Identity Threat Protection with Okta AI is transforming security
We live in a time where remote work, BYOD trends, and a complex tech stack have become the norm. Identity providers play a vital role in this landscape; they serve to unite and secure your organisation. As the horizontal layer that spans your entire system, they provide a unique, single point of visibility and access control at the app level. So, in this world of increasingly sophisticated threats and heterogeneous architectures, Identity, as the connective tissue, integrates and fortifies your long-term defense strategies.
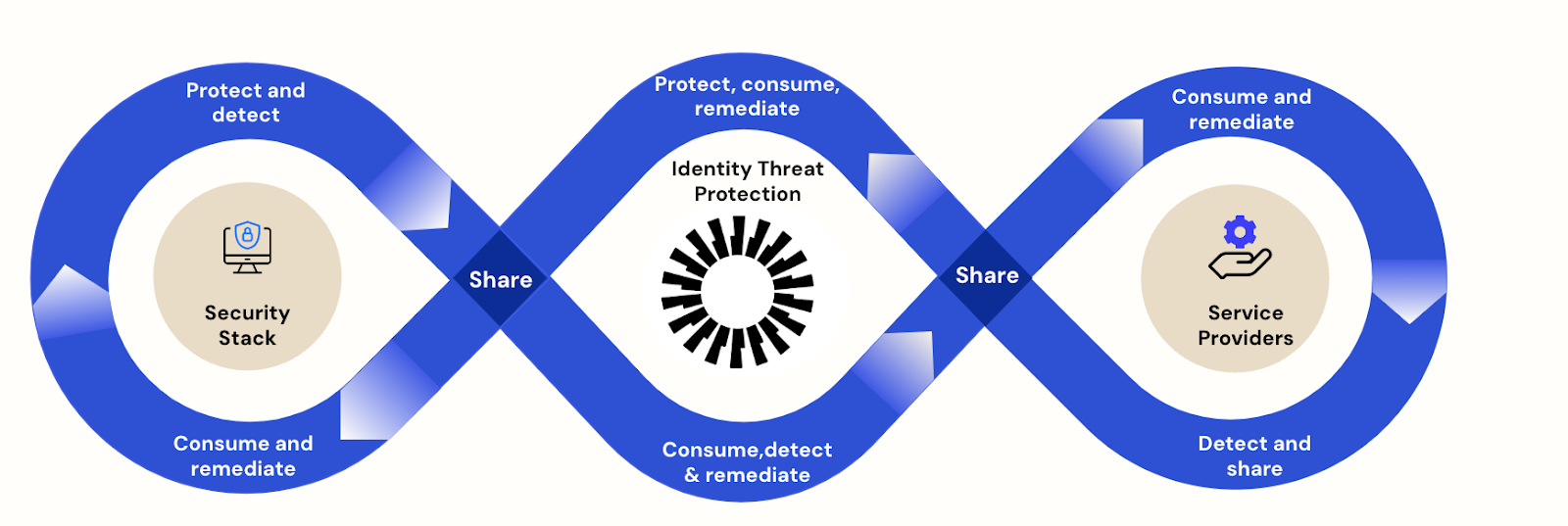
To meet these evolving demands, Okta is thrilled to introduce Identity Threat Protection with Okta AI. Aiming to be available in Limited Early Access in the first quarter of 2024, this isn't merely an addition to your security toolkit. Identity Threat Protection (ITP) represents a shift in how we conceive of and execute Identity-based security. Leveraging neutrality and broad integration, ITP acts as the unifying layer that cohesively integrates the diverse components of your tech stack. In doing so, it offers a new kind of security paradigm, enabling near-frictionless integrations and real-time, post-authentication risk assessments.
Continuous risk monitoring — across the user journey
As cybersecurity evolves and grows in complexity, simply securing the initial login is no longer enough. A stolen cookie/token can serve as a skeleton key, granting access to various corporate resources, sensitive information, and malware. The implications are clear: risk assessment should cover the entire user journey—not just log in. ITP detects threats arising from changes in context continuously, re-evaluating IP and device risk.
Post-authentication risks: the weak link in Identity security
Even organisations with strong Identity security – such as phishing-resistant auth and least-privileged access to resources – can have gaps. Say an attacker infiltrates a partner account and plants malware on an employee's device, pretending to be a collaborator. The employee opens the file, and a malicious Python script kicks into action, gathering important Identity and access tokens from your organisation. Without raising any suspicion from the idP, the bad actor can use these stolen tokens to access your sensitive data, leaving your environment at risk and vulnerable to data breaches.
The need for integrated Identity-centric security
While device and app security layers like EDR and CASB/SASE can effectively generate alerts, they should feed signals into a unified Identity-centric security posture. Our new capabilities ingest alerts from various best-of-breed platforms for accelerated risk assessments. This approach balances prevention, detection, and response while continuously assessing risk. The result benefits end-users and security teams alike — heightened security without compromising user experience.
Bridging security silos for a unified Identity defense
Identity Threat Protection aims to enhance an organisation’s span of control, not replace what’s already there. It integrates existing ecosystems and extends solution capabilities. It takes what's working and makes it better, smarter, and more integrated, with Identity protection as the central goal.
