Okta performs tens of billions of successful authentications monthly while simultaneously blocking billions of malicious requests. With Identity Threat Protection (ITP), Okta now expands this protection beyond initial authentication to help secure the entire identity lifecycle. ITP’s detections are smarter because they are continuously enhanced by the insights from the entire Okta ecosystem. To demonstrate the depth and impact of ITP, we will cover three main topics in this blog:
- Why ITP and how it works.
- Show real-world statistics and the benefits realized by customers who have already adopted it.
- Expert recommendations to take better advantage of ITP.
Why identity protection can’t stop at login
As a leading identity provider, Okta is uniquely positioned to identify the emerging Tactics, Techniques, and Procedures (TTPs) used in identity-based attacks. Attackers use a variety of TTPs that rely on the usage of breached credentials, sophisticated phishing infrastructure, stolen identity tokens, and other methods.
Enforcing the use of phishing resistant authenticators secures authentication and prevents the theft of session tokens at sign-in. It does not, however, protect against scenarios where the tokens are stolen post-authentication. Active sessions can be stolen at any time, even when users are not using them. As adversaries evolve their TTPs, the user identities themselves can also be compromised. ITP addresses these security gaps by introducing the following capabilities:
- Evaluate Session Risk - Continuously evaluates the actions performed during an active user session, checking for compliance with access policies and verifying that it is being used by the rightful account owner.
- Evaluate User Risk - Continuously evaluates the activities associated with a user (even when the user does not have an active session) to help ensure the user identity is not compromised.
- Configure Automated Responses - Provides the ability for IT and Security Administrators to configure automated responses to mitigate detected threats.
Session Risk: Real-time protection against session hijacking
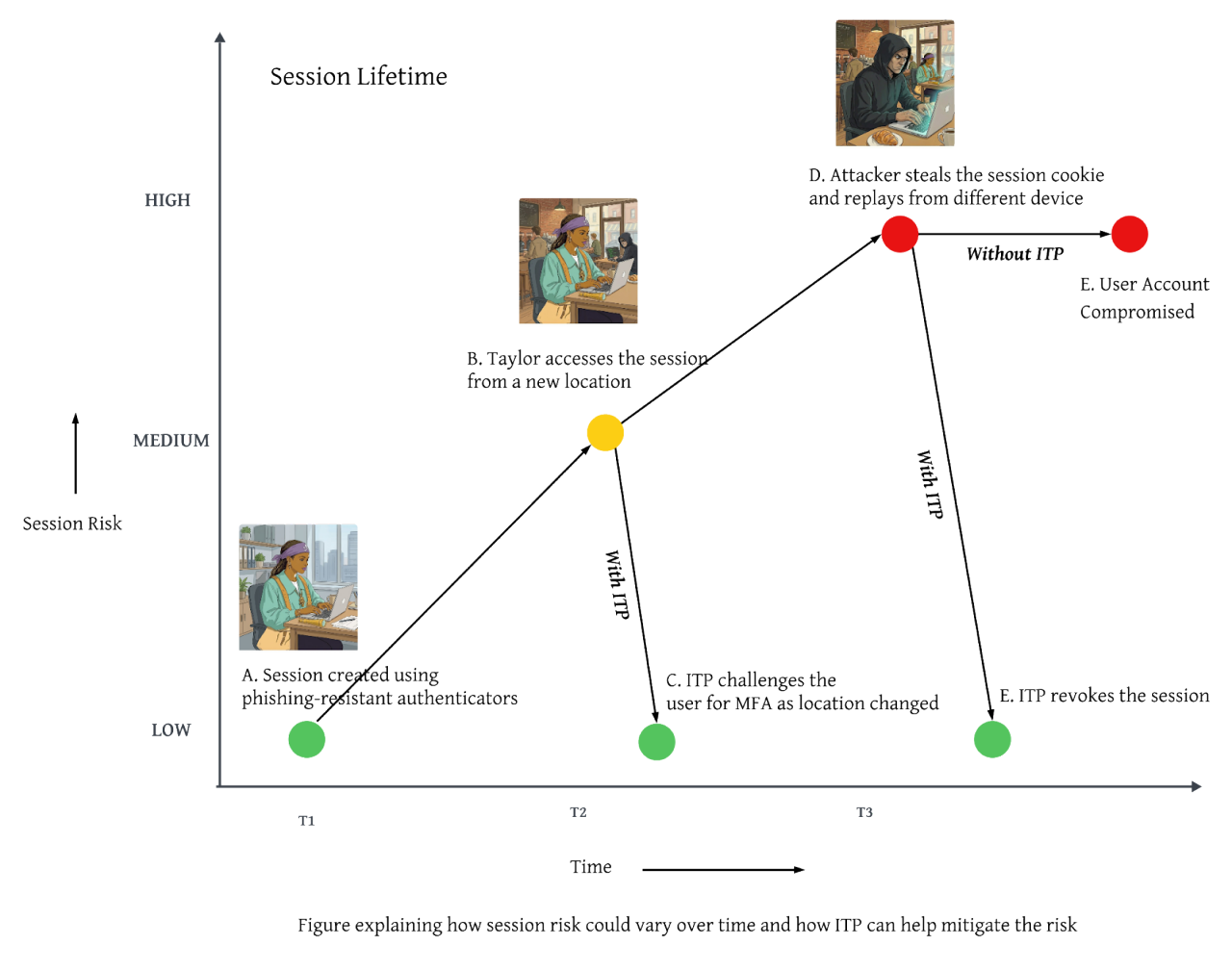
The concept of Session Risk introduced as part of ITP allows for continuous monitoring of the risk level tied to a user's active session. The risk fluctuates during the course of a session. For example, consider the timeline below of Taylor.
8:30am (T1): Session start
