How FIDO2 + WebAuthn Offer a Seamless, Secure Login
For those not familiar with FIDO2, it is an improved version of the FIDO standard – popularly known for the U2F USB tokens provided by Google and Yubico.
Now that we've explored what Webauthn is and reviewed critical Webauthn building blocks and protocols, I’ll use this post to break down how you can leverage WebAuthn with FIDO2 to enhance both app security and user experience.
Where U2F falls short
Let’s be clear. FIDO and U2F are awesome. They are built on open-standards, and are among the best authentication factors out there thanks to a killer combination of user-friendliness and strong resistance to phishing attacks. With U2F, users can authenticate into systems with MFA via a single tap on a USB device. Lovely. And on top of all this, a few different U2F tokens also worked over NFC and Bluetooth, offering a great end user experience for mobile apps.
However, the first version of FIDO has some limitations. For starters, U2F cannot verify the user using the authenticator. Since U2F do not support biometrics, anyone in possession of your U2F key could use the authenticator on your behalf. The solution proposed by the FIDO alliance for user binding was UAF, but this protocol is difficult to implement, and therefore not widely adopted. Some vendors would even encapsulate fingerprint readers into U2F tokens, but this also wouldn't effectively solve the problem.
Enter FIDO2 + Webauthn
With FIDO2 and WebAuthn, those challenges are no more. This combination offers strong authentication with biometrics binding users to tokens. This standard is being widely adopted by the industry, from browsers such as Google Chrome, Microsoft Edge and Firefox to hardware devices such as Android and Apple MacBooks. FIDO2 is here to stay.
What does the admin experience look like?
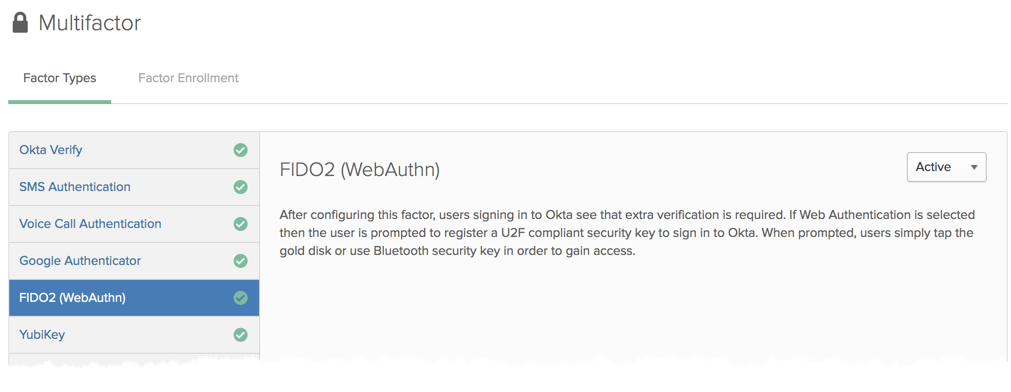
1. First, enable FIDO2 on your factors page:
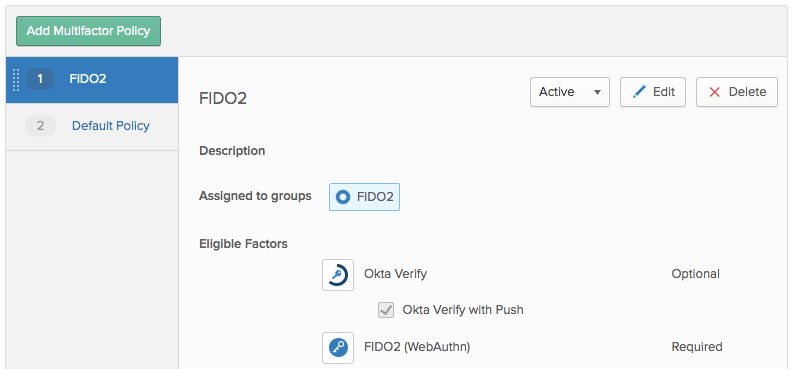
2. Next, create a Factor enrollment policy, similarly to how you do for other factors in Okta. We recommend you add more than one factor in addition to FIDO2. This way, you avoid problems when users forget their devices.
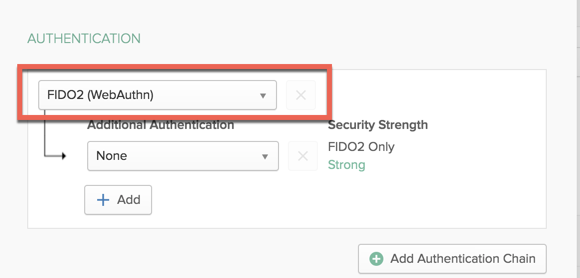
3. Third, create sign-on policies using FIDO2 as a factor:
Now you just need to enrol users in WebAuthn and boom, you are all set!
What does the user experience look like?
Let’s take a look at how easy this is for the user.

Pretty nifty. Let’s take a closer look at that TouchID…

Awesome stuff.
The result? Enhanced security by binding users to authenticators as well as a seamless login for users. To learn more about FIDO2 and WebAuthn, check out another post I’ve written: Understanding FIDO Standards: Your Go-To Guide, or view the session below from Oktane19.

