Encryption scrambles your password so it's unreadable and/or unusable by hackers. That simple step protects your password while it's sitting in a server, and it offers more protection as your password zooms across the internet.
Imagine that you've created the strongest password possible. Now, imagine that all of your hard work is stored in plain text on your company's server. If a hacker gets inside, what happens next? All of your efforts go to waste, and your username and password are sold on the open market to the highest bidder.
Problems like this are common. In 2020, for example, security advocates discovered that unprotected usernames and passwords were sent to servers in China from internet-enabled doorbell systems.
How Does Password Encryption Work?
Experts use terms like salt, SHA-1, and private key to describe what encryption is and how it works. The terminology can be intimidating, especially for people with no background in computer science.
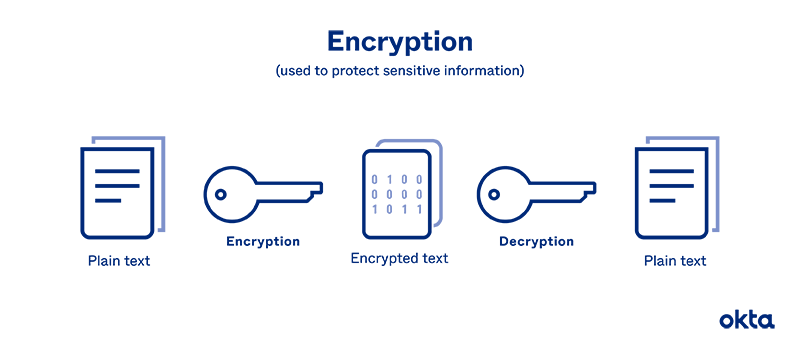
But put plainly, password encryption works by putting your original word through a series of scrambling steps.
Four main types of encryption exist.
- Symmetric key: Your system has a key for encryption/decryption. Move your password through this key to scramble it, and push it back through the key to make it readable once more. A hacker must steal the key to take over your password.
- Public key: Two keys play a role in altering your password. One, a public key, is available for anyone to use. The other, a private key, is available only to a select few. Use one to encode a message, and the recipient needs the other to make sense of it.
- Hashed: A computer algorithm transforms your password into a random series of numbers and letters. A hacker must know what algorithm you used to change your password, and that isn't always easy to discern.
- Salted: A few random numbers or letters are appended to the beginning or end of your password before it moves through the hashing process. A hacker must know the hash (which isn't always easy) as well as your hashing algorithm to decode the message. Your administrator can use a fixed salt that's the same for every password, or they might use a variable salt that changes with each password.
No matter how your company handles encryption, the result is the same. Your password changes from something you know and can remember into something that looks completely random.
Common Password Encryption Formats
Understanding password safety is a bit like learning a new language. Several tools exist to transform your passwords, and they all work a bit differently.
Imagine that our password is R@nT4g*Ne! (Rent Forgone, in common terminology.) Let's pass this through several different encryption tools:
- SHA-1: Our password is made up of 40 characters, and there is no clear decryption method. Our secure password is 12bf203295c014c580302f4fae101817ec085949.
- SHA-1 with Salt: Our password is still made up of 40 characters, but we appended the word "Free." Our secure password is bc6b79c7716722cb383321e40f31734bce0c3598.
- MD5: Our password is encoded into a 128-bit string. Our secure password is 4e84f7e8ce5ba8cdfe99d4ff41dc2d41.
- AES: Use this symmetric encryption algorithm, and you can choose bit length. It's nearly impossible to model what our completed password might look like, as we have far too many variables to choose one, and each will impact the outcome.
A persistent hacker can jump through your defenses and access your files. But use systems like this, and you're likely to cause significant delays. Hackers grow frustrated when they can't discover the algorithms you use to protect passwords. They may choose a different target instead.
Password Encryption Alone Isn’t Enough
With the use of hashing codes and salt, you can protect your password at rest and in transit. But you won't achieve full security until you do a little bit more. In fact, experts say that a strong encryption policy can leave you with blind spots. You think you're secure when you're not.
Be an advocate for strong password policies. Ensure that yours are:
- Unique. Don't use data from one system in another. If a hacker gains access to one database, your duplicate is at risk too.
- Strong. Experts recommend creating a random word list that corresponds to numbers. Roll the dice to determine what your new password should be.
- Memorable. Keep a written list of all your passwords, or invest in a digital solution that stores each one.
If you're notified of a breach, take action right away. The longer you delay, the more time a hacker has to steal data, take over your system, or both.
Get Expert Help With Okta
We build secure authenticationsecurity systems for companies both large and small. We can secure your information, data, and ensure privacy with advanced password management and multi-factor authentication solutions that will leave hackers scratching their heads.
We'd love to tell you more about how this works and how you can apply it. Contact us to find out more.
References
IoT Stupidity Strikes Again—Victure VD300. (November 2020). Electropages.
SHA-1. dCode.
MD5 Hash Generator. Dan's Tools.
AES Encryption and Decryption Online Tool (Calculator). Devglan.
Best Way to Know the Algorithm Used for a Password Encryption. Stack Exchange.
Major Cybersecurity Challenges in the Healthcare Sector. (December 2020). Healthcare Tech Outlook.
Creating Strong Passwords. (October 2018). Surveillance Self-Defense.


