What Is SOC Compliance?
SOC is a set of standards that allow companies to demonstrate they are managing and regulating information properly. SOC stands for “service and organisation controls;” developed by the American Institute of Certified Public Accountants (AICPA), these regulations exist to give companies peace of mind when exchanging customer data with third-party vendors.
Of the available SOC audits, SOC 2 compliance is the most thorough—and the most relevant to companies storing customer data in the cloud.
What differentiates SOC 2?
SOC compliance nets out in a variety of reports depending on a company’s unique requirements. There are three main SOC assessments:
- SOC 1 focuses on auditing internal financial controls and the reliability of financial reporting.
- SOC 2 is a technical audit that tests whether a businesses’ systems are appropriately set up to ensure the security, availability, processing integrity, confidentiality, and privacy of customer data.
- SOC 3 is designed to give users reassurance on the controls of the business without the granularity of a SOC 2. A SOC 3 is ideal for public distribution.
The growing trend towards cloud computing has made SOC 2 reports a necessity for many businesses. SOC 2 is the preferred technical auditing procedure for businesses that manage and store customer data. Unlike the rigid regulations of requirements like Payment Card Industry Data Security Standards (PCI-DSS), SOC 2 reports are tailored to each organisation. A SOC 2 audit requires comprehensive information regarding security policies and procedures to be documented and followed, and is a minimum requirement to fulfill when offering SaaS products and services.
AICPA’s Generally Accepted Privacy Principles
An organisation’s privacy controls need to, at minimum, follow the AICPA’s Generally Accepted Privacy Principles (GAPP), which is a global privacy framework that helps organisations create an effective privacy program. It provides 10 best practice principles companies should know and adhere to:
- Management: This principle ensures businesses define, document, communicate, and assign accountability for their privacy policies and procedures. It advises carrying out personal information surveys to identify what information businesses collect and store.
- Notice: Businesses need to provide notice about their privacy policies and procedures and identify why personal information is collected, used, retained, and disclosed.
- Choice and consent: Companies must provide customers with implicit or explicit consent to the collection, use, and disclosure of their personal information.
- Collection: Organisations must only collect personal information for the purposes it originally provided.
- Use, retention, and disposal: Businesses can only use and retain personal information for the purposes that were outlined when the customer provided implicit or explicit consent, after which it must irreversibly dispose of the information.
- Access: Businesses must be able to provide customers with access to review and update their personal information.
- Disclosure to third parties: This principle ensures that businesses only disclose personal information to third parties for the purposes identified and with the customer’s implicit or explicit consent.
- Security for privacy: Organisations must protect the customers’ personal information from unauthorised physical and electronic access. This includes the secure storage of paper documents and ensuring appropriate security measures are in place on devices to monitor and prevent data breaches.
- Quality: Businesses must maintain accurate, complete, and relevant personal information for the purposes provided.
- Monitoring and enforcement: Businesses need to monitor compliance with privacy policies and procedures and ensure processes are in place to address privacy complaints and disputes.
What are the components of SOC 2 compliance?
SOC 2 compliance applies to any technology-based service organisation that stores customer data in the cloud. It, therefore, applies to every SaaS company and any business that stores customer information in a cloud-based system.
A SOC 2 audit includes two report variations, Type 1 and Type 2.
- A SOC 2 Type 1 report focuses on the security principles, systems, and controls a business has in place to mitigate security risks at a specific point in time.
- A SOC 2 Type 2 report details the operational effectiveness of those systems and controls and how they are structured and implemented over a period of time.
