MFA Trends: The Impact of COVID19
The COVID pandemic has changed how we do many things. In the workplace, it’s pushed us to take a deeper look at how we enable employees to work remotely—and to ensure that they can do it securely.
But what does that actually look like? According to our recent Businesses @ Work (from Home) report, companies are adapting and evolving quickly. Alongside the rapid adoption of collaboration and network security tools, our customers are also increasing the use of multi-factor authentication (MFA) to better protect access to their resources. And while we applaud those efforts—some MFA will always be better than no MFA at all—we want to ensure that you’re setting up your workforce for success with the most secure options.
To help you make those decisions, this post will break down some of the trends we’ve seen this year—both before and during the pandemic—and offer suggestions on how to deploy MFA for your organisation, so that your technology can keep you safe.
What we’ve seen in our data
Every year, our annual Businesses @ Work report takes a comprehensive look at how organisations and people work, and the applications and services they use to be productive. We review data generated by our over 7,400 customers as well as the 6,500 integrations on the Okta Integration Network (OIN) to identify yearly trends.
This year, our report featured a chapter on how customers are using MFA. In an interesting shift, it outlined that customers are starting to focus on quality over quantity when it comes to MFA factors. For the first time ever, we’ve seen a decrease in the number of factors deployed, with many companies just deploying one to three factors on top of passwords.
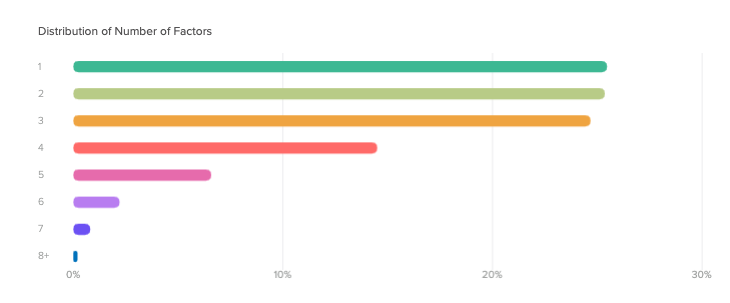
At the same time, our customers are more often opting for stronger factors like Okta Verify and Google Authenticator, which are much harder to compromise compared to factors like SMS. While SMS authentication is still popular—largely because it’s easy to deploy—it’s particularly susceptible to mobile security threats and simple hacks like unauthorised SIM swaps and interception. Despite its ongoing usage, we were pleased to see that SMS adoption is on the decline. In the last two years, it dropped from 56% to 51%. In the same time, security questions have dropped from 22% to 17%, leaving space for more secure alternatives.
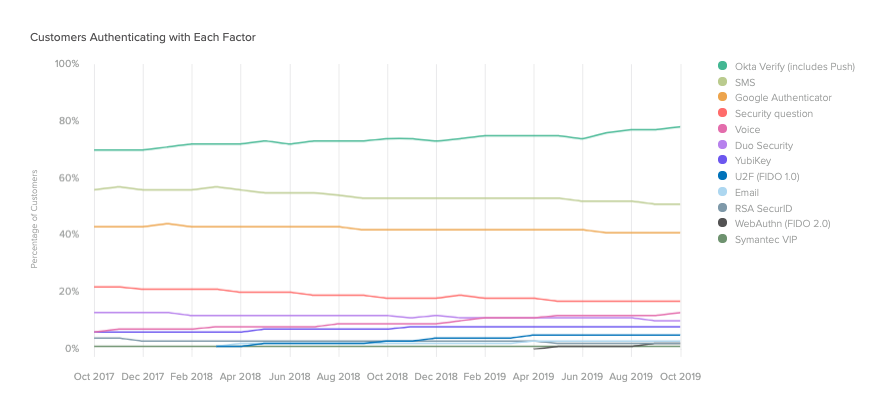
These trends were largely driven by new customers deploying authentication at their organisations.
How COVID-19 has impacted MFA usage
But the story doesn’t end there. In April 2020, we published a remote work version of our Businesses @ Work report that put the spotlight on how organisations across various regions and industries have responded to the effects of the pandemic. One of the biggest trends we identified was the increase in unique users accessing collaboration tools like Zoom and Cisco AnyConnect, as well as network security tools like Palo Alto Networks GlobalProtect and Citrix ADC.
We also saw significant growth in MFA authentications across the board. On the one hand, we were pleased to see that Okta Verify (including Okta Verify with Push notifications) saw the biggest uptick in unique users authenticating with it every day. By the end of March, it was hovering at approximately an 80% increase in usage compared to 28 days prior.
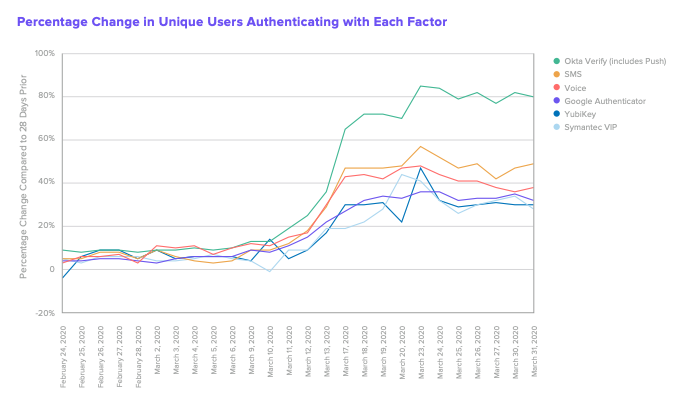
However, we’re seeing a similar growth trajectory with other, less secure factors as well. Despite its vulnerabilities, SMS is seeing increased usage of approximately 50% to four weeks prior. We suspect that this usage increase originates from organisations trying to rapidly adapt to a distributed workforce, and opting for an authentication option that is quick and easy to deploy. But this method may be riskier than ever before, as hackers are capitalising on COVID-19 to try to compromise users and their sensitive information.
Navigating rapid change
Threat actors are employing social engineering attacks to try to take advantage of people by using messaging and ploys around health concerns, stimulus payments, brand campaigns, and more. There have also been numerous phishing attempts made within organisations, referencing changes to work policies and sharing dubious links that could contain malware. These threats are driving the need for strong, secure authentication factors that can better ensure that only the right people have access to the right resources in your systems—and no one else.
Our customers are continually proving to us that they are leaders in their fields by responding rapidly and effectively to this crisis. We know that sometimes that means choosing the easiest and fastest solution so that you can address a problem quickly. Over the coming months, however, as you and your organisation settle into your new state of operations, there may be an opportunity to invest in stronger factors that can better keep bad actors at bay.
As you continue to make these changes, we’re here to help. Look out for part two of this blog series, where we’ll discuss other MFA pitfalls to avoid, best practices, and an in-depth guide to deployment. For more information, check out the following resources:

