What are Salted Passwords and Password Hashing?
Security is often not top of mind when creating customer-facing applications. But in a landscape of continual data breaches of major corporations like T-Mobile and Google, companies must be vigilant to adhere to security best practices.
Processes like password salting and hashing are fundamental to the security posture of your apps. Understanding these broader security concepts is the first step in avoiding major breaches to your database, and loss of consumer trust.
In this post, we will explore the basics of encryption and cryptography, the mechanics of password hashing, and the application of salted passwords to uncover why security experts care about these topics.
Cryptography & Encryption
To understand why salted passwords were created, and how they work, we first need to explore the importance of cryptography and encryption. Some definitions:
Cryptography is defined as the practice and study of techniques of secure communication between two parties in the presence of a 3rd party.
Encryption is a technique of cryptography wherein a message is encoded such that only authorised parties can read it, converting plaintext into an unintelligible series of letters/numbers.
Cryptography and encryption are crucial today because of their role in helping protect against bad actors from around the world. With cybercrime becoming the fastest-growing crime in the U.S., and costing the global economy more than $450 billion in 2016, employing best practices of encryption and cryptography are more important than ever.
If all information were plaintext and had no encryption or cryptography surrounding it, sensitive materials like password information, health records (PII), and even bank account information (PIFI) could be stolen and sold to the highest bidder. One of the first steps of basic security hygiene is to not store sensitive data in plaintext—especially passwords. This is where password hashing comes in.
What is Password Hashing?
Password hashing is defined as putting a password through a hashing algorithm (bcrypt, SHA, etc) to turn plaintext into an unintelligible series of numbers and letters. This is important for basic security hygiene because, in the event of a security breach, any compromised passwords are unintelligible to the bad actor. As a result, the theft of this information is considerably more difficult.
Below is an example of a few words going through the hashing process.
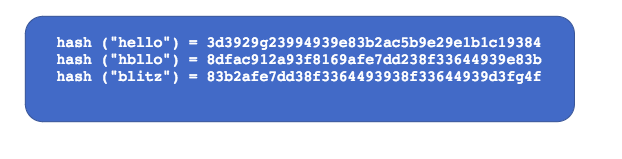
What is Password Salting?
Password hashing is a key step to protecting your users on the backend, but it’s not infallible because it hashes in a consistent way. This means it is predictable and can be beaten by dictionary attacks or rainbow table attacks.
“Hello”, for example, will always equal to the same combination of letters and numbers, and therefore can be guessed through brute force. One way of protecting against this is by adding a salt or using salted passwords.
Salting is the act of adding a series of random characters to a password before going through the hashing function. How does it work? Let’s take a look:
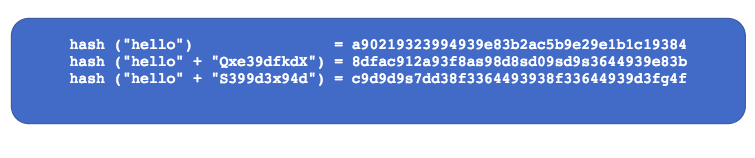
As you can see in the image above, we’re adding a series of random numbers and letters to the original “password” to result in a different hash function each time. This way, we protect against the flaw of the hash function by having a different hashed password each time.
Where should salted passwords be stored?
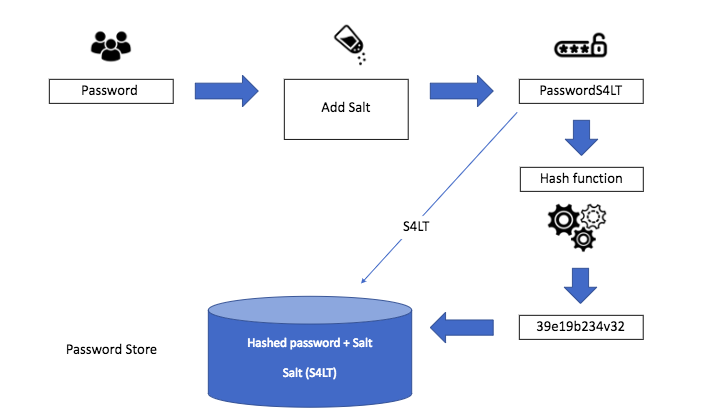
In terms of how this works in the IT infrastructure, salts have to be stored in a database along with the user password, as illustrated below. Salts are recommended to be random and unique per login to mitigate attacks using rainbow tables of pre-computed hashes. While an attacker could still re-compute hashes of common password lists using a given salt for a password, a way to provide additional defense in depth is to encrypt password storage at rest, preferably backed by a HSM or cloud key management service like AWS KMS.
Beginning your journey
That’s how salted passwords work. But that’s only the tip of the iceberg for securing your customer-facing applications. Understanding these concepts around cryptography and encryption is a lengthy process, and when creating customer-facing applications, creating these workflows are not easy.
How Okta can help
Today, Okta supports the use of salted passwords, and we employ industry best practices to best protect your customer data. We support standardised hashing algorithms like bcrypt to best secure your customer passwords and allow for secure authentication.
When you store your customer data with Okta, we never allow for passwords to be exfiltrated with restrictive admin policies. This prevents a single point of vulnerability due to privileged access, and protects against account takeovers.