The Power of SCIM: Reduce Security Risks and Automate User App Provisioning
Transcript
Details
Sara Daqiq: Thanks for coming everybody. My name is Sara, as Joe mentioned, and I will be presenting and talking to you guys about SCIM. Let's just cut to the chase and talk about SCIM.
Okay. So this is our agenda, what we're going to talk about today. SCIM is going to talk about the challenges that people have faced with SCIM and without SCIM, and how SCIM has designed to solve those challenges. We're going to talk about the case study with our partners at LendingClub and how they have been using SCIM, and at the end we're going to have a QA session that's going to be open for the audience.
Let's just cut to the chase and see what SCIM is. Okay. So, what problem does SCIM solve? Maintaining identities between different platforms has been very time consuming, expensive, and really labor-intensive. So, what that means is, that SCIM is going to solve these problems for us, and we're going to address how SCIM does that.
First of all, let's know what SCIM is. Okay. SCIM stands for "System for Cross Domain Identity Management". It automates user provisioning. So when a user ... When in today's increasingly cloud-centric environments, organization opts into having their identity stored in a different platform, usually called "identity provider" and then you will have ... their customer, or their application service provider will talk to those identity providers.
So SCIM in very short, or very in sync sentence, keeps the user profile, and the identity provider in sync with the user profile and the service provider. If you get anything from this presentation that is, that SCIM keeps the user profile, and the identity provider in sync with the user profile and the service provider, or your application in this case.
So just to reiterate, identity providers are the application, the user profile, or user storage or platform, that uses, or saves users, and that your service provider is the application that you use.
Okay. So, let's cut a little deeper into that. In this slide you see that is our identity provider in this case is Okta. Okta provides the identity, and they say this is your organization. Your organization have a couple of obligations that they want to have a copy of the user profile. What they will do is that Okta will ... If you want a copy of the user profile in your application, you will create a SCIM server. A SCIM server creates a copy or updates and maintains all the user information data in your application. So how to do it ... Let's say in here, the user has created an application and is assigned to that application, and then SCIM creates copies off that in your system, and vice versa. So, let's say a user gets deleted, or a user gets updated in your application, it's going to be updated in the Okta as well.
So let's dive into an example, shall we? So in here it's the same concept, but a different perspective. So let's say, in here you have your Okta dashboard, and then you have your application here. Tom, for example, is doing contract work for you guys for, let's say, two months. So Tom is in your organization for two months, and you guys are obviously trying to pay him. What happens is that when Tom tries to ... The first thing that you need to do is to assign Tom to the application, and as soon as you assign Tom to that application, the payroll application, a user, or a copy of Tom, a user is going to be created in the payroll application. So that will create a username and ID for Tom, and Tom can access that payroll application.
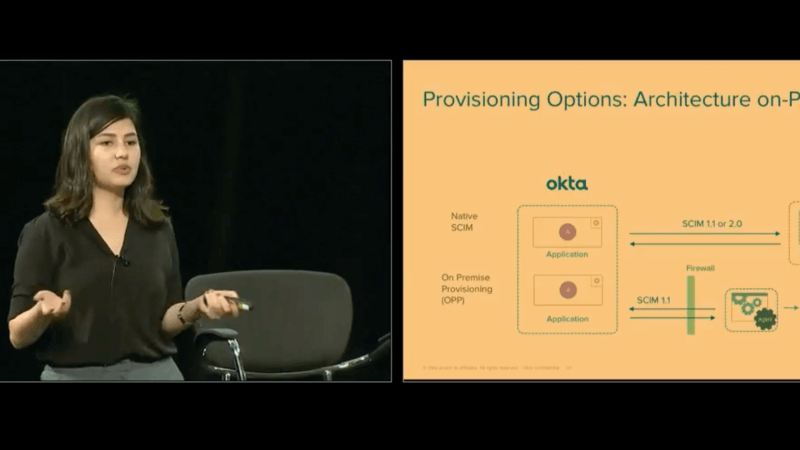
So, let's say in two months Tom has done his job, and he leaves, you de-assign, or unassign Tom from your application at Okta. It will deprovision the user in your application. And in that case, Tom does not exist and cannot access the application anymore. So that's basically the gist of it. Let's say you have an application that's behind a firewall, right? This is all on cloud. Let's say you have an application that's behind a firewall. How would SCIM support that? Well wonder no more because SCIM does support that. The only structure that you need to change is download an agent and have a connector.