Taylor starts her day from the office and logs into her work account using a phishing resistant authenticator, like Okta FastPass. ITP determines that the session risk is LOW since she is logging in from a known network, known device, and is using a known phishing resistant authenticator.
10:45am (T2): Location change mid-session
Taylor, who started her session from her primary office location, goes to a client location to continue her work. ITP detects the location change during an active session, re-evaluates the access policies, and prompts her with MFA. Taylor answers the authentication prompt and she continues her work.
12:15pm (T3): Session compromise detection and response
An attacker tricks Taylor into downloading malware onto her device via a phishing email. The attacker steals her session cookie and attempts to use it from their infrastructure to impersonate Taylor. ITP detects that the session has been compromised and immediately performs a Universal Logout, thus revoking the session and making the stolen session cookie unusable. Meanwhile, Taylor seamlessly reauthenticates, establishes a new session, and continues her work.
As you can see, Okta stopped the adversary from abusing the stolen session token, while providing a simple, transparent experience to the end user. All of these outcomes were orchestrated by Okta’s ITP, which helps ensure that active user sessions are in compliance with the organization’s access policies throughout the session lifecycle.
How is Session Risk evaluated?
ITP continuously assesses the risk level of an active Okta (IdP) session. If the network or the device attributes change during a session, ITP determines that the session context has changed. It then evaluates session risk by running machine learning models and targeted heuristics to determine a session risk level of Low, Medium, or High.
The session context change triggers a re-evaluation of the Global Session Policy and App Sign-in Policies. It uses the session risk level to determine if any action needs to be taken to adhere with the policies. If the policy re-evaluation results in a DENY or if the user does not respond to the MFA challenge required by the policy, ITP treats it as a “failure” and applies the mitigation actions configured in the Session Protection enforcement settings.

The result
Between October 15th 2025 and November 15th 2025, a 30-day period:
- Session context changes: ITP detected around 6 million session context changes.
- Policy re-evaluation failures - Of the total policy re-evaluations triggered by the 6 million session context changes, around 5,000 policy re-evaluation failures were identified by ITP as carrying a high session risk.
