Demo: Multi-factor Authentication
Transcript
Details
Speaker 1: With Okta, you can choose several different factors for authentication. To do that, you just go to this multi-factor factor type interface, and you can see that there are a lot that are pre-integrated. You have our native ones, like Okta Verify, you have our partners', like Duo Security and Yubikey. You even have standard ones like U2F. You enable these here. We also support On-Prem MFA like RSA SecurID through an agent.
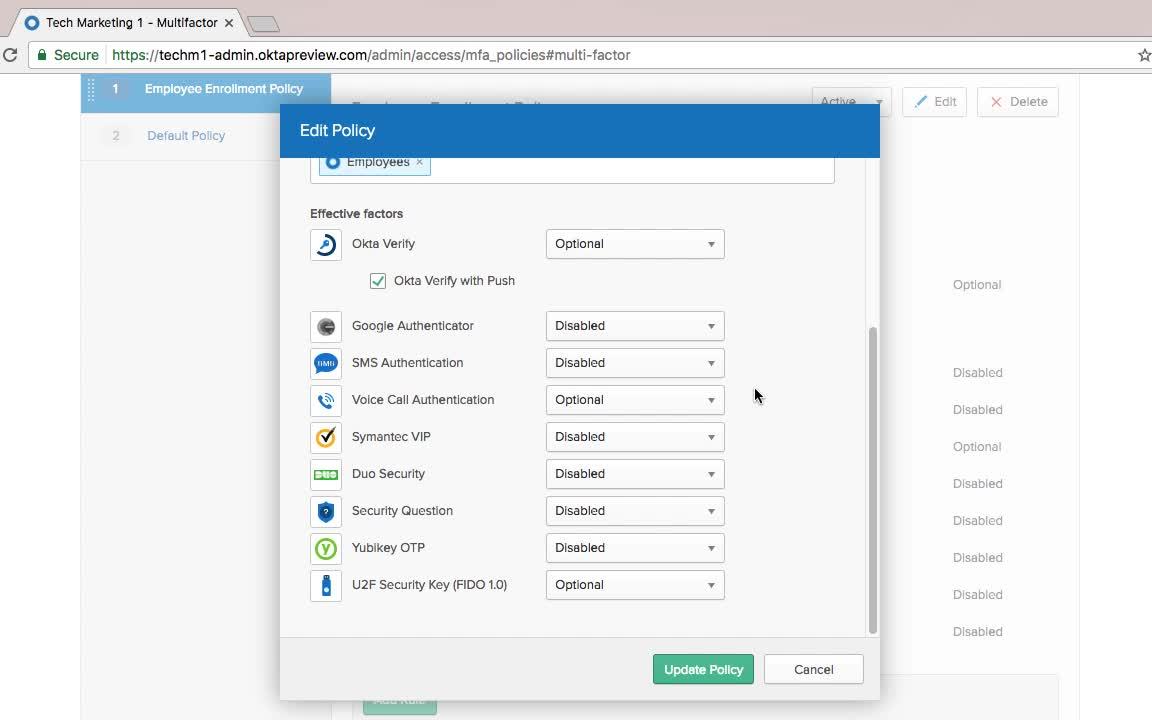
Speaker 1: I've selected a few here, and then to set them up, we actually use something called an enrollment policy. The key here is that this gives you granular control over the enrollment experience for an end user. You can see I have an employee enrollment policy here. It's assigned to my employees group. I can have other policies for other groups. And then when I click Edit here, I can alter the factors that they're eligible to enroll. So, in this example, I'm going to go ahead and enable U2F Security Key because it's a great user experience, and it's also pretty cheap, and users kind of like them. Also, SMS. I want to make this optional as well, because this is just a ubiquitous factor that's very common for use in Okta.
Speaker 1: Another thing that I'll add here is that we have rules for enrollment, as well. If I go ahead and edit this rule, you can see that I have very granular control over the enrollment experience. I can say the user has to enroll the first time they're challenged for MFA. So, first time they click on an application that requires it. Or, the first time the user signs into Okta, I can actually force them to enroll upon first login. I can also turn off enrollment for situations like, if they're logging in from a zone that is not recognized, or they're logging in from on-prem. That way, I can enforce only users can enroll for MFA when they're on-prem. I'm going to leave that as is for now.
Speaker 1: Now, everything's set up. If I go to the applications and the HR application Workday and then click on sign-on, that's where I set up the actual policy. If I add a rule here ... You name the role MFA. In this case, we're going to turn it on every time the user accesses the app, and for all users. All users that are assigned to this app, regardless of where the user's located. I'm going to prompt for a factor every sign on. Click Save, and now I'm going to be prompted for MFA.
Find out how easy it is to setup multi-factor authentication in Okta’s admin portal. Learn about our out-of-the-box user authentication methods, and how to choose one.