So Okta itself has a Java SDK, and the Java SDK and the user ... the application is going to talk to each other. The same thing will happen, Tom is going to get assigned to the application and then get updated to agent. Agent talks to the SDK and creates the user in the database. It goes the other way around as well. If you update Tom's information, let's say bank account, in your application, that's going to be updated, and I'll do it in the user in your Identity provider or Okta in this case.
The cool thing about this is that, this application is not piercing through the firewall, instead it's working with the firewall to make this happen. So it's not just discarding all the data that the firewall had, or all the securities that the firewall had, it just goes through a call period with it.
Okay. Now that we have that, let's see what were the problems that people had before. So let's say, 20, 30 years ago, when people didn't have SCIM model data, right? Okay. So the first thing was the manual entry. So how that works is that you'll have a user and identity provider, and then you would create another user in your service provider, and then you will try to keep them in sync manually. The problem with that is that if you're like me, or your Joe right here, you guys don't even remember how to pronounce or write your own last name, so it's very error-prone. The other problem is that it's very time consuming. So your IT people have to literally create for you two users, or two profiles for each users. The other problem would be to ...
So the other alternative would be bulk entry. So you would have a CSV file, and then as soon as you create a few users in your identity provider, you would insert them into a CSV file and wait for a while. The problem with that is the latency effect, obviously. The error is also ... it's very error prone. The other problem is that it has the latency effect in effect that, the first user who got into the CSV file has to wait for a long time to get the user profile in the application.
Okay. So the third solution would be the Custom API. With Custom API, you can customize it anyway you want it. You could have all the possibilities of SCIM and anything that you want. The problem with that is, it's a lot a developer resources. It uses a lot of your resources. So that's something to be considered. It's heavy and expensive.
And then the last solution that people have been using is called SAML JIT. So SAML stands for "Standard ..." SAML is like an authentication system. So SAML communicates authentication between an identity provider and the service provider. And JIT stands for "Just in Time Provisioning". So SAML JIT, it has an overlap with SCIM in a sense that SAML JIT creates users in the application. It's an authentication. SAML is an authentication system and SAML JIT is an extension of SAML that has overlap with the SCIM.
But let's see why SCIM is way better and how does it do the work. So in this chart you see all the functions that SCIM supports, right? SCIM creates the user when the user is assigned with an admin. So soon as the application is assigned to an admin, the user is created. And then SAML creates the user when the user accesses that application.
So let's say, you have Alice, Alice has worked or just got an offer and signed the offer, and she is working in your company. What happens is that Alice says, "Okay, I have a signed offer, I want to go out for a month and then I will start to work." What you can do is if your application is SAML provision, you cannot do any communication with Alice's email or identity until Alice joins and signs in to access the application. But if it is a SCIM enabled app, what you can do is you can just create a user identity for Alice and talk to him and send him ... CC her to all these emails and she doesn't have to access it, so real time. As soon as she gets access or creates ... As soon as she is assigned to that application, she receives all the emails and she can come back and check it when she is ready, right?
And the update is also ... So SAML JIT updates the user when the user is accessed. A user accesses the application and SCIM updates the user when the changes occur. So you can see that real time is always better. About the read, deactivate, and password sync, SAML JIT does not do that. So SAML JIT is not full life-cycle management, but SCIM is. Since SCIM is only for provisioning it has other supports enabled to it too.
