AI is evolving fast. Look no further than the latest headlines and announcements: OpenAI turned ChatGPT into a platform for in-chat apps and autonomous agents. Anthropic released Claude Sonnet 4.5, capable of reasoning across multi-hour tasks. Google’s Gemini can now navigate the web like a person, and Microsoft’s Copilot ecosystem has multiplied into a network of embedded agents across Windows and Office.
Together, these announcements mark a turning point (and will probably be woefully out of date by the time you read this). AI is moving far beyond chatbots that answer questions. It’s becoming an active participant in how we live and work.
Unlike humans, AI doesn’t clock out or forget. Agents can persist quietly in your systems, holding access long after their purpose ends. Without governance, these identities operate unseen — and in security, what’s unseen is what’s vulnerable.
Why our traditional identity infrastructure won’t cut it for AI agents
Traditional identity systems were built for people: employees, partners, and contractors. But AI introduces new identity challenges that don’t fit into that model.
| Challenge | Human Identities | AI Identities |
|---|---|---|
| Volume | Stable workforce size | Thousands of dynamic, short-lived agents |
| Visibility | Managed via HR or directories | Hidden in APIs, pipelines, and automations |
| Accountability | Tied to a person’s credentials | Often lacks clear ownership or traceability |
As AI adoption grows, ungoverned agents lead to shadow access and compliance gaps with access no one monitors, but everyone is responsible for.
How do you govern an AI agent identity?
To manage and govern AI agent identities, you need visibility, accountability, and control. With the right identity security playbook in place, you have everything you need.
It ensures every AI identity is:
- Known — you can identify every AI agent operating in your environment.
- Owned — a human is assigned to each agent and is responsible for its behavior and access.
- Scoped — permissions are limited to a clear purpose and timeframe.
- Auditable — every action is logged and traceable.
- Revocable — when the task ends, access ends.
Identity doesn’t stop with humans anymore — it extends to the AI that acts on their behalf.
Thousands of use cases, but the fundamentals remain the same
At Okta, we talk to customers every day who are in various stages of deploying AI agents in their organizations. While the use cases are different, securing the agents all start with getting identity right:
| Use Case | Goal | Example |
|---|---|---|
| Customer Support Agents | Prevent overexposure of PII | Agent can read customer data but not export it |
| Developer Copilots | Limit system access | AI assistant can read internal repos, not write to production |
| Procurement Agents | Maintain accountability | AI can create a purchase request but requires human approval |
| Research Models | Protect sensitive data | Model uses synthetic datasets, not live customer data |
Secure Your AI Agents Using a Maturity Model
Organizations can assess their readiness with Okta’s AI Agent Security Maturity Model. It defines four stages to help you secure and govern AI identities at every level.
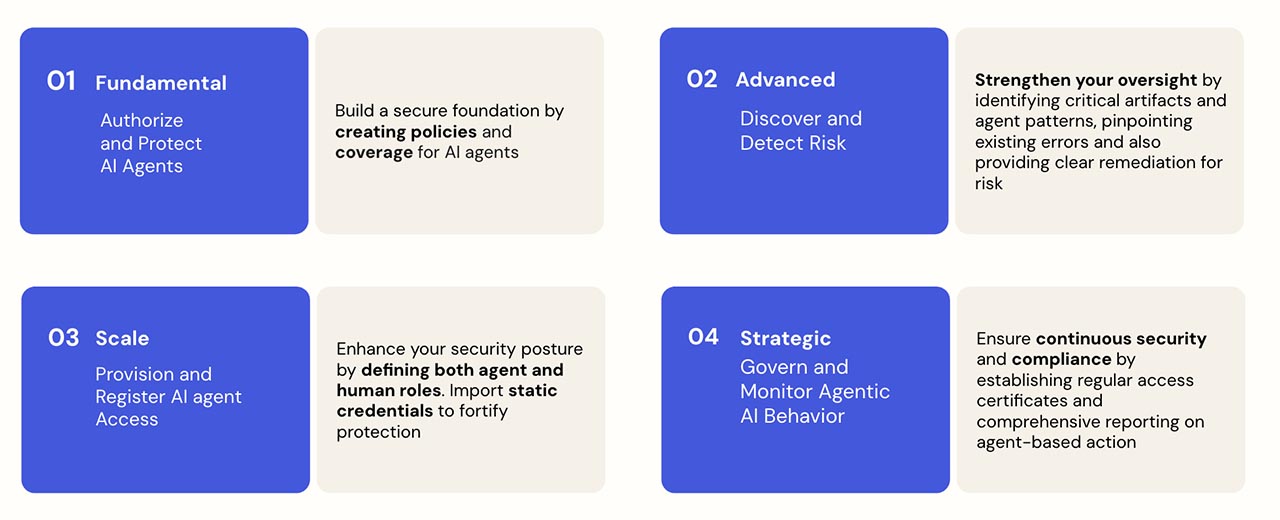
Unsure where to start? We’ve got a checklist to help.
Step 1: Inventory AI identities
Catalog every AI agent, model, or automation that touches sensitive systems.
Step 2: Assign human owners
Each AI identity should map to a responsible person or team.
Step 3: Apply least privilege
Grant access for only what’s needed, using just-in-time tokens when possible.
Step 4: Include AI in access reviews
Treat AI accounts like human ones — review and certify them regularly.
Step 5: Automate lifecycle management
Use workflows to provision, update, and deprovision AI identities automatically.
Governance is continuous. The earlier you start, the easier it becomes to maintain control as AI scales.
Need some help checking these things off your list? Learn more about how Okta helps you see, manage, and secure AI agents in your organization.
These materials are for general informational purposes only and do not constitute legal, privacy, security, compliance, or business advice.
The content may not reflect the most current security, legal and/or privacy developments. You are solely responsible for obtaining advice from your own legal and/or professional advisor and should not rely on these materials.
Okta makes no representations or warranties regarding this content and is not liable for any loss or damages resulting from your implementation of these recommendations. Information on Okta’s contractual assurances to its customers may be found at okta.com/agreements.