SOC 2 compliance focuses specifically on the five Trust Services Criteria (TSC) principles:
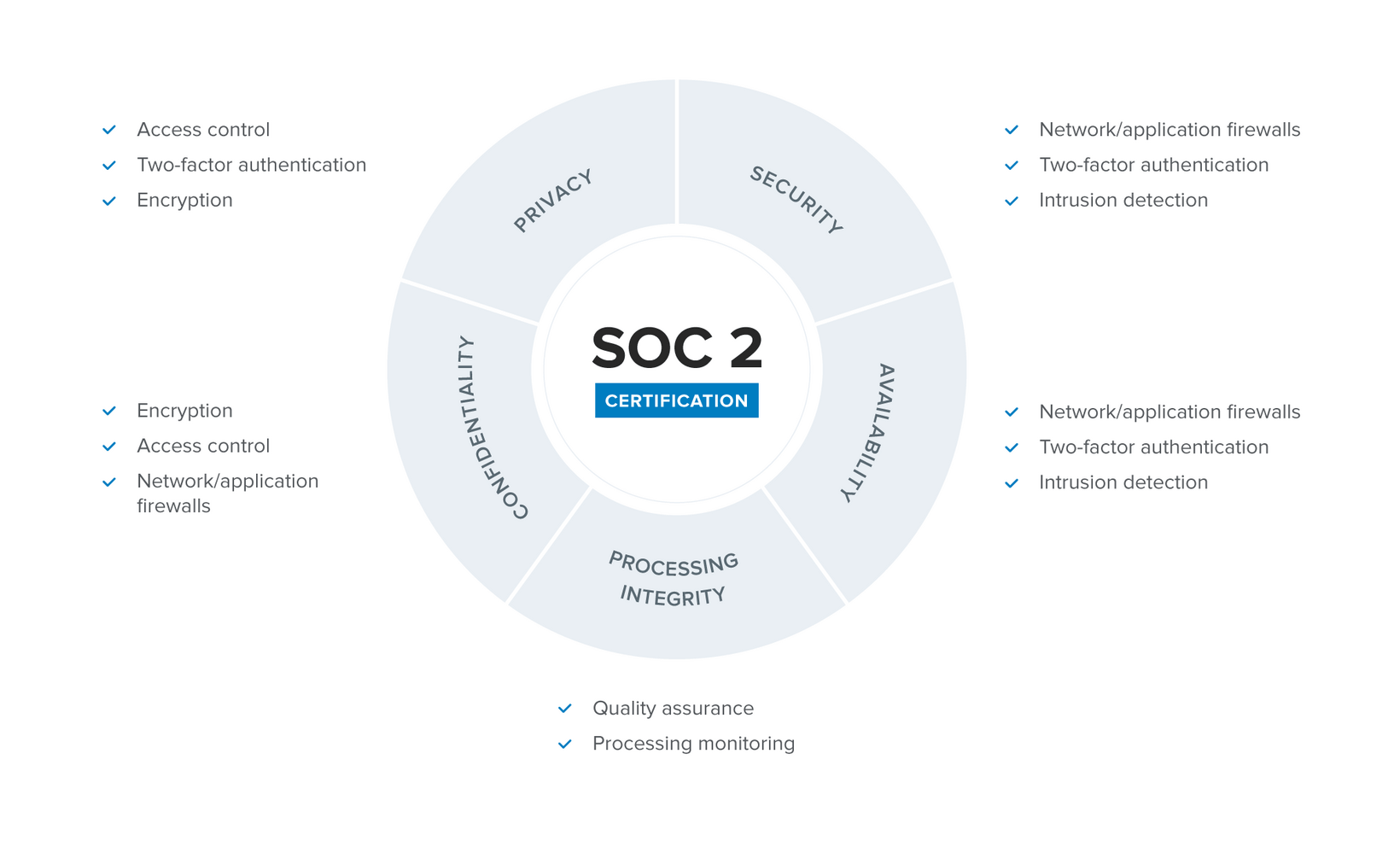
- Security: A SOC 2 audit focuses on both physical and electronic security. It examines whether business premises and systems are protected from unauthorised access and if there are controls in place that will alert enterprises in the event of suspicious activity.
- Availability: This part of the SOC 2 audit ensures businesses are able to access their systems as outlined in their contractual specifications.
- Processing integrity: SOC 2 compliance aims to ensure that any company that offers financial or eCommerce transactions has controls that safeguard those transactions. This includes encrypted sessions for transactions on mobile devices and the ability to audit how customers access the services that the company provides, whether through a data repository or a hosting platform.
- Confidentiality: The SOC 2 audit assesses whether an organisation has restrictions in place on how data is shared. This includes documenting guidelines around dealing with personally identifiable information or protected health information, as well as details around how data is accessed, stored, and transferred.