So let's look at a little bit of quantifying how these two compare. Okay. So in this chart in blue, we have a store and it's called OIN in Okta that have all the published applications that we have. So in blue is all of the SAML enabled apps, and then in red is the SCIM apps, right? What happens is that there is a question of why if SCIM is so good, why are there less of that? Why aren't there more of SCIM? The answer to that is that the SCIM very early in that standard. It is approved by Internet Engineering Task Force. So, if you want your application and it has a complete legends and protocols. If you want your application to be or your organization to be on top of technology, this is what people are going with.
What also is helpful is that it has a complete guide on protocols and you can just go and find it on internet and follow those rules.
The other problem with this is that the SCIM ... or the other point that I want to make is that SCIM isn't invested in the standard, but there is also a lot of demand for what we are trying to do. So in the near future we are expecting the SCIM to grow and be bigger or compete with SCIM in a better level.
So let's look at ... We have talked about how SCIM is better. Let's look at a little bit more about features of SCIM and how that it's going to help us. SCIM based on existing standards, so that's one of the reasons it's better. SCIM reduces costs and complexity, so that's one of the main goals SCIM was created, to reduce cost and complexity of user provisioning.
The other thing is that SCIM emphasizes on simplicity and integration that uses established pattern on protocol. So these are all theoretical stuff, right? We see is SCIM both existing on existing standards, it reduces the complexity, it emphasizes on simplicity, and it uses established standards. These are kind of all theoretical stuff.
Let's go to a little bit of quantifying what that means. So in here it says a user ... So how does it do all those things that we mentioned before, right? So one of the things that it can help with is real time user provisioning. I told you, as I mentioned before, when a user application is assigned, or a user is assigned to that application, it takes a minute or a second to create thousands of users, right, and assigns them to those applications. So it's very easy in real time.
It utilizes JSON and HTTP. So JSON is the data format that the body of the data, that uses, and http is how it is translated or transferred between standards, so. Okay. So the data format is JSON and then it talks to other people through, or it communicated through HTTP protocols. This is something that every developer, I might not even be exaggerating, that every web developer knows these protocols and data types, so. You don't have to learn anything new to implement SCIM.
And the third thing is full life-cycle management. Not only it supports all of the current operation created, deprovision, update, read, password sync, and user. It also supports some group operation. For example, creating groups and then deleting groups, updating groups and maintaining groups, SCIM also supports that.
And then the last one is automatic provisioning. So as soon as you put some data in your application, as soon as you create a SCIM server, you don't have to do anything afterward. So you put a little bit of time and investment at the beginning, and then everything else is taken care of.
So now that we have talked about this, let's talk about ... We have a group of experts called "Professional Services". They create and help you guys with the integration, and development, and integration of your Okta product. So they have given me the stats that proves how and quantifies how this works. Excuse me.
So SCIM saves 30 minutes on every application, provision, or request. SCIM saves 30 minutes on determining and configuring groups and entitlements. SCIM saves $20 per user in preparing all this for each year.
Sara Daqiq: ... dollars per user and preparing audits for each year. And, SCIM has two versions, so you can do on cloud application, and then you can use On-Prem application to use SCIM.
So, now that we have covered everything that SCIM does and how awesome it is, let's take a look at the summary. Basically, what I've talked about is that SCIM stands for System for Cross-Domain Identity Management. It has a feature that creates, update the provision and read upload users in application and identity management. It keeps identity management identity profile and the service provider in sync. It saves you a lot of money and a lot of time and who doesn't like cheap and easy to integrate stuff, right?
Now, that we are current. We have a case study. We have our partners at LendingClub that's going to talk to us about how SCIM has helped them integrate their Okta or integrated SCIM and with that I will welcome Gaurav. Please welcome with me Guarav, Senior Director of Corporation Engineering at LendingClub.
Audience: (Applause).
Guarav: You guys can hear me?
Audience: Yep. Yeah.
Sara Daqiq: Some water?
Guarav: No. I'm good.
Sara Daqiq: Right. Thanks Gaurav for joining us.
Guarav: Thanks for having me.
Sara Daqiq: Alright. So, I have a few questions from you. The first question is, can you please tell us a little bit about your experience with identity management and SCIM?
