Okta Identity Engine
A set of customisable building blocks for any access experience
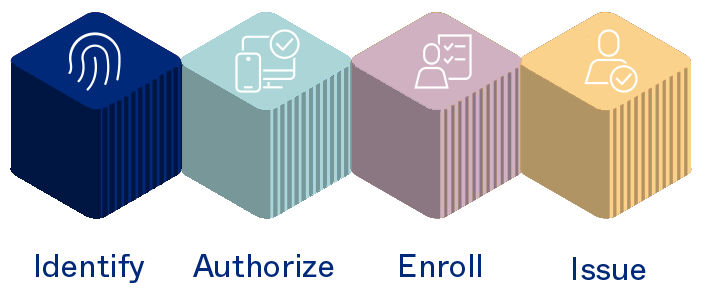
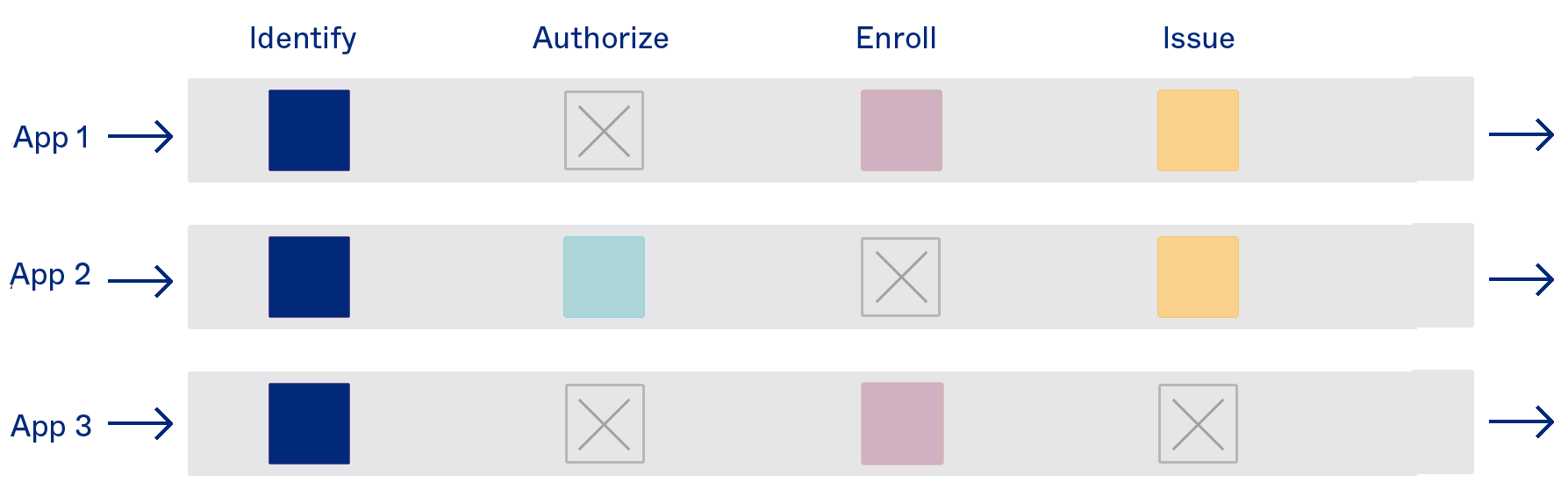
Use cases enabled by the Okta Identity Engine

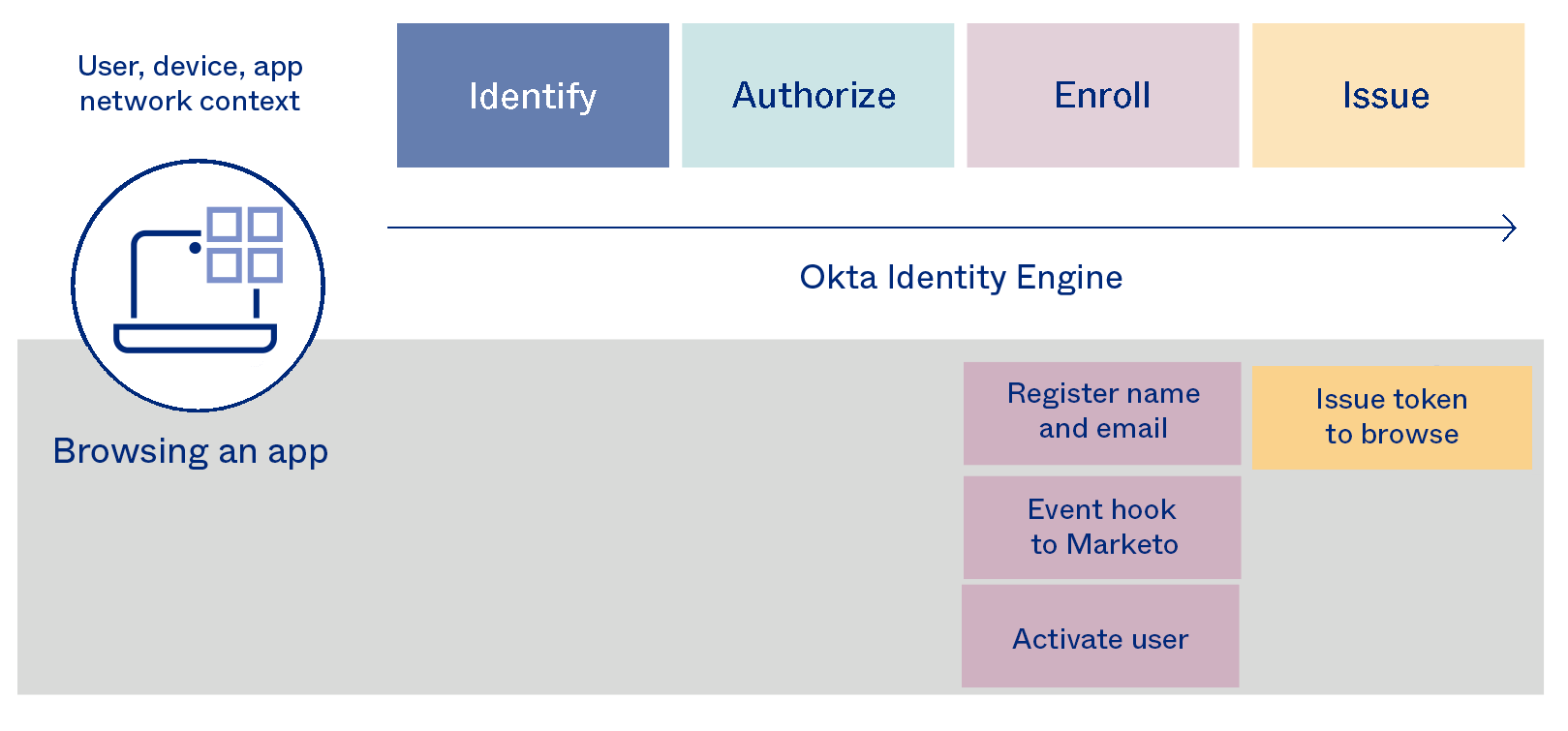
Features
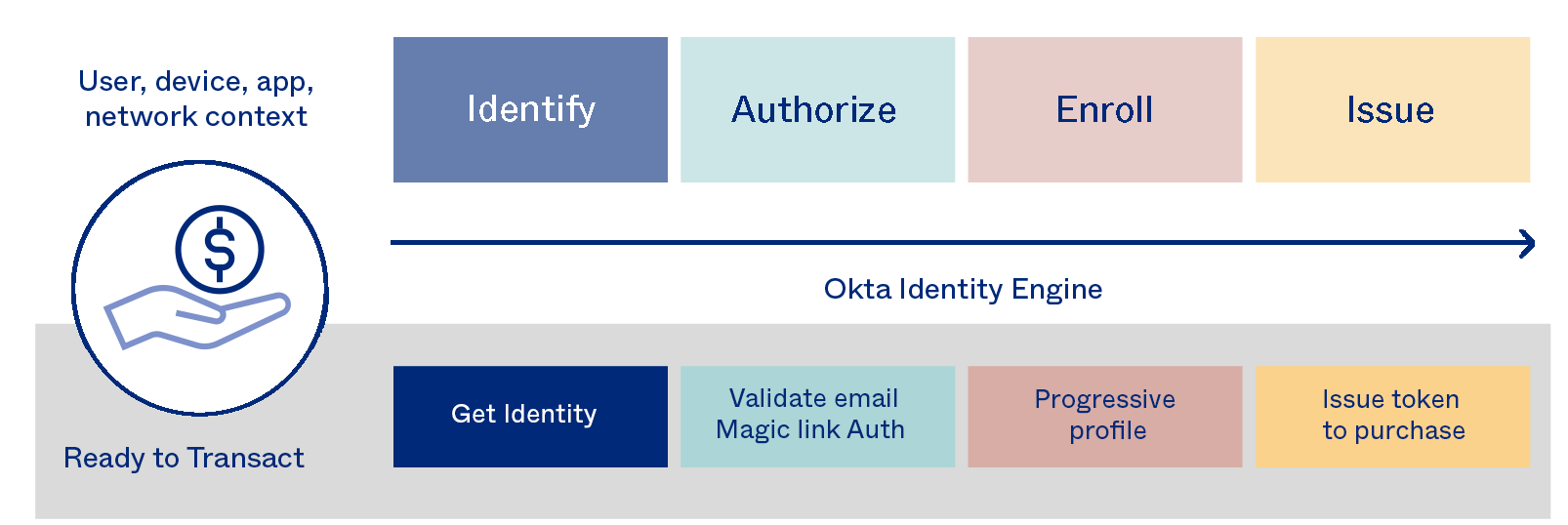
App-level policies
Customise security policies
Create dynamic sign-on policies that are tailored for different applications based on the behaviour, risk level, and context of the