Okta secures AI
Give your AI agents the keys, not the kingdom. Widespread AI adoption requires uncompromising security.


The AI agent workforce is already here
Shadow IT has evolved into Shadow AI. With agents operating as rogue pilots, the risk isn’t coming—it could already be inside your perimeter.
of organizations are already using AI agents*
experienced unintended agent behavior**
have a strategy in place*
report credential exposure via agents**
THE UNIFIED IDENTITY PLATFORM
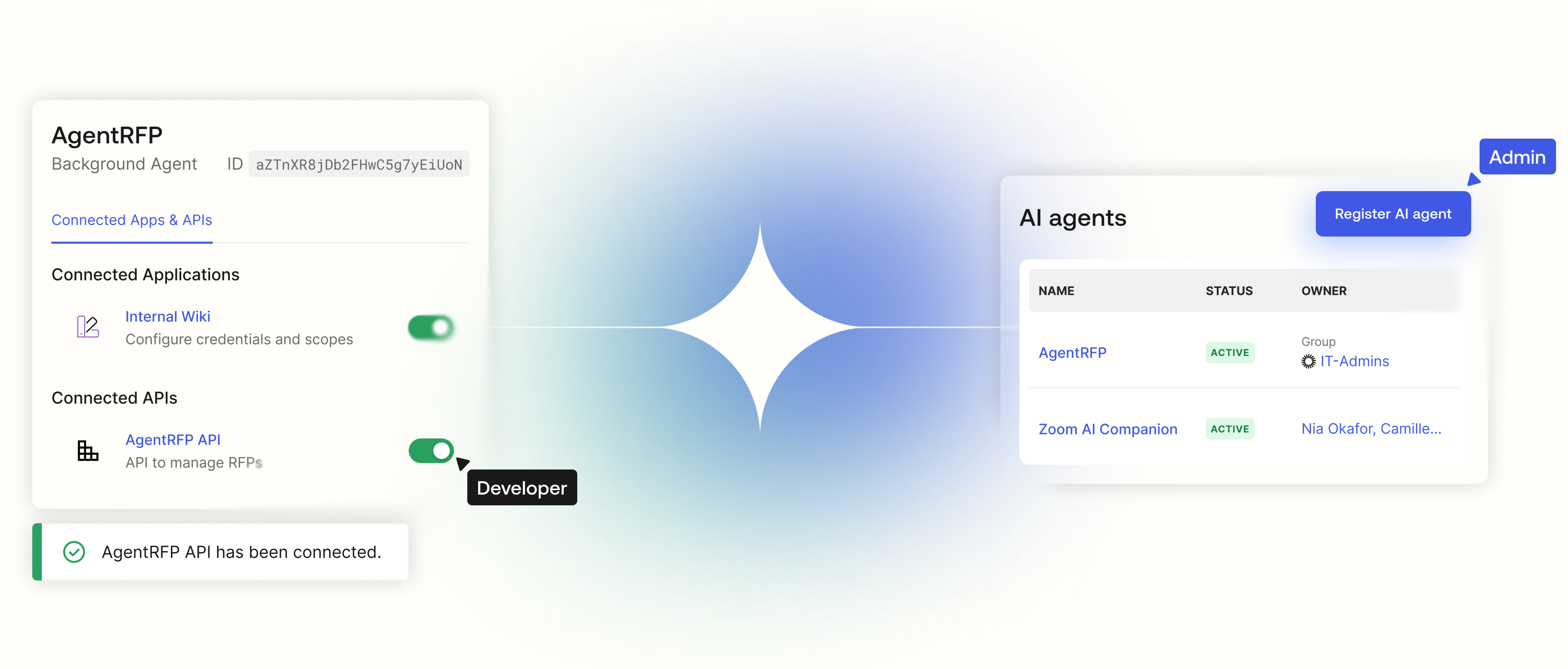
Govern agents from day one
Whether you build your agents or deploy vendor solutions, secure the entire lifecycle—from creation to retirement—on the platform built for developers, security, and IT.
FOR DEVELOPERS
Build AI safely from the start
Secure agents by design, whether they serve your workforce or your customers.

Enable agents to verify who they are acting on behalf of. Pass verified user context to your agents to maintain trust and accountability.
Seamlessly connect agents to third-party tools. Automate the handling of access and refresh tokens to reduce credential sprawl.
Execute high-stakes decisions with confidence. Pause long-running workflows automatically for human approval.
Protect sensitive data in your RAG pipelines. Enforce granular permissions so agents only access what is necessary.
FOR SECURITY & IT TEAMS
Manage your AI workforce at scale
Automate the full lifecycle for your non-human workforce from a single control plane.

Automatically expose unmanaged agents running in your stack to help eliminate blind spots.

Enforce accountability by registering agents in the directory with a mandatory human owner.

Prevent helpful bots from becoming insider threats by enforcing strict least-privilege scopes.

Monitor activity and detect threats in real time. Validate permissions and instantly revoke access if an agent acts suspiciously.
AI SECURITY BLOG SERIES
Building autonomous trust at machine speed
Resources
Frequently asked questions
Identity security is critical because AI agents can act as autonomous “super admins” capable of accessing sensitive data and executing tasks without constant human oversight.
Securing agents requires treating them as first-class identities with strict authentication, authorization, and governance to help prevent them from becoming insider threats.
The rapid adoption of AI has outpaced governance, creating significant “Shadow AI” risks. Key threats include unintended agent behavior (experienced by 80% of organizations*), credential exposure (reported by 23% of organizations*), and a lack of visibility into where agents exist.
Furthermore, poorly managed agents often have over-privileged access, allowing them to reason over enterprise data they shouldn’t be able to touch.
Securing the AI agent lifecycle requires a two-pronged approach: build and manage.
Build (secure by design): Developers should use tools like Auth0 to embed identity standards—such as fine-grained authorization and token vaulting—directly into the agent's code.
Manage (secure control plane): Security teams must use a unified platform like Okta to detect running agents, register them in a directory, and govern their access policies and lifecycle events.
An identity security fabric is an architecture that gives IT and Security teams a unified control plane that manages every identity type—human and non-human—to help prevent security gaps. As AI agents effectively become part of the workforce, they must be brought into this fabric.
This approach eliminates “swivel chair security” by unifying governance, privileged access, and identity management, ensuring that a policy applied to a human employee can also be enforced for an autonomous agent.
Cross App Access is a new standard protocol designed to secure how AI agents connect to critical applications without compromising user experience.
It replaces risky, unmanaged integrations and ad-hoc user consent prompts with policy-based access decisions managed by the identity provider. This gives enterprise admins visibility and control over agent connections while eliminating consent fatigue for end-users.









