Cyber Kill Chain Defined: A Review of Cyber Kill Chain Steps
A cyber kill chain is a series of steps designed to stop a cyberattack.
When reporters cover hacks, they use words like “suddenly” and “surprise.” The event seems to come with no warning, and the damage hits a company out of the blue.
In reality, a successful hack comes about through a series of predictable, repeatable steps. And some security experts believe that understanding those steps is critical to keep the next attack from succeeding.
The steps you should know are part of a cyber kill chain. Learn it backwards and forwards, and put in the proper protections at each step, and you could be a hero when the next attack appears.
What Is a Cyber Kill Chain?
Lockheed Martin developed (and trademarked) the concept of the cyber kill chain. But plenty of other companies have embraced the concepts.
Put a cyber kill chain into practice, and you'll study all of the steps malicious actors take as they gain access and then control of critical systems. You'll begin to think like a hacker, and you'll create countermeasures for the game plan your enemies follow.
The cyber kill chain is often compared to military maneuvers, and that's apt. Your goal with this concept is to anticipate your opponent's every move so you are always ready to respond appropriately.
In a large company, your enemies could number in the hundreds or even the thousands. And some of them won't be strangers. Former employees with grudges could also try to infiltrate your systems. The more you know about the steps they might take, the better you can prepare.
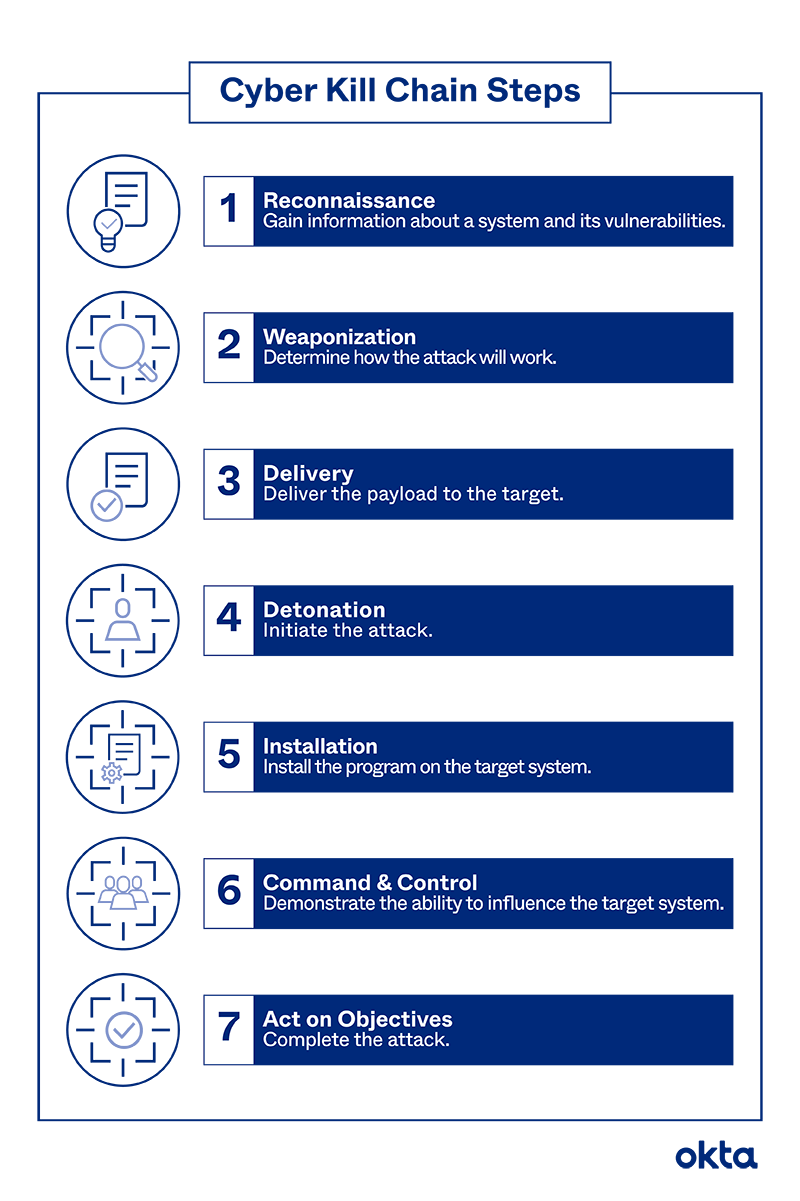
Cyber Kill Chain Steps Explained
The classic sequence described by Lockheed Martin consists of seven steps. You may choose to tinker and add a few of your own. Similarly, you may find that some of these steps just don't apply to your company and your audience. But we'll walk through them one by one to help you get started.