Guarav: So, my personal experience with identity management goes back a decade. I've been involved with a lot of legacy identity management product on some micro systems, and a lot of legacy products that I've used in the past, but we've been using Okta for the last 5 years or so. Identity management has multiple facets. I mean, one is the authentication authorization and the life cycle management are the key facets of it.
Sara Daqiq: Mm-hmm (affirmative).
Guarav: And, the last 5 years we have done a very good job in doing the access and access management on authorization for it, but as we started seeing more and more proliferation of cloud based applications. So, to give a fun fact we have our own 2 hundred applications on out there right now. And, when we started seeing that, okay, how do we manage identity more holistically on these platforms? We came across what is the more long-term strategic vision that we want to put in and that's when we explored and started using SCIM more and more for both cloud based application and anything internal that we can use to standardize our provisioning and life cycle management process.
Sara Daqiq: Perfect. So, before we get started a little bit deeper about SCIM, what does your company do?
Guarav: So, LendingClub has the name, such as, we are a credit marketplace. We are a tech organization based off of San Francisco and the value that we provide to the credit marketplaces is that we make credit more affordable and investing more rewarding. So, we collect borrowers and invest it on our platform to provide easy access to credit and to strivers who are looking for financial help, improvements in their personal lives.
Sara Daqiq: Alright. Awesome. So, what were you doing before this came? How was LendingClub managing identity?
Guarav: So, let me walk you through the three areas that prompted something that we need to address in this particular space. Being in the financial service industry, we have all the regulations and compliance about stocks and all that stuff we do periodically and as we had more and more applications which we're dealing with; consumer data, credit data. We're coming across a lot more valid requests and how do we prove to auditors that we are managing our systems, our accesses and privileges and permission, all the systems in a more repeatable way, a provable way? That, okay, people have access to what their supposed to and prove that. So, our operations team was spending a lot of time in making sure that, okay, the life cycle is managed properly, preparing reports for the auditors and what not. That's one area.
A couple of other key areas that we wanted to leverage any automation on life cycle management was; one was licensing and optimization. A lot of providers and the softwares that we work with, they charge based on per user licensing, right? And, if you do these provisioning manual, right? Quarterly clean up, right? So, you might be paying for licenses for three months when you don't have proof. If you look at your provision in just real time, you're maybe saving the licensing cost that you don't have to.
And, the third thing is compliance and staff efficiency, right? If we have a lot of applications, any time a worker changes their position within the organization or then they leave the organization and when somebody joins the organization, their time for being productive was like 2 days, 3 days before they get access to all the applications that they need. At the same time when somebody gets terminated, they might have access to some applications for 2 to 3 days until their access is removed so that is a compliance hole, also, that we were trying to fill in.
So, all these holistically drove us to create a solution that can help us mitigate all these needs and be more effective in how we manage identities across.
Sara Daqiq: Perfect. So, what user life cycle management, I know that you mentioned it a litte bit, but what user life cycle management problems were you guys facing?
Guarav: Yeah. So, these were the problems that we were facing, and again, as I said, when we started to look at our entire landscape we feel like it's a very big problem to solve but the way we prioritized this was, like, okay. Let's identify what are the low high end feeds? What are the key applications that falls under our audit review? And, starts with that rather than creating a big whole program for it. The way I have recommended my team to approach this is that, solving an identity is not a project. It's a journey. It's an ongoing thing. You keep going back as you would with new application, as you would new processes. It's a part of life cycle management. We have to keep on improving the way we do these things and engage with our business partners to start to make sure we get continuous feedback on how we make it better.
Sara Daqiq: Oh. Awesome. So, what were the alternatives? Was there anything that you would say, "Okay. Should I use SCIM or should I use something else?" Was there any other options and what were they?
Guarav: Sure. So, me being an engineer in an organization our first purpose was well, okay, let's build it. Let's build the code out of everything, right? So, that's what our engineering mindset goes with, but again we started with a couple of them. What we started realizing was that every application has its different semantics. The way it works. The identity means different for different applications and as we started using Okta more and more, we started realizing that we have to create an abstraction on top of this, right? And, that's when SCIM helped us and what my team has done is they've done a very good job in abstracting and more democratizing SCIM.
