Okta Device Trust: Get the Most out of Integrating Identity + Endpoint Management
The current state of device based access control
It's no secret that devices have changed the way we work. Mobility has transformed the enterprise enough to redefine the term "mobile device." With modern management techniques for mobile form factors as well as laptops and tablets, the traditional desktop device can now be considered "mobile." However, the large variety of mobile and desktop devices available to us introduces new challenges: How do you secure BYOD? What device management tools are you using for different OS platforms? What types of compliance and/or security settings do you require for on vs. off network access?
Unfortunately, organisations have a difficult time ensuring their existing defenses keep pace with mobile security threats. The Verizon Mobile Security Index 2019 tells us that 67% of respondents said they are less confident about the security of their mobile assets than other devices.
Fortunately, this is where Okta's device trust can help.
Introducing Okta device trust for all major platforms
We're excited to announce that Okta device trust is available in production for all major platforms—Windows, MacOS, iOS, and Android. We have made significant investments to ensure that customers can utilise device trust regardless of the combination of endpoint management tools in your organisation. This means that if you're using different tools for desktop vs. mobile management, you can keep your existing tools in place, while still ensuring device security. Keep reading for more details on what this means for your organisation.
What exactly does device trust mean with Okta?
It starts with device context—specifically, the various levels of security controls that can be enforced on different device platforms. Typically, enterprises are most concerned with the validation of known and/or managed devices. And, the managed state of a device usually indicates a certain level of security or compliance settings enforced by your endpoint management tool.
Today, Okta's device trust solution specifically refers to the ability to enforce device management—that is, ensuring that a device is managed by an endpoint management tool before end users can access Okta managed apps. On mobile platforms, this means the device has a management profile installed on it. On desktops (Windows and MacOS), this typically means the device is managed by an agent-based endpoint management tool or managed via a mobile device management profile (think Jamf, System Center, BigFix, Workspace ONE, etc.).
To put this into context, here are a few examples of what an enterprise device management setup with device trust could include:
- Enforcing that any MacOS device accessing Okta managed apps is managed by Jamf Pro
- Enforcing that any iOS and/or Android device accessing Okta managed apps is managed by Workspace ONE (previously Airwatch)
- Enforcing that any Windows device accessing Okta managed apps is joined to your on-prem Active Directory and managed by System Center Configuration Manager or BigFix
These are just a few possibilities, but this list can vary based on the endpoint management tools you may be using. This is where Okta's device trust shines — even if you're using a combination of endpoint management tools for desktop vs. mobile platforms, or in the process of migrating off one solution to another, you can always ensure that your devices are managed before end users access corporate resources.
In the future, Okta's definition of device trust will expand to include capabilities such as lightweight device management checks, and passing on device context to other apps to further enforce security settings at a per-app level, but for this post, we’ll focus on managed devices.
How is Okta device trust different from the rest?
You may have noticed similar solutions from other vendors. However, not all solutions are built equal. Here are some benefits you’ll get when choosing Okta for device trust vs. the rest:
- Okta’s approach is vendor-agnostic, so we don’t limit you to using a specific endpoint management tool to enforce device security on mobile and desktop devices
- Our technical approach has ensured that device trust is supported for any SAML or WS-Fed application, so we are not focused on just a specific set of apps
- A passwordless login experience for all platforms, when accessing any set of applications
- The ability to combine device trust with Okta’s other adaptive authentication policies to ensure you are always delivering a seamless, secure access experience
The technical details of device trust
Now that you're familiar with Okta's definition of device trust, let's go through the technical details on how we assess the managed state of a device. We’ll keep this simple by putting device trust into two categories. Keep in mind that you can deploy a combination of these two options based on what makes the most sense for your organisation.:
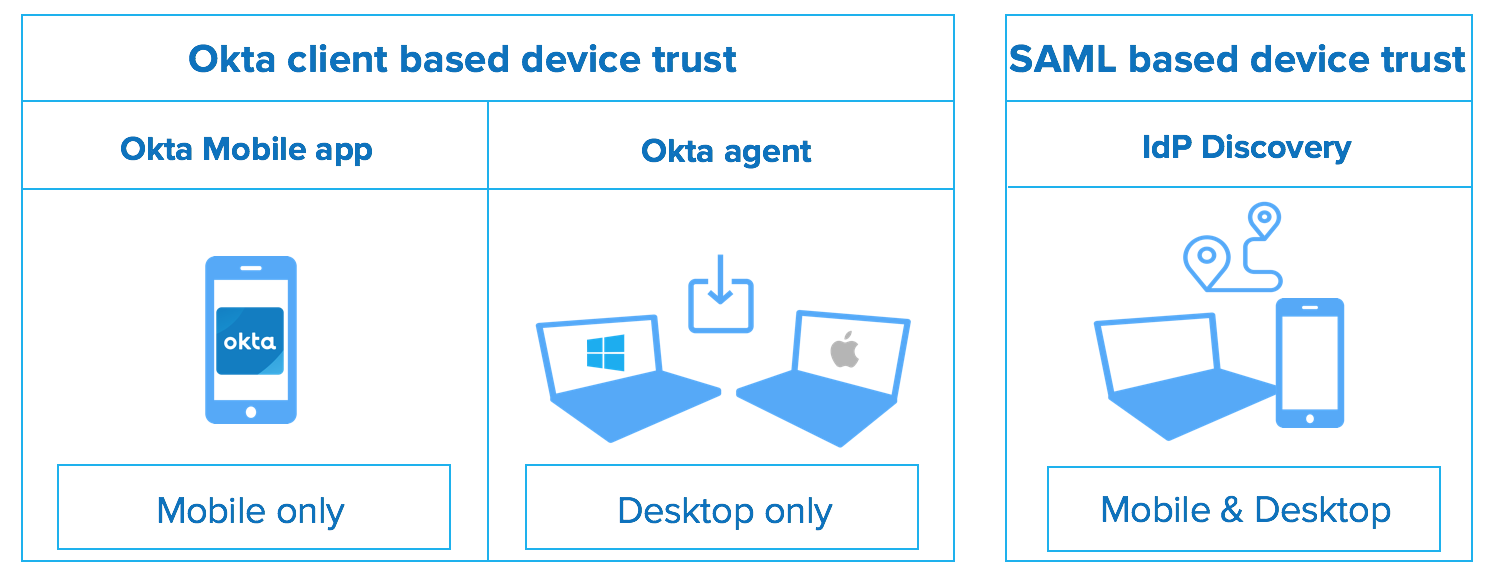
1. Okta client based device trust
With this option, you utilise Okta built software to assess the managed state of a device. Since there are nuances in how this works on desktop vs. mobile, the technical approaches that we take on desktop vs. mobile platforms differ.
Desktop (Windows and MacOS) - Assess managed state via an Okta agent
On Windows and MacOS, administrators deploy a lightweight Okta agent to each endpoint. This can be done using your endpoint management tool. This installer serves two purposes: (1) it deploys an Okta CA issued certificate to the device, and (2) it creates a scheduled task to check the validity of the certificate, indicating whether the device is trusted.
On Windows, Okta will consider the device to be trusted if it is joined to on-prem Active Directory. The installer will start a process of checking the AD domain joined state, deploy the certificate, and create a scheduled task.
On MacOS, Okta will consider the device to be trusted if it is managed by Jamf Pro (no dependency on Active Directory for MacOS). With this solution, Okta first checks if the device ID exists in Jamf. If it does, the installer will deploy the certificate and create a scheduled task.
Mobile (iOS and Android) - Assess managed state via the Okta Mobile app
As mentioned before, we offer a vendor-agnostic approach to device trust which will work with any endpoint management solution that supports managed app configuration. Managed app configuration is the ability to deploy native mobile apps to end users’ devices with preconfigured settings. With this solution, Okta Mobile serves as a broker application to check if the device is managed. In the Okta admin console, you will generate a secret key value tied to your Okta org. Then, you'll use your endpoint management tool to deploy the Okta Mobile app with a managed app configuration setting called “managementHint”. The presence of the Okta Mobile app deployed with this secret key value tells Okta that the device is managed so the end user will be able to access Okta managed applications.
That sums up the Okta client based approach to device trust.
2. SAML based device trust
This approach uses a feature within Okta called IdP Discovery to help assess the managed state of a device. With this approach, your endpoint management tool must also include an identity service in their offering. Examples of these types of endpoint management tools include VMware Workspace ONE, UEM, and MobileIron Access.
Using IdP Discovery, Okta can pass the login off to the endpoint management tool. The endpoint management tool then checks if the device is managed, enforces any required device compliance policies, and sends the login back to Okta once the enrollment process is complete. Alternatively, you can set a policy to deny access altogether, or require Okta MFA if the device is unmanaged.