1. Reconnaissance
A hacker can't just walk into your system and take over. Most use in-depth research, triggered long before the attack begins, to understand the systems you use and your vulnerabilities.
A hacker might do this work in two phases.
- Passive: Sources such as LinkedIn, email directories, and published articles give the hacker information about who you are, what you do, what might be worth stealing, and how you protect it.
- Active: The hacker tries to dip a toe into the computer system to grab information. The research is subtle, as hackers know you'll retaliate if you find them.
2. Weaponization
The hacker digs into the research to determine what form of infiltration will be most successful. Are you a widely dispersed organization with plenty of email users? A phishing attack might work best. Did you just hire a crop of new IT members? No need to spend much time on sophistication, as your team is unlikely to find anything at all as they learn.
3. Delivery
The hacker puts the plans into action. This might be the first moment that you suspect something is amiss. But even then, the launch could pass you by.
For example, reporters say the most effective phishing email tells users that they've already been hacked. One click opens the door to further engagement.
Unless your team tells you about such email messages, or you get one in your inbox, you may never know this is happening.
4. Detonation
The attack is formally launched. A user clicks the email or plugs in the infected USB drive. All of the plans are suddenly moving.
5. Installation
Some attacks don't require malware. But many of the most devastating hack forms do.
For example, ransomware circulating in Fortune 500 companies in 2020 could have resulted in millions of dollars of losses. Companies would pay fees to get their files back after code was installed that encrypted all of their files.
If your attack does require some kind of program running on your servers, that step happens here, and it begins quickly after the detonation stage.
6. Command & Control
This phrase comes directly from the military, and it involves a soldier or low-level actor talking to commanders about next steps.
If your hacker is hired by a larger group, that person may need to prove access to your system. And then, that person may need to hear about what should happen next. The pause could be brief, or it could last long enough for you to take action.
7. Act on Objectives
Hackers know that simple entry has no value. They must do something at the end of this process to make the work worthwhile. That might involve asking you for money, stealing data to sell to someone else, or both.
Should You Install a Cyber Kill Chain?
Thinking like a hacker and walking over every bit of your security system takes time and effort. It's not your only option.
You could look for common hacking symptoms, such as these:
- Ransomware messages
- Redirected internet searches
- Random, incessant popups
- Unusual software installations
- Missing money
- Leaked information
But thinking like a hacker can mean patching glaring holes in your systems that put your security at risk. For example, you may need to focus on:
- Education. Do all employees in your organization know that they shouldn't click on buttons from email senders they don't recognize? A few classes could help you prevent problems in the Delivery part of an attack.
- Segmentation. Do you use firewalls to protect deeply sensitive information? If a hacker moves past one, will the others stay in place? This could help you during Detonation.
- Reaction times. How quickly are you notified of an intruder? Does your system require explicit action from you before recovery steps start? Few delays could help you during Installation and Command & Control stages.
You may never eliminate every risk. The hacking lifestyle appeals to many people, including students. You’ll always need to be on alert. But using a cyber kill chain could make your work a little easier.
Get Help From Okta
Deploy robust security solutions from Okta and make a hacker's work even harder. Use our sophisticated decryption tools to protect data in transit and at rest. And protect everything with our firewalls.
Contact us to get started today.
References
The Cyber Kill Chain. Lockheed Martin.
Cyber Kill Chain Model and Framework Explained. (March 2020). AT&T.
Reconnaissance the Key to Ethical Hacking. (August 2019). Medium.
Most Effective Phishing Tactic Is to Make People Believe They've Been Hacked. (October 2019). Info Security.
Major US Companies Targeted in New Ransomware Campaign. (June 2020). Dark Reading.
Command and Control. Oxford University Press.
Can You Spot the Hacker? (November 2020). EC-Council.
15 Signs You've Been Hacked and How to Fight Back. (August 2020). CSO.
How to Spot a Teenage Cyber-Hacker. (September 2019). Education Week.