- Okta sessions remediated - ITP customers remediated more than 1,000 potentially risky Okta (IdP) sessions immediately via automated actions (either prompting for inline MFA or by revoking the session).
- App sessions remediated - ITP customers revoked more than 6,000 potentially risky app sessions using the automated actions.
- Additional actions - ITP customers took the additional action of running a workflow at least 250 times.
This shows not just the scale of detections and policy evaluations ITP drives, but also how we are able to help customers identify and proactively defend against the high-risk events that matter most, right at the identity layer.
User Risk: Connect risk across sessions, apps
The concept of User Risk was introduced to keep track of the security status of a user account over time. Session Risk, as explained earlier, is also one of the factors that influence User Risk.
How is User Risk evaluated?
ITP continuously aggregates User Risk by using various methods, including, but not limited to:
- Threat intelligence and analysis: Detections curated by the Okta Threat Intelligence team, which flags user accounts that have interacted with known malicious infrastructure. Examples of detected activity include interactions with IPs associated with phishing-as-a-service platforms that target popular business applications.
- Inline detections: Detects adversaries performing critical actions, such as enrolling credentials from known malicious IPs, authenticating using breached credentials, hijacking sessions, etc.
- Multi-event inferences: Identifies any past suspicious successful logins by running ML models and heuristics using Okta’s batch data pipelines.
- Partner-reported signals: Ingests Continuous Access Evaluation Profile (CAEP) events from partner vendors using the standards-based OpenID Shared Signals Framework (SSF).
- End-user or admin-reported anomalies: High-confidence signals generated when end-users or admins report suspicious activity directly in the user profile.
Once User Risk detections are collected and analyzed, the respective policy – called the “Entity Risk Policy” – can be configured to trigger downstream actions according to the risk level (Low, Medium, or High). These include Universal Logout for all connected apps, or other actions through Okta Workflows.
The result
Between October 15th 2025 and November 15th 2025, a 30-day period:
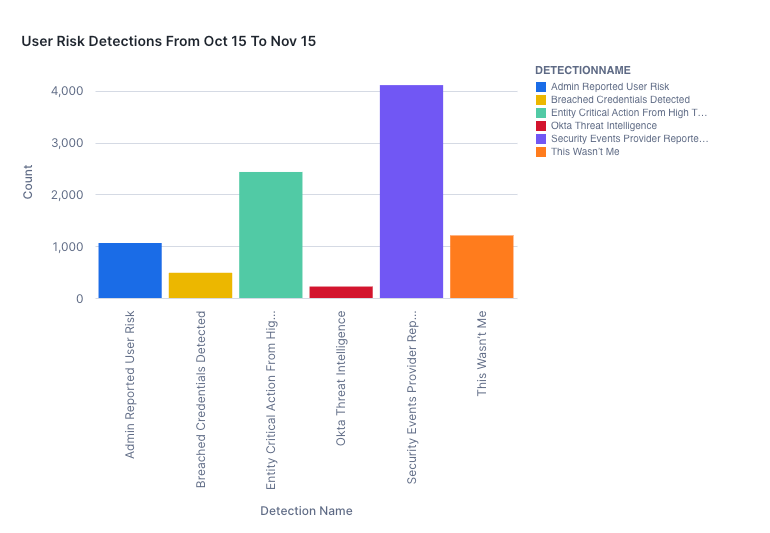
- ITP detected around 8,000 users to be at high risk across more than 200 organizations as shown in the chart below.
- More than 6,500 of these users’ risk was remediated through automated actions, such as performing Universal Logout or running a Workflow as part of the Entity Risk Policy.
- The Okta Threat Intelligence detection flagged nearly 220 users as high risk across 46 organizations during this time period.
It’s worth noting that Okta's Threat Intelligence team recently discovered VoidProxy, a highly evasive and sophisticated Phishing-as-a-Service. The detailed breakdown of VoidProxy infrastructure is on the Okta Security blog and analysis of similar services are available for Okta customers to view and download at security.okta.com.