For device trust to work, Okta gets added as an app in the endpoint management tool’s service, and the endpoint management tool’s IdP is added in Okta. Okta still remains the SSO provider for all your applications. We just use the endpoint management tool’s device management check capabilities. As long as the endpoint management tool supports checking for the managed device state across all platforms, this approach works on both desktop and mobile because IdP Discovery can route logins for individual desktop and mobile platforms over to another IdP.
This means that the SAML based device trust approach supports Windows, MacOS, Android, iOS, and any other platform that may be supported by your endpoint management solution.
That sums up the SAML based approach to device trust.
How do I know which option is right for me?
You can use a combination of these options based on the endpoint management tools and platforms deployed in your organisation.
Here's a diagram that depicts the high level options available.
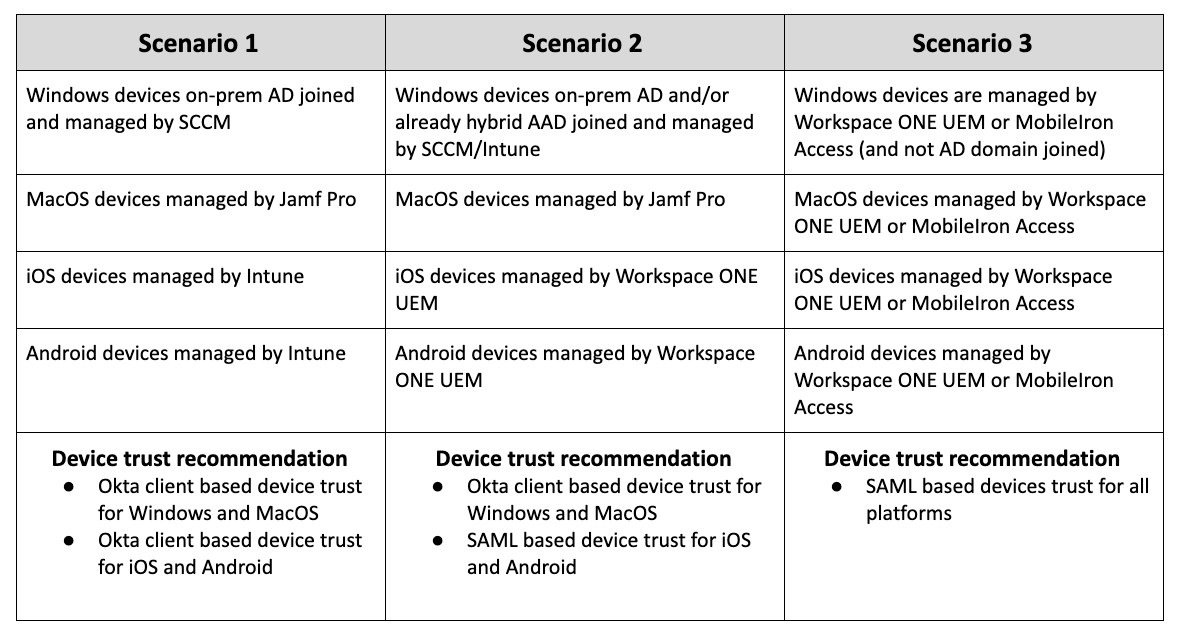
Based on the combination of endpoint management tools you have deployed, you can make a decision about which methods of device trust are the most appropriate. Here are a few examples:
How can I get started with device trust?
Here’s an overview of what is available in production with device trust today:
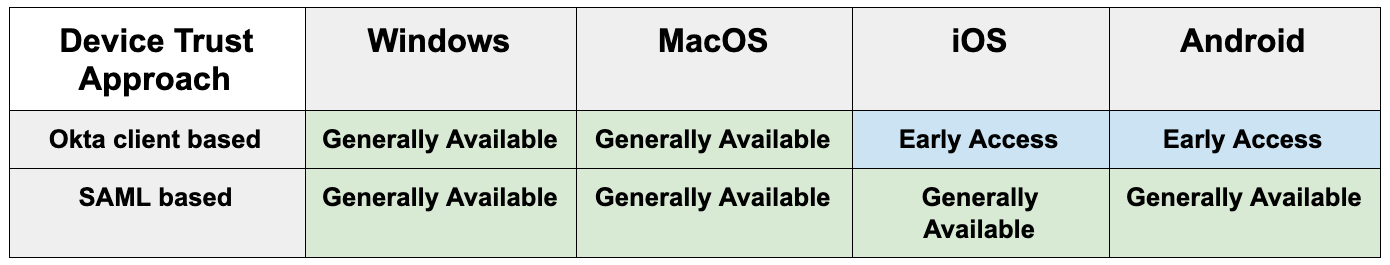
In order to utilise device trust for Okta, you will need either Adaptive MFA or Adaptive SSO enabled in your Okta org.
