MFA 101: Leaving Passwords Behind
Cloud technology is growing at unprecedented levels — and as a result businesses are changing the way they work, seeing an increasing number of employees use mobile devices to access both personal and work related information.
While these changes enable workers to be more productive, they also bring security concerns for IT departments tasked with the challenge of maintaining visibility over who has access to what while protecting both on-premise and cloud applications. In fact, in a recent report our partner Accenture found that 51 percent of senior decision makers are concerned about security issues when adopting new technologies.
The challenge is users themselves pose a security threat for organisations, as they tend to either use the same insecure password across all personal and professional channels, or leave passwords written on pieces of paper for all to see. These bad habits leave us vulnerable to password theft and data security breaches. In order to protect itself, IT needs to efficiently manage the roles and access of individual network users within the company. The key is to supplement the traditional but insecure username and password setup with strong and easy-to-use second factors.
The Pitfalls of Passwords
Traditional web applications are protected with single-factor authentication: a username and password. In addition to being difficult to remember, these credentials leave sensitive data and applications vulnerable to attack.
Even though cloud software vendors like Salesforce.com and Workday each go to considerable measures to ensure they’re running highly available and secure service, their login screens are equally as available to attackers as legitimate users. What’s more, today’s cloud applications do not easily integrate with existing enterprise products used to monitor dangerous security events, which can make breaches of enterprise cloud apps difficult if not impossible for to detect.
Supplementing Passwords with MFA
As enterprises adopt more cloud applications, addressing this threat has become increasingly critical — and business decision makers are taking notice. A growing number of organisations aren’t just talking about MFA, but actually using it: tokens are on the rise while the classic security question is on the decline as a form of authentication, according to our recent data.
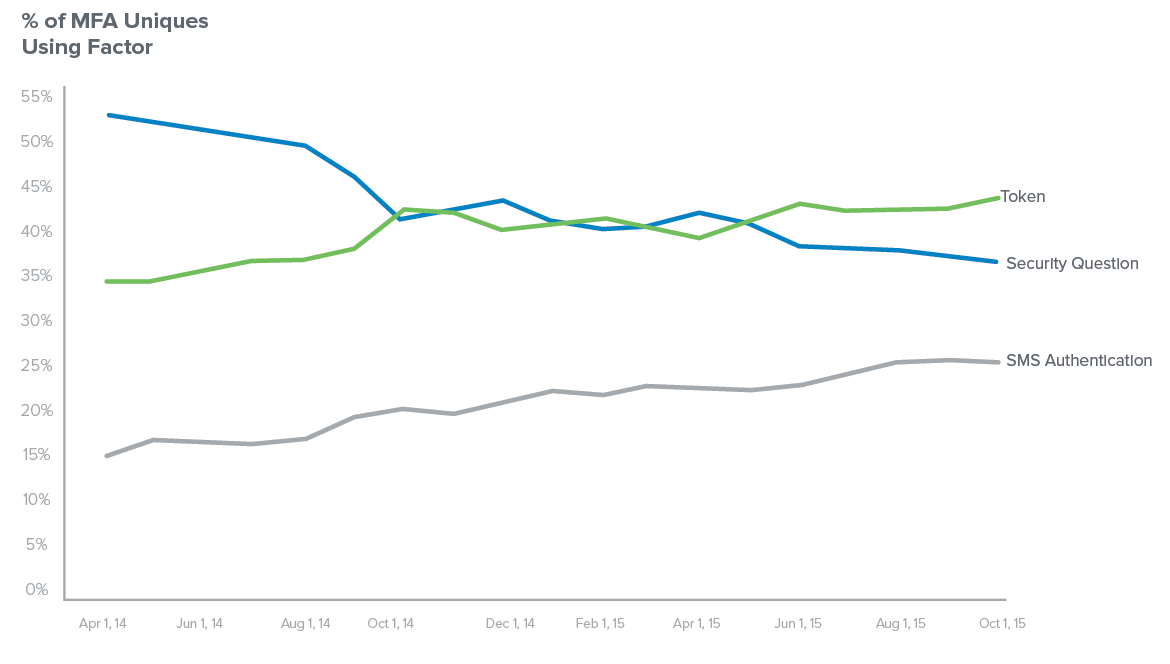
Depending on user needs and the sensitivity of the applications, businesses can choose from a variety of second factor options, including SMS and “soft tokens" like Okta Verify with Push and Google Authenticator. For example, Box secures employee applications by requiring a username and password, as well as a phone application that generates a unique number they have to enter in order to gain access.
Enterprises including DocuSign and Rotary are using MFA to ensure people who want to access sensitive information are who they say they are. MFA enables the right employees to access the right data from any device, anywhere in the world.
In the case of Gatwick Airport, CIO Michael Ibbitson points out that adaptive forms of MFA allow the airport to better understand and identify applications that need to be protected with second factor authentication. Administrators can also designate different access management measures across applications without changing the login experience for users.
With companies of all sizes going digital, businesses are looking for new ways to quickly and securely adapt. In order to realise the real benefits of the cloud, they will have to alleviate concerns around application security, access and control by moving beyond passwords and using MFA. In turn, employees will have access to the apps they need, when and where they want them.

