Simplify communication between APIs and trusted services
Easily handle authentication and authorisation for non-interactive applications with machine-to-machine communication from Okta Customer Identity Cloud, powered by Auth0.

Trusted interactions for APIs and applications
Enable secure access to your API from other internal or external non-interactive third party-apps with minimal configuration.

Internet of Things (IoT)
Use the identity of the IoT device instead of a user identity to streamline a secure IoT implementation
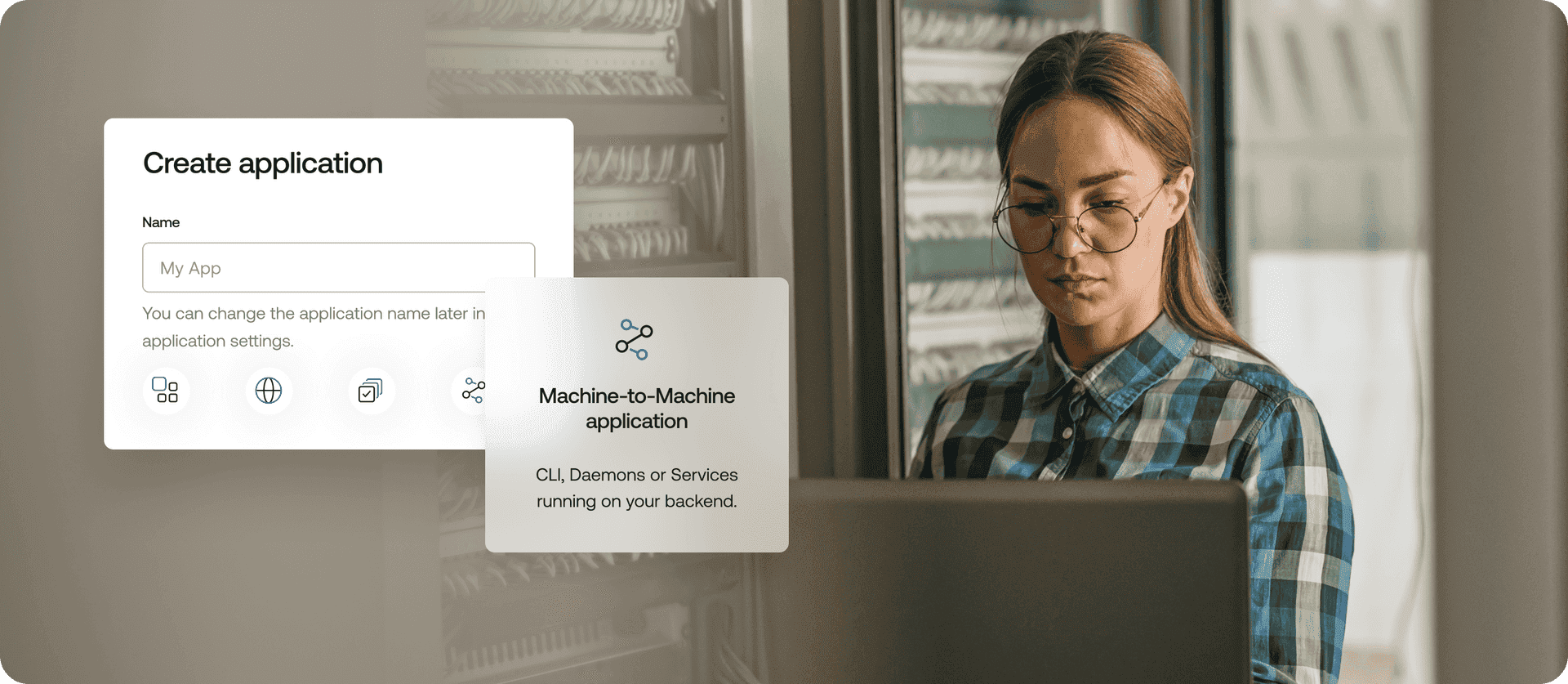
Secure API authentication for non-interactive apps
Allow non-interactive applications such as app servers, command line interfaces (CLIs), daemons, and others to safely and securely consume your API in cases where no human interaction is necessary.

Enable app servers, APIs, and services to make authenticated requests to your API without the need of human interaction.

Build powerful tools and CLIs that can connect and authenticate to your APIs.

Let job schedulers, daemons, and other system processes securely interact with your API.

Easily control internal and external clients’ access levels to your API with highly granular permissions.
- Application backends
- Command line interfaces
- Other processes

Standards-based security
Rest easy knowing your API is protected with open standards through the use of the OAuth2 Client Credentials grant flow for secure communications.