To get started, you can follow these steps:
1. Contact Okta Support to enable any Early Access features. Features that are Generally Available should already be enabled in your Okta tenant.
2. Decide which device trust approach makes the most sense for your organisation (Okta client based vs. SAML based).
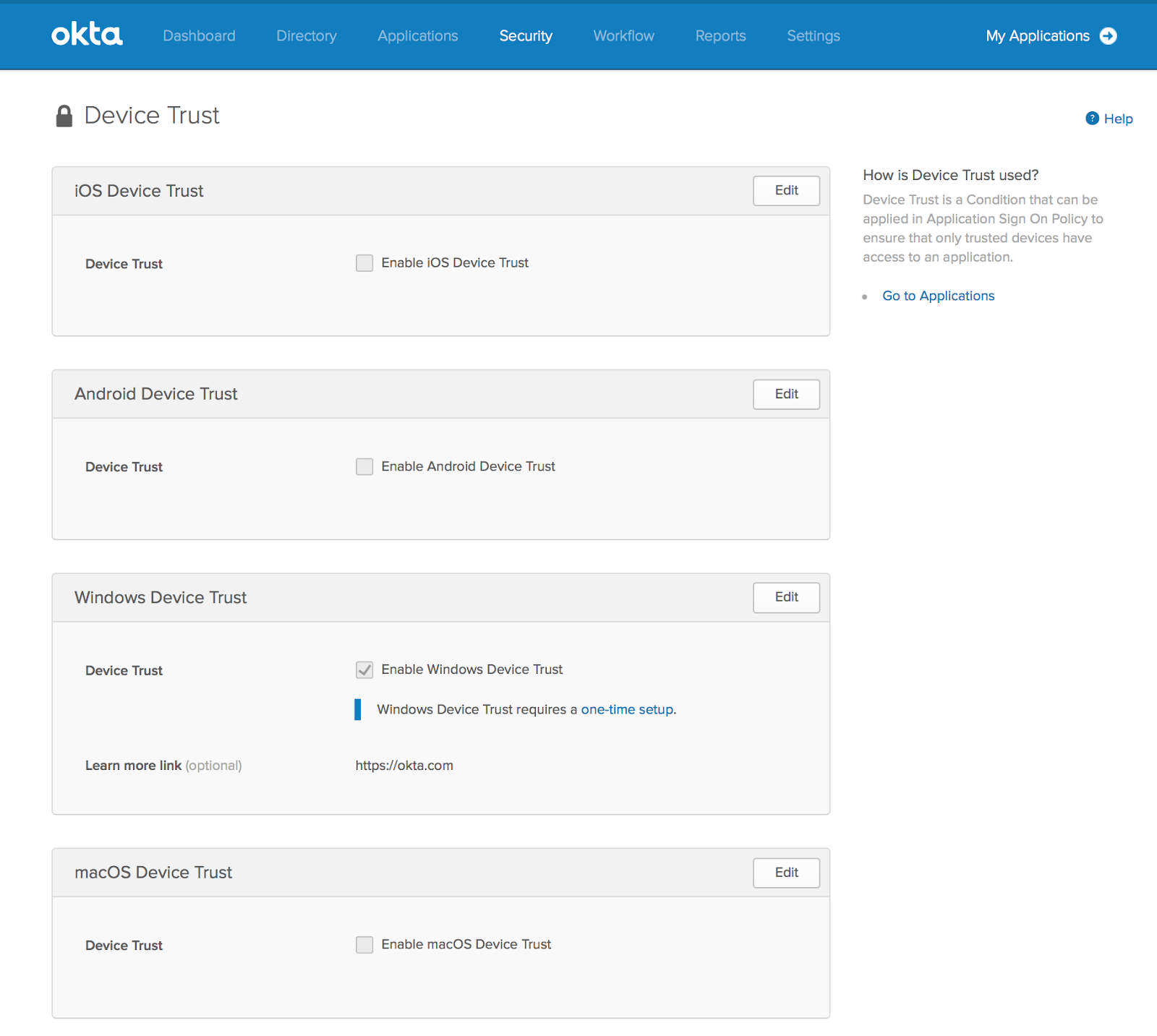
3.In the Okta admin console, go to Security - Device Trust, and enable the platforms that you will be enforcing device trust on.