- Privacy: The privacy section of SOC 2 compliance focuses on how an organisation collects and uses customer information and assesses whether the privacy policy in place aligns with operational procedures. For example, if a company claims to alert customers when it collects data, then they must document how this is done.
Why is SOC 2 compliance important?
Any company that stores customer data in the cloud must comply with SOC 2 audit to ensure they minimise risk and prevent that data from being exposed. The five TSC principles are crucial to establishing customer trust and ensuring the right practices and procedures are in place and in line with other data protection regulations.
SOC 2 helps businesses to deploy well-defined, ongoing policies, procedures, and practices, as opposed to simply being a compliance box-ticking exercise. This instills trust in customers and end users that the organisation is secure and operates cloud infrastructure that will keep their data safe.
A SOC review ensures businesses have detailed audit trails that provide deep context and enable them to conduct effective security operations. It also puts organisations in a position to effectively discover malicious, suspicious, or unauthorised activity across their networks, processes, and systems, by establishing a continuous security monitoring service.
What’s included in a SOC 2 report?
Upon the completion of a SOC 2 compliance audit, companies receive a report that verifies they’ve done everything required towards minimising security risks and addressing their privacy requirements. The report is broken down into seven sections:
- Assertion Report: Details the company’s security controls in relation to the five TSC principles outlined above.
- Independent Auditor’s Report: Explains how effective the auditors deemed the controls the business has in place.
- System Overview Report: Provides an overview of how service organisations interact with the business.
- Infrastructure Report: Provides a detailed report of the organisation’s environment, including software, procedures, people, and data.
- Relevant Aspects of Control Report: Analyses how the risk assessment was conducted, the effectiveness of the business’ communication procedures, and the monitoring controls it has in place to track security systems and usage.
- Complementary User-Entity Controls Report: Outlines the security protocols that the business has in place to protect its user environment and platforms.
- Test of Controls Report: Analyses the performance of the business’s controls and outlines whether the auditor deemed them effective enough to meet the TSC principles.
SOC 2 certification
While technically an attestation report, a clean SOC 2 audit is often still referred to as certification, and is issued by auditors from outside your organisation. The audit is based on one or more of the TSC principles, and the external CPA firm issues Type 1 and/or Type 2 reports of the business’s design and controls. In other words: management makes the assertion that controls are in place that align with SOC 2 criteria, and auditors report back on whether they’ve found these claims to be supported. Every time a business completes a SOC 2 report, it will contain an opinion from the accounting firm on whether or not it agrees that the appropriate controls are in place.
SOC 2 and remote work
SOC 2 compliance is more important than ever with businesses operating fully remote workforces. The guidelines for SOC 2 haven’t changed since they were written well over a decade ago, but the procedures that businesses are adopting to enable remote work are constantly evolving.
With more cloud adoption, these environments are more dynamic than ever, meaning the controls need to be 'cloud-aware' in their capabilities. It’s therefore vital for organisations to constantly monitor physical and electronic systems and networks. This includes managing access controls to systems, and having alerts in place for potential malicious activity.
A good example of meeting SOC 2 compliance standards while supporting remote teams is the need to protect all devices and endpoints regardless of location. To do this, businesses need to deploy multi-factor authentication policies that account for the context of each authentication request.
Remote working doesn’t need to make meeting compliance standards more difficult. Admins can manage and provision users to the applications and networks they need remotely through tools like SAML, and just-in-time and SCIM provisioning.
Identity and SOC 2
Identity sits at the heart of SOC 2 compliance. People are the new perimeter for all businesses, especially those with a distributed workforce: it’s vital to have measures in place that guarantee only the right people have the right level of access to the right information at the right time.
Businesses are already tracking and managing how teams access and engage with data and company services, laying a strong identity foundation for SOC 2 compliance.
- For example, the audit logs that businesses owe to their auditors every quarter already have to include information like how administrative accounts and credentials are protected and who has access to software and servers. SOC 2 compliance is simply the next step.
- The security of applications and underlying infrastructure is also vital for software companies: SOC 2 guidelines help them to ensure the security of software development. Quarterly audit logs help businesses to satisfy their audit requirements while confirming that their data is safe and secure.
Find out how Okta adheres to the SOC compliance guidelines and provides the identity solutions businesses need to achieve their own compliance goals.

