Internet protocol spoofing (or IP spoofing) involves impersonation. A hacker alters address data within the IP header, fooling a system into believing the data comes from a trusted source.
People use IP spoofing to launch devastating attacks, including denial of service (DOS) and man in the middle. But the technique also has legitimate uses, especially if you're planning to launch a new website.
It's difficult to stop an IP spoofing attack in progress. But with filtering techniques and solutions applied on the edge of your network, you can stop a hacker from gaining access.
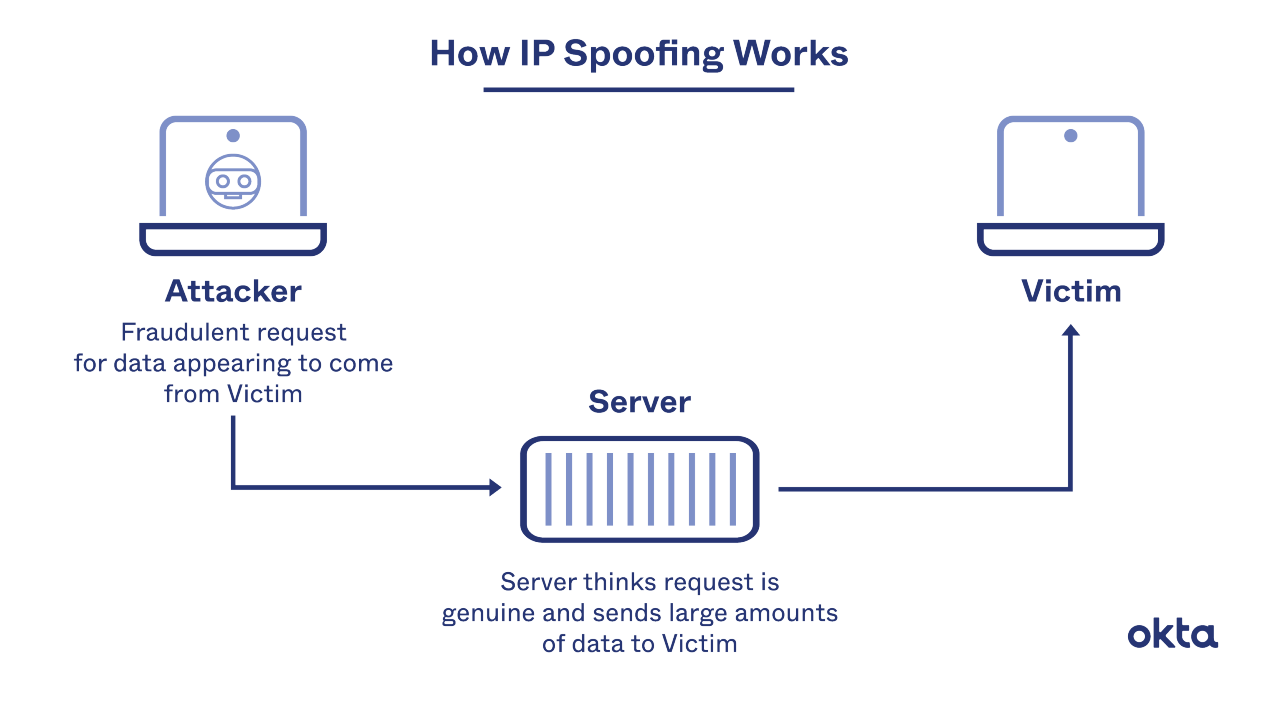
How IP Spoofing Works
Hackers exploit known vulnerabilities to launch an attack. Then, they use bots or zombie computers to amplify their work. The results can be catastrophic.
Each time you send something between servers, the data is bundled into packets. Each one comes with a header, and that typically includes routing information, such as the sender's address. Once all the packets reach their destination, they're reassembled and combined into a cohesive whole.
In a typical network, outgoing traffic isn't subject to a filter or a cross-checking system. Inconsistencies flit by, and the system isn't designed to look for them.
To accomplish IP spoofing, a hacker typically needs:
- A trusted connection. Spoofs work best between two devices that have some kind of prior relationship. If a hacker can access an internal machine that doesn't require a login, the attack is much easier to launch.
- A controlled IP. The hacker must have an address that can be ignored.