So, what we do is that we don't try to create central processor, like everyone has, to be SCIM within my own organization, but more educating people, educating teams across different application owners. Meanwhile, evaluating a third party application, of evaluating in applied form, how to make sure that these support these kind of protocols so that it's easier for us to hook up with a standard life cycle management.
One of the interesting things that we did is that we went with our management partners and we have include these identity related questions as part of our RFE packages, right? So, when we evaluate lenders, these are part of our evaluation of third party software; is that do you support Samwell? How do you support Samwell? What API do you support? Do you support SCIM as a standard API? That helps us evaluate those windows up front rather than realizing later that no, we need to do all this work later in the game to make our life cycle easier with those applications.
Sara Daqiq: I have two questions about that. One of them is that, can you elaborate on what you meant by democratizing the applications?
Guarav: Sure.
Sara Daqiq: The second question is that, if I apply to your company as a lender, and I do not have SCIM, is that a requirement?
Guarav: Let me answer your first question. So, the way I mean by democratization is that SCIM is a game of specification, right? SCIM doesn't enforce you to use a particular technology or a particular platform or a programming language. I mean, you can use Python, Java, I mean, Node. I mean, you can use whatever programming language that you want to create for that specific application. So, the way that we have a process is that if you're in ops organization and if you're onboarding a bunch of applications, alright? What we educate them is, okay, can you build SCIM extraction on top of that? Right? Using the technology that you are comfortable with. My team, for example, we use Okta for a lot of our stuff, for application of a lot of stuff. So, we have created our way, specifications of SCIM that we have published across the organization. Anybody can use it to implement that, SCIM extraction and pop up application.
The next step that we are trying to do, and it's not just about based application, right? It is, again, SCIM is managing clausal identities, right? You can manage access to database. You can manage access to anything that you want to do it, all that membership, right? So, we're just trying to say when we're going into the same purification journey how can we create an extraction on top of any identity management? And, building ropes with an organization can build their own, as long as they're at a brink of a specification, it will be really easy for us to hook it up to our infrastructure and manage the life cycle centrally with given based provisioning and de-provisioning.
Sara Daqiq: Awesome.
Guarav: And, to answer your second question, so as of right now SCIM, as you said, is in very early stages of an option. But, they're two intents to ask that question when we're asking about availability of SCIM on the platform or not. One is, we want to encourage more lenders to think about it. As of right now, it's not a show stopper for us, I mean, functionally for particular applications it's meeting our business needs, that prompts everything. We have to look at, but from a preference perspective we would like them to be either SCIM compliant or at least have some sort of API's that does use our management that we can extract and create SCIM on top of...
Sara Daqiq: Mm-hmm (affirmative).
Guarav: Because we don't want to get into a position where we have, I mean, if you're asking that we have at least two applications go up every week.
Sara Daqiq: Right.
Guarav: That is the frequency that we are getting different applications on and we don't want to get into a position where when our auditors come in and ask, okay can you explain that you have these 2 hundred applications, how are you managing their identities? How can you prove that you don't have unauthorized access to these systems, right? So, we don't want to look back and fix that so we are trying to get ahead of the game and injecting that as part of our initial diligence.
Sara Daqiq: Yeah. So, maybe I've talked about how SCIM is good for us and how it has helped your organization. What are the challenges that you have faced?
Guarav: The biggest challenge is that making sure people understand the value of it and that's why it's important to educate. You have to work with your business partners, your technologic partners, to understand what does it mean and it required us to create a set of road shows that we worked with them. How is it important? How is it going to help? Before starting to deepen to it.
The second thing, as I said, was prioritization, right? I mean, if you have a big application pool, what do you focus on first in making sure that you're focusing on the applications which gives you the biggest value for the buck.
Sara Daqiq: Mm-hmm (affirmative).