user. For example, you may want to enforce a more stringent assurance requirements to gain access to a sensitive app, but relax those requirements if you have high confidence the access request is legitimate given the user’s past behaviour and current context.
Unlimited possibilities
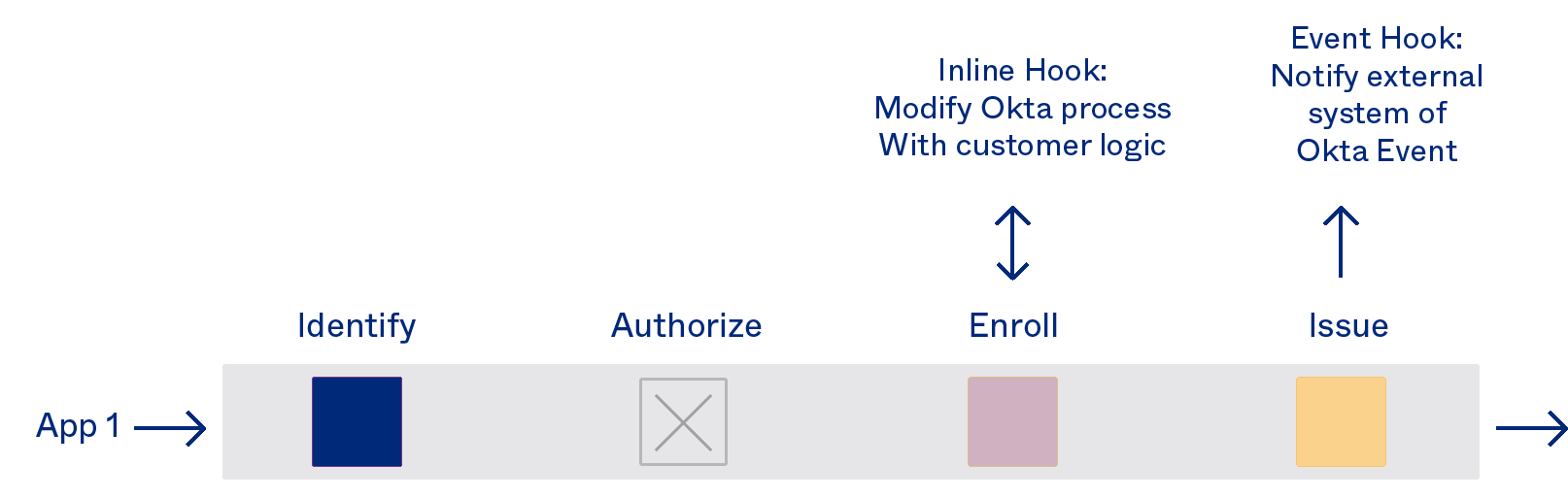
But that’s just the beginning. With Okta Hooks and Okta Identity Engine, Okta can be securely customised to be the foundation for any digital experience imaginable. A selection of the use cases unlocked include:

Ramiya Iyer
Global Vice President of IT, Digital and Marketing
Albertsons interacts with over 34 million customers a week, providing the products they want, at a fair price, with great customer service. As one of the largest grocers in the country, we recognise how important it is to adapt and grow, meeting our customers wherever they are. The Okta Identity Engine provides us with a flexible solution to digital identity.