The challenges of a fragmented security landscape
We all know what’s driving the need for integration… Most security environments consist of isolated information silos with little to connect them. Each security solution operates in its unique ecosystem, with no clear lines of communication. These lapses introduce policy sprawl, additional tooling, and/or homegrown scripting. This patchwork of solutions leaves teams scrambling for cohesion, wasting time and funding.
Breaking barriers for collective threat awareness
The Shared Signals pipeline aims to break down these silos, reduce the costs of a best-of-breed approach, and strengthen collective Identity threat detection. Our philosophy is not to compete with partners, we integrate their intelligence into the Identity threat surface. We're investing in and helping develop open standards like the Shared Signals Framework (SSF) and protocols like CAEP. These standards establish mechanisms to share security events, state changes, and signals across federated systems.
Collaborating with industry leaders
To enable this ecosystem, we've partnered with leading security companies, including CrowdStrike, Jamf, Material Security, Netskope, Palo Alto Networks, SGNL, Trellix, Zimperium, and Zscaler. These collaborations allow us to collectively provide customers with a comprehensive, multi-sourced, yet seamless integrated solution to our mutual customers.
“As a contributor to the Open Cybersecurity Schema Framework (OCSF) project, Netskope understands that effectively defending against today’s cyberattacks requires cybersecurity tools to coordinate and share security signals with each other,” says Lamont Orange, Chief Information Security Officer at Netskope. “Our partnership with Okta provides security and admin teams with deeper visibility into how users interact with resources, making it easier to detect any changes in user risk.”
Taking adaptive action to the next level with Okta
While denying access at a point in time when the risk level is deemed high is often the most applicable response, the story doesn’t end there. Offering flexible actions for an automated, multi-layered response, ITP goes further, highlighting shifts in user context and risk levels across Okta sessions and all connected apps.
Inline actions
One of our key features, Universal Logout, enhances inline actions like session revocation and post-auth prompting of multi-factor authentication. By instantly terminating a user’s sessions across integrated apps when enabled, if policies are configured accordingly, Universal Logout allows organisations to revoke access. This blocks former or terminated employees from using active sessions to access resources. It also enables security teams to quickly disable detected bad actors’ access in response to a threat, like ending a compromised session that was hijacked and accessed from a different device. Currently, Universal Logout works with select leading apps, but this list will expand continually.
The power of Okta Workflows
While Okta customers are already familiar with the power and utility of Okta Workflows, the addition of ITP builds on that foundation. With Workflows deeply integrating security-relevant actions across many apps, ITP can leverage Workflows to orchestrate automated responses for diverse threat scenarios flexibly. You can generate a ticket in ServiceNow, alter a user’s access in Salesforce, and/or even trigger custom API actions.
What’s Next?
With ITP, we're formally marking our entry into Identity Threat Detection and Response (ITDR), serving a clear need in the market. Our consolidated solution is tailored for multi-sourced, diverse, Identity-centric threat detection and response for Okta environments. By leveraging the power of Identity as a core pillar of security, ITP maximises your existing investments, including XDR. ITP acts as a bridge, connecting various security tools. It creates a closed-loop system that integrates threat detections, correlates risks, and triggers automated countermeasures throughout the Identity lifecycle.
Level up your Identity security by partnering with Okta. Connect with your top security and SaaS app providers to collaborate on our open standard platform. By teaming up, you'll enhance your offerings and contribute to a stronger Identity security landscape for everyone. Let's advance together.
To learn more, visit the Identity Threat Protection page for upcoming deep dives, blog posts, and resources as we approach this Limited Early Access release.
—------
Safe Harbor
This document contains “forward-looking statements” within the meaning of the “safe harbor” provisions of the Private Securities Litigation Reform Act of 1995, including but not limited to, statements regarding our financial outlook, long-term financial plans, product development, business strategy and plans, market trends and market sise, opportunities and positioning. These forward-looking statements are based on current expectations, estimates, forecasts, and projections.
Words such as “expect,” “anticipate,” “should,” “believe,” “hope,” “target,” “project,” “goals,” “estimate,” “potential,” “predict,” “may,” “will,” “might,” “could,” “intend,” “shall” and variations of these terms and similar expressions are intended to identify these forward-looking statements, although not all forward-looking statements contain these identifying words. Forward-looking statements are subject to a number of risks and uncertainties, many of which involve factors or circumstances that are beyond our control. For example, the market for our products may develop more slowly than expected or than it has in the past; there may be significant fluctuations in our results of operations and cash flows related to our revenue recognition or otherwise; we may fail to successfully integrate any new business, including Auth0, Inc.; we may be unable to retain key personnel; global economic conditions could worsen; a network or data security incident that allows unauthorised access to our network or data or our customers’ data could damage our reputation and cause us to incur significant costs; we could experience interruptions or performance problems associated with our technology, including a service outage; and we may not be able to pay off our convertible senior notes when due.
Further information on potential factors that could affect our financial results is included in our most recent Annual Report on Form 10-K and our other filings with the Securities and Exchange Commission. The forward-looking statements included in this presentation represent our views only as of the date of this presentation and we assume no obligation and do not intend to update these forward-looking statements.
Any products, features or functionality referenced in this material that are not currently generally available, may not be delivered on time or at all. Product announcements do not represent a commitment, obligation or promise to deliver any product, feature or functionality, and customers should not rely on them to make purchase decisions.