Guarab: And, we had to do an extensive exercise with our service desk personnel. Get some historical data. Let's identify how many application requests were you getting? How much time do we spend on each of those applications? And, have some metrics before and after that we can prove statistically, that okay, this is what is the benefit that we are getting in terms of efficiency compliance and how it affect those.
Sara Daqiq: That's a very good point. The last question I have is, so, now that you have implemented SCIM for some of your applications, what's next? What would you do to upgrade SCIM?
Guarav: As I said, it's an ongoing thing. SCIM itself has been evolving. I started exploring SCIM when it was 1 or 2, now it's .02, which is a lot more picture and has a lot more capabilities to it. And, in my opinion, right? As I said, it's an ongoing thing. I mean, we find it's an opportunistic implementation, as I would say. We identify where we can improve the way we do things and continuously work on it. Once you establish a process in the framework, working with your business partners, it becomes a lot more easier for adoption and implementation.
Sara Daqiq: Thank you, Guarav.
Guarav: Yeah.
Sara Daqiq: Now, I'd like to welcome Joe back to the stage to talk and get questions from you guys, if you guys have any.
Joe: Any questions from you folks? Looks like we have a question over here.
You can just tell me and I'll repeat it to everybody.
Questioner 1: Sure. How do you set up SCIM server and is it SCIM server per app or SCIM server can be one on top of many apps?
Joe: So, the question is how do you set up a SCIM server? And, is it one SCIM server per app or can you have a SCIM server that togs to multiple applications?
Guarav: You want to take that?
Joe: I can take that one, so it's pretty flexible. It really depends kind of on how things are set up so it's at the core of how the scanner works is it's just up to sending messages to an end point that you set up. If it makes sense conceptually for you to have a single place where that happens then you can just have one SCIM server and, you know, but you'd have to update it too. Every time whenever you're adding a new application, you'd have to update it to go downstream. So, ideally each of your applications should eventually have support for SCIM. It probably makes sense to have one per application. Just because you often map an application to a group in Okta and you want those assignment and un-assignment messages to go to that particular application.
Guarav: And, that's what we have done. I mean, we have created extraction for each app separately, so that each application lives in its own ecosystem. It's not a central single point of failure and that way, I mean, the way we're going with micro services then it becomes only part of the...
Guarav: The way we are going with micro-services, that it becomes only part of that application ecosystem, it's not impacting anything else.
Joe: Oh, and we've got another question here.
Speaker 1: Hi, how does this standard deal with error handling? If Otka is trying to send the message to the SCIM endpoint, and it can't get to it, what happens then? Is there an alert that goes out? I'm just curious how-
Guarav: So the way Otka works with SCIM is that it works on a queuing mechanism. Everything that even happens in Otka gets logged into a queue and it gets processed by the agent that pushes that to the SCIM server. And that message is not logged that's complete until that provision is happened such as this one right? And then when the provisioning fails, an administrator would see alerts within like ... if you have used out of the box provisioning for sales for any other applications, then something fails so there's a conflict of identity, right? So you see that alerts that you can reprocess those messages in that. So SCIM works in the same methodology and can do that.
Joe: And this is one of the things that Sarah was mentioning is because it's the HTTP protocol, it's all defined, right? So if you return an HTTP 200 error, then our queue is like, cool, message got accepted. If you turn a 400 or 500 error, then you'll see something show up in that log. And that's one of those things like, your developer already knows this, right? If there's an error, give an HEPR.
Speaker 2: We're in the process of adapting SCIM so for adopters like us, like we're just starting with SCIM, do you guys have any suggestions or what are the challenges that you guys have to go through which we should be taking care of?
Joe: So that this question about how hard is it to get SCIM set up or-
Speaker 2: Right. How hard it is and any blockers of things that you had in the way which we should be taking care of early?
Guarav: So, one of the things that I would suggest early that SCIM has different interpretation for different organizations and Otka has a very specific SCIM implementation, so even the SCIM is very broad. If you go with 1.2 and 2.0, it's very broad specification, but when you start implementing SCIM, make sure you understand how Otka works with SCIM and you design your endpoints and specification that is compatible with how Otka uses it. That will make it more effective.