- Coding know-how. The hacker must know how to intercept a packet and swap out the address in the IP header.
With this work completed, you will be unable to:
- Stop the attack. Block the IP address that seems to be the source, and you'll block work from a benign computer. You'll have no idea where the problem originates.
- Respond to the attack. You won't know to whom you should speak or what to do next, as you won't have the proper address.
IP spoofing is relatively common. It takes just a bit of know-how to launch an attack, and once inside, the rewards are significant.
What Is IP Spoofing Used For?
Anyone with a desire to cause destruction and disorder could attempt to spoof an IP address. But it's typically used for one of two reasons.
Hackers use IP spoofing to conduct serious and overwhelming attacks, such as:
- Denial of service. Once the hacker forms a connection between a falsified address and your server, it's time to launch a series of requests. Hackers may send just a few at first, but amplifying the attack through open reflectors, such as servers running applications with connectionless protocols, can be devastating.
Experts say an attack like this can reach several hundred Gbps. Your system won't have the capacity to do anything else.
- Man in the middle. Once hackers establish a trusted connection, they can reroute all packets to a destination they choose. All data could be read or manipulated before it's released.
IP spoofing, as a whole, isn't illegal. You may have legitimate reasons for deploying the technique within your own server.
For example, if you're preparing to launch a new website, you must understand how it will perform when hit by hundreds or even thousands of website visitors from all around the globe. IP spoofing could allow you to run simulations to enhance your performance and ensure that your site stays up.
You might also run IP spoofing simulations to check for gaps within your programmed security systems. If you can't run a test, you may never know if you have adequate protections in place.
How to Protect Against an IP Spoofer
Cyberattacks cost businesses an average of $200,000 per incident. Since IP spoofing is one of the easiest attacks to launch, and one of the most devastating, it makes sense to put protection at the top of your to-do list.
These are commonsense solutions:
- Use filters. Set up systems to examine the source headers of incoming IP packets. If something looks unusual or awry, reject those packets outright until the issues are fixed. Use a similar system to check the headers of packets leaving your servers too.
- Enhance verification. Don't allow connections to stay open without some type of check or quality control. Your users may have more work to do to maintain a connection, but you'll ensure that an attack falls flat.
- Use DNSSec. Digital signing helps assure users that the data originated from the stated source and that it was not modified in transit.
- Use IP level encryption. Keep hackers from understanding your data as it moves from one place to another. Keep standards as strong as you can.
Ongoing monitoring is critical too. It can be hard to spot an IP spoofing attack, but if you notice unusual activity, including a spike in server requests, you could have a problem in play that deserves your full attention and a quick remedy.
A History of IP Spoofing
The internet was built with IP packets in mind. Spoofing is almost as old as the internet itself, although people weren't aware of the problem until many years later.
In the 1980s, researchers became aware that hackers could alter the data within the IP header system, and they wrote articles about how this worked and how it could cause problems. Researchers discussed this among themselves, but no widespread panic seemed to come from these conversations.
Everything changed in 1994. A well-known security expert named Tsutomu Shimomura endured a devastating IP spoofing attack on Christmas Day. The incident was widely reported (and it's sometimes called the "Computer Crime of the Year"). All that publicity made many people aware of the damage an attack like this could cause, and plenty of experts began wondering what they could do to keep their systems safe.
Much of what we know about IP spoofing prevention stems from conversations held after 1994. While we still have much to learn, we know much more know about how to protect our servers than we did in the early days of the internet.
Help From Okta
Plenty of bad actors want access to your servers and your critical data. Creating a strong firewall can help, but anyone with a bit of coding expertise can trick your servers into trusting them. We can help.
Learn how Okta's systems can help you block IP spoofing attacks, so you can avoid catastrophic hacks that take down your servers.
References
Detecting IP Spoofing by Modeling History of IP Address Entry Points. (June 2013). Conference: AIMS 2013.
Addressing the Challenge of IP Spoofing. (September 2015). Internet Society.
IP Spoofing In and Out of the Public Cloud: From Policy to Practice. (August 2019). Computers.
Cyberattacks Now Cost Companies $200,000 on Average, Putting Many Out of Business. (October 2019). CNBC.
IP Spoofing. RaviKannan911.
Shimomura vs. Mitnick: The Computer Crime of the Year. CrimeResearch.org.


