Desktop password sync: Unlock the benefits of platform SSO for macOS
The rise of Zero Trust architecture has brought new challenges to the table. With a Zero Trust approach, it's no longer sufficient to simply trust that a user's credentials are valid. Organisations must also verify the device itself to ensure that it meets their security standards.
One key way to address this challenge is by enabling device login using credentials validated by the organisation's Identity provider. This approach would allow users to log in to their devices using their organisation’s credentials, consolidating passwords and enhancing both the user and admin experience.
With macOS Ventura, Apple introduced Platform SSO, which enables developers to create a single sign-on (SSO) extension that interacts directly with the macOS login window. This extension enables users to link their local macOS account with their Identity provider through a simple, Mac-native workflow. Okta has led the way in adopting this with the upcoming Desktop Password Sync feature under the Okta Device Access offering, allowing users to authenticate themselves using their Okta credentials directly from the macOS login screen.
Desktop Password Sync not only synchronises the local macOS account password with their Okta password but also enrols users to Okta’s phishing-resistant and passwordless authenticator, FastPass. With Okta FastPass, users can now experience passwordless authentication to their organisation's resources using biometrics.
The current state of access management on macOS
The current state of access management on macOS presents several challenges for organisations. With local accounts, it's often difficult to ensure that users are following best practices when it comes to password complexity, length, and expiration. This can make it easy for attackers to guess or crack passwords, putting organisational resources at risk.
While tools such as mobile device management (MDM) solutions exist to enforce password policies and enable LDAP sync on domain-joined Mac devices, access management on macOS can still be a cumbersome process for both users and administrators. Users are often required to maintain multiple passwords and login credentials, which can be a source of frustration and security risk. Admins must also manage various tools and workflows to ensure that users have access to the resources they need while maintaining necessary security controls.
With Desktop Password Sync, users only need to remember one set of credentials: their Okta username and password. By setting strong password policies via Okta’s Admin Console, organisations can ensure that users are following best practices for their passwords across devices and web resources. With this new feature, Okta offers a promising solution that can simplify access management and improve security for organisations.
The user journey
Desktop Password Sync consists of a two-part flow: registration and authentication.
- When a user logs in to the device, they will see the following system notification, prompting them to go through registration.
- After clicking on “Register,” the user will be presented with a simple Mac-native workflow.
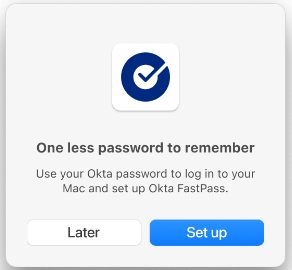
- The system will then prompt the end user to enter their local account password one last time to enable Okta to manage their password going forward.
- With that registration complete, the user can now authenticate with Okta. The system will prompt the user to enter their Okta password to sync it to their Mac device.
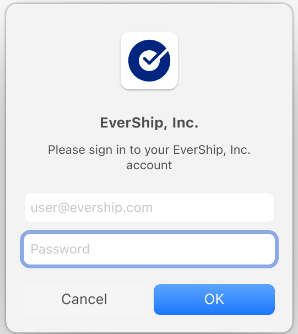
- Once successful, macOS updates the local account password to match Okta’s, enabling the user to log in to the device using their Okta password.
- Desktop Password Sync is now complete! It provides a seamless user experience that uses Okta credentials to log in to the Mac. In addition, because we enrolled the user with FastPass as a part of the registration process, the user is now also able to access their browser or native apps by just providing biometrics.
Taking a deeper dive
Registration is orchestrated by Okta Verify’s SSO extension. The registration process begins with macOS generating two public/private key pairs, one for device signing and one for device encryption. The private keys are kept locally on the Mac, managed natively by macOS’s Platform SSO process. The public keys are made available to Okta’s SSO extension, which enrols both keys with Okta’s backend server while simultaneously creating a link between the local account and the user's Okta account. With the keys and user link established, the Mac and Okta’s backend can communicate securely, enabling the user to log in to the device using their Okta credentials.
Unlike the registration part of the flow, where control is partially delegated to the SSO extension, the authentication process is driven by the operating system itself, communicating with Okta’s server directly using Apple’s Platform SSO protocol. The protocol starts with the operating system requesting a server nonce. On successful nonce request, the operating system builds a JWT signed with the device signing key that was saved in the registration step. The JWT contains the username and password that was entered by the user during device login, along with the server nonce that was requested previously. This JWT is sent to Okta’s token endpoint, which then validates the credentials in the JWT and the signature, ensuring that the password sync is coming from a known and previously registered Mac. Okta’s token endpoint responds with a JSON Web Encryption (JWE) token that is encrypted by the device encryption key. This encryption ensures that only the intended Mac can decrypt and access the tokens within. After receiving the token from the Okta server, macOS performs signature validation. At the end of the authentication step, the local account password is updated to keep it synced with Okta’s password, and the tokens are securely stored on the operating system.
In summary
As the workplace continues to evolve towards a Zero Trust architecture, it is important for organisations to adopt new technologies to ensure the security of their resources. Okta enables great benefits to customers through product Device Access. By leveraging this powerful technology, organisations can improve security, enhance user experience, and streamline the management of identities and access.
Access management on macOS has been a challenge for organisations in the past. However, the introduction of Okta’s Desktop Password Sync, a feature under the Device Access product, simplifies password management for macOS and balances security with convenience by enrolling users in FastPass.
Okta is committed to building the best access management story for macOS by working closely with Apple. Visit the Okta Device Access webpage to learn more details.
Have questions about this blog post? Reach out to us at [email protected]. Explore more insightful engineering blogs from Okta to expand your knowledge. Ready to join our passionate team of exceptional engineers? Visit our career page. Unlock the potential of modern and sophisticated identity management for your organisation. Contact Sales for more information.

