Only members of the DevOps team can access the servers in the CI/CD cluster, and only members of the Data team can access the servers in the Database cluster. You can restrict privileged commands for the Data team, so they can only perform actions related to their job.
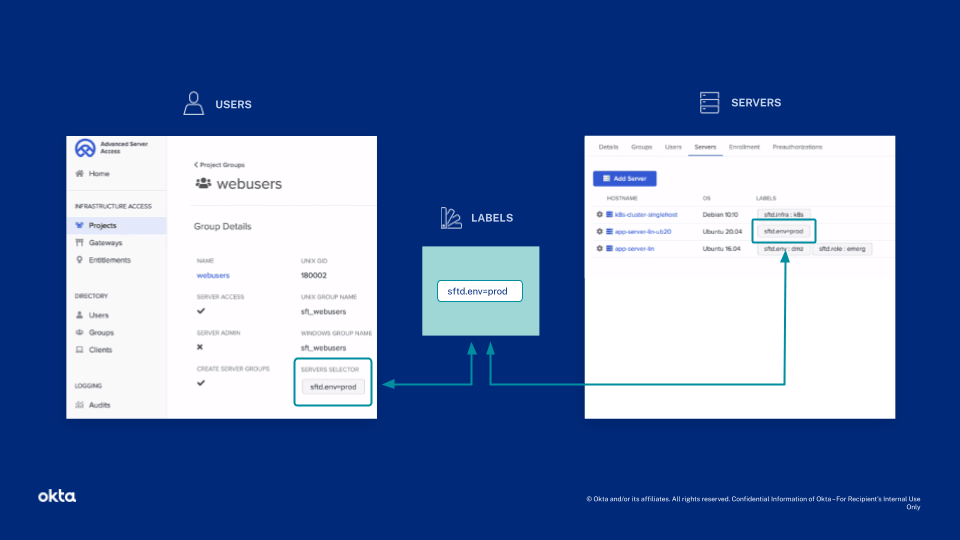
Additionally, you can apply group assignments to labels, which you can configure or import from AWS. For example, you may have several servers that handle payment processing and are subject to PCI-DSS guidelines. You can assign these servers fine-grained control, across all projects, based on a label name.