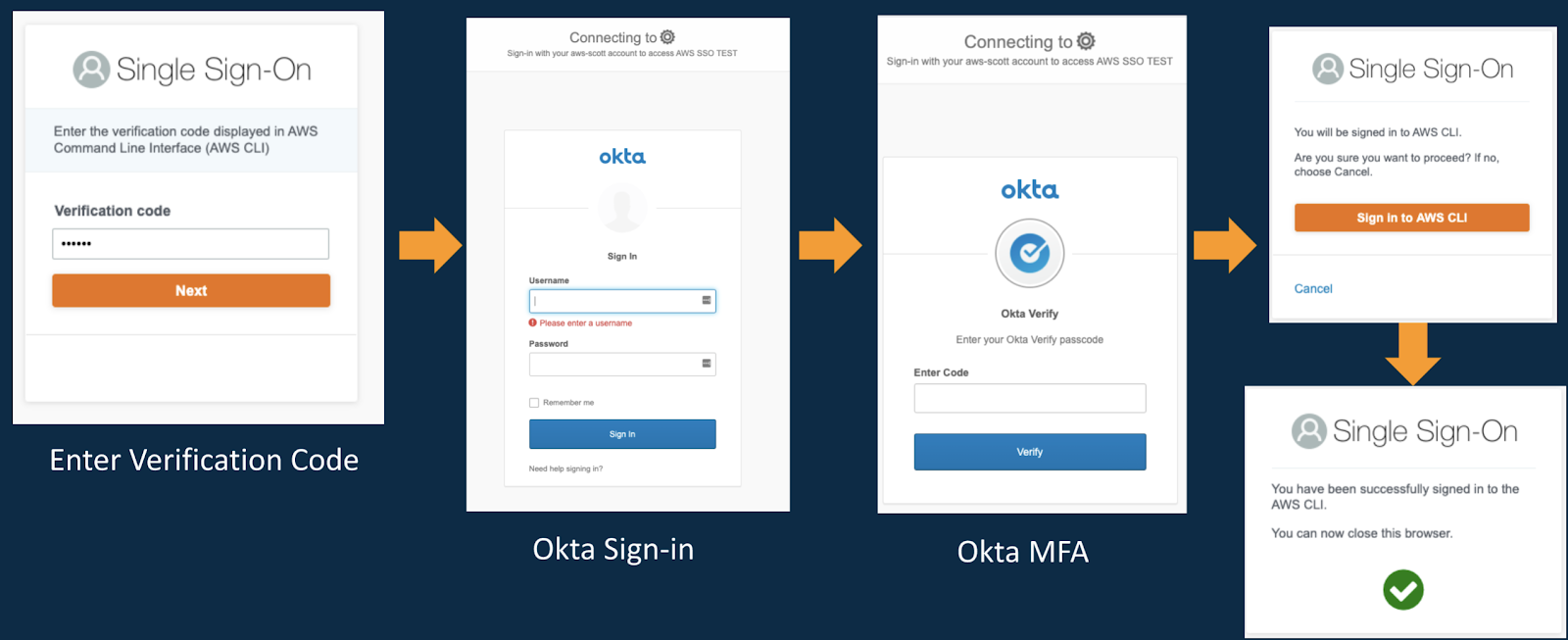
With AWS CLI v2 support for AWS Single Sign-On, this means that AWS CLI profiles can be linked to AWS SSO accounts, allowing Okta to act as the external identity provider. This gives developers a secure and seamless Okta login experience, quickly getting them in to focus on building apps. The process is simple:
Step 1 - Initiate SSO authentication from CLI
Step 2 - Sign-in with Okta credentials + MFA
Step 3 - You’re authorised to AWS accounts and roles!
Want to learn more?
At Okta, we’ve always prided ourselves on providing modern identity solutions that are simple, secure, and easily integrated with the platforms and applications our customers use—and we never stop innovating our solution set. This integration deepens an already strong and seamless connection between the Okta Identity Cloud and AWS, helping us continue to deliver on that promise for all our joint customers.
To learn more, please see the following detailed configuration guides:
How to configure SAML 2.0 for AWS Single Sign-On
How to setup automated provisioning for AWS Single Sign-On
Configuring the AWS CLI to use AWS Single Sign-On
You can also visit the Okta-AWS webpage. Or simply click here to get in touch with our team.