4. Choose the applications that you need to enforce device trust on. The policy for device trust is set at a per-app level in Okta.
Example:
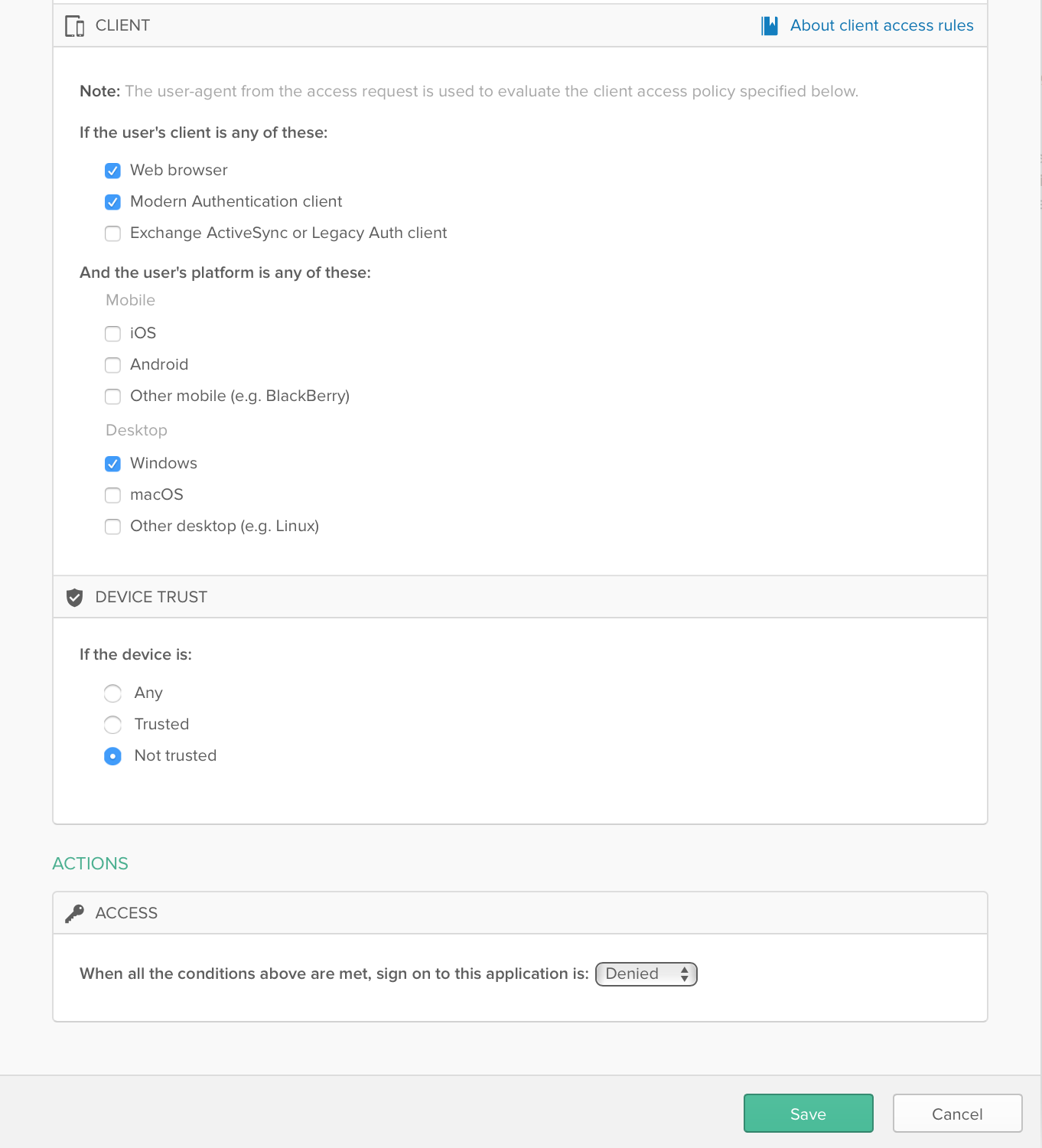
Follow the steps in our product documentation based on which device trust approach you decide on:
Okta client based
SAML based
- VMware Workspace ONE (partner page available here)
- MobileIron Access (partner page available here)
Learn more
Please see the device trust product documentation for details on these topics, including supported architectures, prerequisites, and known limitations for the solutions mentioned in this post.
Visit our VMware and MobileIron partner pages for more information on the benefits of integrating these solutions with Okta.