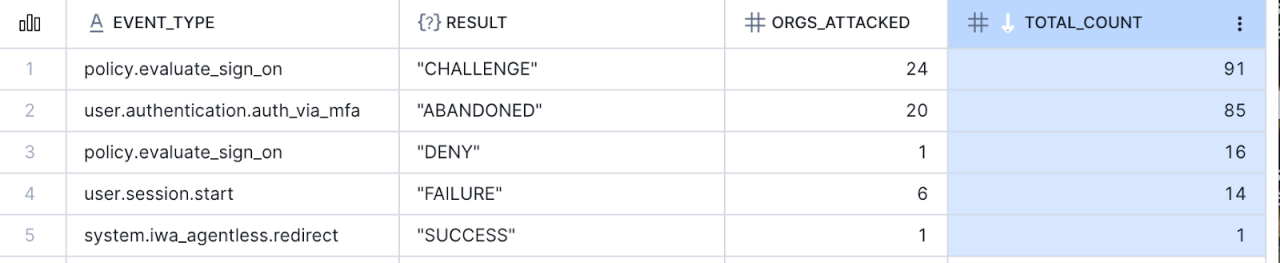
To shed light on the malicious activity of these infrastructures, the chart below illustrates activity originating from an IP address linked to VoidProxy over a four-day period. It indicates that an attacker using this IP tried to attack at least 24 distinct organizations. All the attempts to login from the IP were either denied or the MFA challenge was abandoned. ITP fired user.risk.detect events for users targeted in the attack and added the relevant malicious IPs to these events.
To prevent repeat abuse, ITP administrators can configure workflows that automatically add these detected malicious IPs to a blocked network zone using the Entity Risk Policy.
What’s next?
We just shipped three new user risk detections and can’t wait to hear the feedback about them. We will dive deep into more User Risk detections, their impact on customer security, and how we leverage AI in a follow-up blog.
As mentioned earlier, ITP's detections are smarter because they look at signals observed across the Okta ecosystem. Our global vantage point as the central identity provider enables ITP to detect emerging attack patterns and threats across thousands of organizations that would be invisible to any single organization. These insights are continuously incorporated into ITP detections, allowing Okta to proactively protect all customers.. This security network effect provides a level of real-time threat intelligence that single-tenant solutions or non-identity providers simply cannot match.
Recommendations
Session Risk
- Session Risk evaluation is considered during policy evaluations only when the risk condition is configured in your access policies. So, we strongly recommend configuring it if you have not already.
- Configure the Session Protection Policy in “Enforced with Action” mode to protect against session hijacking once you observe ITP in monitoring mode for a few days.
- Based on your monitoring results, you can leverage the new Session Protection detection settings to establish the Session Risk level and Trusted Network Zones. This setting skips policy re-evaluations only for sessions originating from these defined Trusted Network Zones and/or risk levels.
- Okta captures the session context changes in its System Logs as they happen. We recommend focusing on the events that resulted in elevated risk, so that you can tackle the threats that matter most.
User Risk
- Implement the recommended actions for the high-risk detections in the Entity Risk Policy.
- Leverage the Shared Signals Framework (SSF) to transmit CAEP events from your chosen security vendor to Okta. This integration empowers Okta's risk engine to enhance its assessment of user risk.
- Help improve ITP user risk detections in your organization by providing feedback (e.g., false positives) to the risk engine.
- Train users to identify indicators of suspicious emails, phishing sites, and common social engineering techniques used by attackers. Make it easy for users to report potential issues by configuring End User Notifications and Suspicious Activity Reporting.
Conclusion
Since launching General Availability for ITP over a year ago, customers are already experiencing tangible benefits, including earlier detection of attacks and faster automated response. Don't leave your organization exposed. Start leveraging the full potential of ITP today by implementing the Session and User Risk recommendations to help ensure your users are continuously protected. Learn more about how Okta deployed ITP within our organization to discover more best practices.