When we started it, we created a general SCIM endpoints that can work with anything, but as we started using it in conjunction with Otka, you start to realize that there is a certain way it has to be done and I think Otka has done a great job in documenting how it has to be done, what are the data limits expected, what are the endpoints, and what is expected for it to work with Otka specifically. So, once you do your set of POCswith couple of applications, integrating with Otka, that will give you a better understanding on how to take it to large scale.
Sara Daqiq: Yeah, and before that, we have in our Otka preview, we have samples of the application that you can integrate in your backend and that shows you all the logs that you would get, and how SCIM works with different applications.
Speaker 2: And did you have to face any performance-related problems going through this app switch.
Guarav: The good thing about this, this is all asynchronous it's a queue-based model, right? So Otka is getting processed by the provisioning agent or if it is a real time and location. From an even processing perspective, I've never seen it as taking more than 15 minutes from the time the firing happened to the way the provisioning activity has happened. So it is pretty quick and almost like no real time to process.
Speaker 2: And one more question on the Otka. So does Otka itself have SCIM-compatible APIs? If you wanted to do provisioning from AV to Otka?
Joe: So, we don't have that yet. We're working on it. People keep asking about it. I actually wrote the Python sample that's out there with that in mind. So if someone really needs it, just let me know and I can add that stuff in because the nice thing about SCIM is that it often maps almost one to one two existing APIs and the Okta user's endpoint is very close to that SCIM standard. So, if you need it, let me know. You can find me. My name's on the thing here or I'm just JF on Twitter. I'm happy to help you with that.
Other question? I think we have one over here.
Speaker 3: So, a follow-up with an earlier question, in case of headers. . . is it automatically retries that SCIM provides?
Guarav: So that would be from Otka, right?
Joe: Yeah, so the specification, the standard itself doesn't have anything around doing retries. The way it works in Otka in particular is that it, like we were talking about earlier, you get an error shows up that is in a log, and I believe you can actually say retry in that interface and usually those errors will ... it might be a temporal thing, you just retry it again. Then if it goes through, then that error message disappears.
Guarav: Yeah, because I think from an Otka perspective, also, we look that it doesn't ... kind of the mediation or the broad spectrum of errors that we have, it can be a five-oh (50) to a bad gateway, or it's an internal server under 500, or it can be anything in the mirror, right? So Otka's retry won't know what to do with that until you have to implement a rule-based retry mechanism and depending on different codes or different scenarios, do the retries. So at this point, it's open to the administrators to understand what there is, look at the logs, and determine what needs to be done from that. If it's a little glitch, you can do a bold select and reprocess all the alerts. It will reprocess all the failure messages.
Speaker 3: So, in the future, do you guys contribute ... okay, say it's a bad connectivity, a connection failure. Can Otka retry those failures automatically based upon the other goals. Do you guys-
Joe: So, I believe we do some basic retries in certain situations. I forget what it is, but it's all based on the HTTP standard. So for a network connectivity error, you might just have 80% packet loss and you won't even get that error back, you'd have a time out. I forget the specific situation for that, but in practice, how often do you see errors?
Guarav: I've seen very rarely and whenever it happens, my administrator goes back and reprocesses it at this point. So I haven't seen that as a major pain that we have to deal with so far.
Joe: I think in my mind the way to think about SCIM is it's just like another HTP endpoint. So if you have an application of a standard web app, it's HTP, you can put an engine X in front of it, you can take all of the same techniques that you'd use to keep a highly available website up and apply that to your SCIM endpoint.
We've got a couple more questions here.
Speaker 4: So this is a question about the errors again. Will they end up on the dashboard again like all of the other provisioning errors?
Joe: Yes.
Guarav: Yes.
Speaker 4: And is there functionality planned to send email educations for the dashboard tasks?
