Products
Our platforms secure all types of identity from AI agents to your customers, employees, and partners.
Our platforms secure all types of identity from AI agents to your customers, employees, and partners.
Okta is the neutral, powerful, and extensible platform that puts identity at the heart of your stack.
Okta and Auth0 deliver flexible, secure access. Build fast with our extensible platforms for customers, workforce, and non-human identities.
Our platforms secure all types of identity from AI agents to your customers, employees, and partners.
Our platforms secure all types of identity from AI agents to your customers, employees, and partners.
Okta is the neutral, powerful, and extensible platform that puts identity at the heart of your stack.
Okta and Auth0 deliver flexible, secure access. Build fast with our extensible platforms for customers, workforce, and non-human identities.
Our platforms secure all types of identity from AI agents to your customers, employees, and partners.
Shift from chasing fires to proactively preventing breaches. Secure every identity—both human and non-human—across your ecosystem.
Continuously scan for risks across all human and non-human identities (NHIs). Then, prioritize vulnerabilities by impact and streamline remediation.
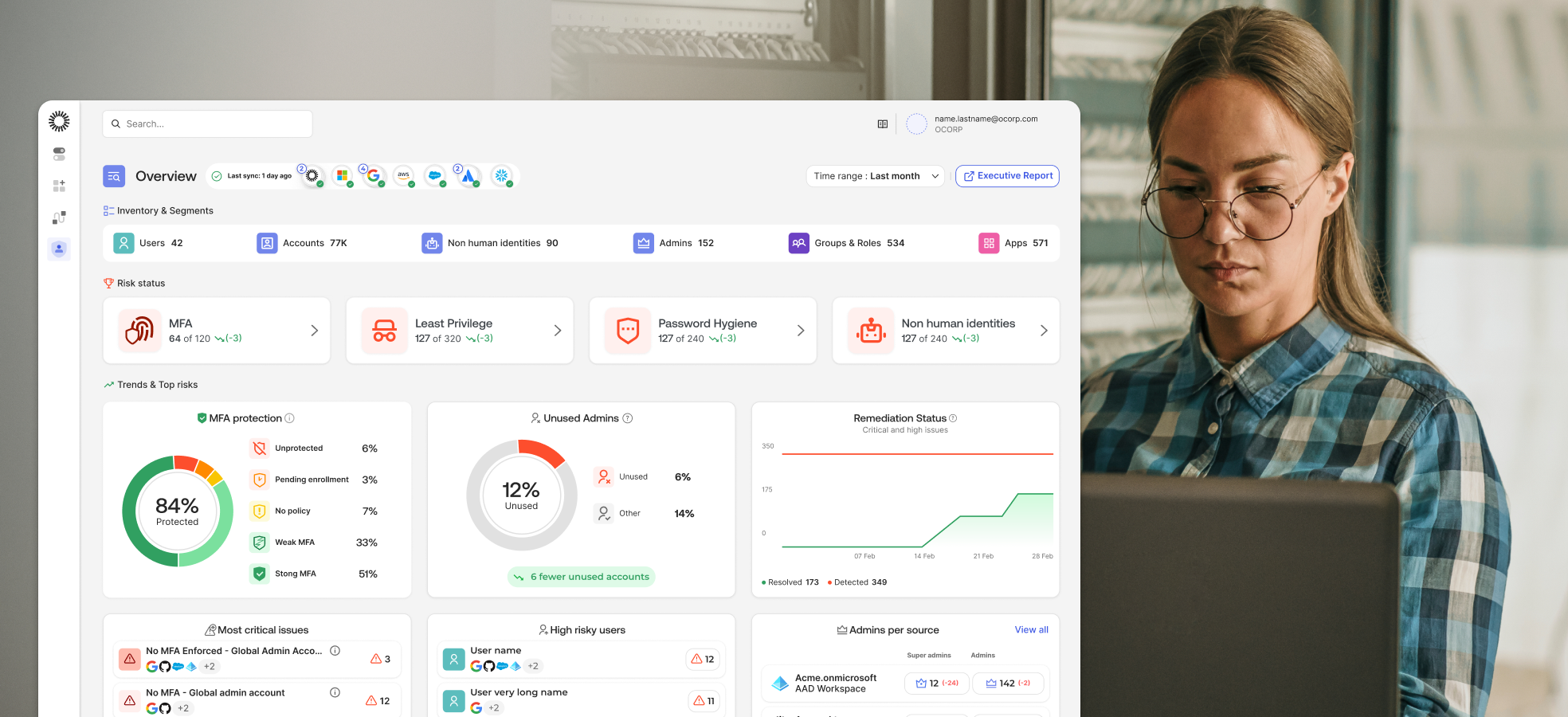
Go beyond simple lists. From human users to AI agents, visualize the complex relationships between all your identities and their corresponding permissions.
Quickly spot and resolve your most urgent identity security issues, mapped to known best practices and prioritized based on attack chains and consolidated context.
Deploy in minutes and get stronger security up and running right away. Once deployed, you’ll have ongoing and continuous analysis of your identity security exposure.
Go beyond simple lists. From human users to AI agents, visualize the complex relationships between all your identities and their corresponding permissions.
Quickly spot and resolve your most urgent identity security issues, mapped to known best practices and prioritized based on attack chains and consolidated context.
Deploy in minutes and get stronger security up and running right away. Once deployed, you’ll have ongoing and continuous analysis of your identity security exposure.
Identify shadow admin accounts and permissions, and enforce least privilege.
Continuously scan and analyze your organization's identity graph to detect access points without MFA, and identify local accounts.
Easily identify offboarded users who still have active access, and reduce the time needed to complete offboarding while supporting compliance.
Identify shadow admin accounts and permissions, and enforce least privilege.
Continuously scan and analyze your organization's identity graph to detect access points without MFA, and identify local accounts.
Easily identify offboarded users who still have active access, and reduce the time needed to complete offboarding while supporting compliance.
Unify NHI security and control for every identity across your tech stack with one policy engine—without slowing innovation.
Easily navigate complex configurations like nested groups and misaligned identities, and confusing conditional access policies.
Understand and validate MFA bypass and least-privilege access to virtual machines, databases, and S3 buckets by identities and API keys.
Monitor non-MFA access, local accounts, offboarded employees, and contractors with access.
“Identity has become the key to modern security. Controlling the identity sprawl while enabling business is a challenge that legacy solutions could not resolve. Identity Security Posture Management uniquely provides us with ongoing visibility and reduces Identity risks with a quick time-to-value and a data-driven approach.”
Matt Sharp
CISO
Read their story“Identity Security Posture Management enables us to see the actual data and immediately reduce identity security risks across business units without having to drill through miles of spreadsheets. It showed quick ROI by eliminating accounts not being used. This improved both security and license expenses. Identity Security Posture Management filled a gap that no one else could.”
Drew Robertson
CISO
“Identity Security Posture Management provides us with assurances of our controls’ effectiveness, subsequently reducing the attack surface of our applications. It makes the identity risk remediation process collaborative and seamless, ensuring teams are meeting expectations and policies.”
Douglas Graham
CISO
Start a free trial or talk with us — the next step is all yours.