Joe: I don't know of plans for that. We do have kind of generally what we've been thinking about is giving people the ability to hook into certain stuff, so you might have heard us talking about our extensibility. Again, this is sort of a forward-looking statement, but it's like a general practice. You could monitor the CIS log messages and then create emails based on that. Eventually we're hoping to build something where you could say when this type of message happens, do this type of action. Again, that's pretty far down the line.
Guarav: So what we have done for that particular thing is that we are using Otka's API to Splunk everything and we have created a lesson on top of Splunk using it as a slug. The good thing is that all the event information in Otka is very rich that you can do whatever you want to do with that. So we have used the standard Splunk dashboards and other mechanisms that we are traversing through our standards in platforms like Splunk to create any alerts.
Speaker 4: And the follow-up question to SCIM is that functionality available with base Otka or do you need separate licensing?
Joe: As a technical guy, it's something that I'm not really sure. I know that in the Otka preview, if you get a developer instance, it's there. So you can get that, try it out. I believe it's tied in with lifecycle management SKUs, but to just try it out, you can go to developer.okta.com, try it out from there.
Got time for a couple more questions.
Speaker 5: I'll keep this quick. It's great that you're doing this for those who can build and are doing this for custom applications. As somebody who's at the mercy of a customer of other people, what is Otka doing to promote SCIM and push this forward and across that little red chunk becomes a really big chunk?
Joe: Well, for one, we have this conference and then we're giving a talk in the conference. We actually have a bunch of classes in enablement for that but I'd say at the base level, if you have an application that you want to be enabled for provisioning, contact support, let 'em know. It matters. In the back end, we have support tickets that are talking about a lot of people have been asking for this particular feature. And once that number gets big enough, we'll start pressuring people, or bringing up when you're having a renewal conversation with the vendor. Those types of normal things, but in terms of enablement, we have a slide at the end. We're doing training classes on if the vendor wants to know how to set it up, we have a really amazing training class on how to get that set up. We have a ton of documentation, we've got samples that are written in Python and in Java, we have a test suite that people can use to just run a full series of tests against their endpoint to see if it's working.
Doing all the stuff that we can think of, definitely, let me know if there's other ideas that you have, but that's the kind of baseline.
Sara Daqiq: Yeah, I want to add to that, that Joel is a very big evangelist of promoting SCIM in the organization and outside the organization. So we have application in RANScope. We have tests in RANScope that as soon as you enable your SCIM or make your SCIM, you have to run against those applications to see if all those are working.
Joe: Yeah, which means as a vendor, you can say, hey do this. Pass all these tests. And it was actually written so that someone who was learning would be able to ... you pass the first test is the easiest, and then it gets harder and harder. That was one of those design intentions.
Sara Daqiq: And I also want to mention that we have a whole team dedicated. So once you talk about it, they will help you if you have any questions.
Joe: We have time for one more. And afterwards, we're going to be outside. We want to get ready for our next talk, but we'll be outside after this is done. So, last question.
Speaker 6: Thank you. Are you using the supported SCIM server that is offered by Otka or can you use another SCIM server out of all the possibilities? For example, we have Best Talk has an integration solution. It can be used Best Talk to be the SCIM server.
Guarav: Yup. You can. So you can use any server that can do HTTP to API, so it's up to ... the way that we are using it, that we have SCIM servers written on NOJS, NEO Java, everywhere. So anywhere that you can bite in API on top of, that can be a SCIM endpoint that you can hook up.
Joe: Yeah, I mean we're following the standard, so as long as ... like any standard, there's certain areas that have gray areas. One I ran into recently was token sizes. One of the vendors we were working with had tokens that were 64k in size. So we had to take that into account. But generally, we're following the spec, so as long as it's a standard compliant server, we expect that we're going to work with it.
Thank you everybody for coming. Again, we're going to be right outside.
Watch how LendingClub and Okta partner up to handle multiple users in multiple applications on a 24/7 basis. By utilizing a System for Cross-domain Identity Management (SCIM), Okta shows how this open standard manages identity at large.