The Impact of Quantum Computing on Cybersecurity
Quantum computing is a fast-emerging area of computer science that is upending the foundations of cybersecurity. It’s set to change how we secure our everyday communications, process credit cards, store data, and securely connect to websites. But it’s also likely to disrupt modern security as we know it.
What is quantum computing?
Conventional computing is based on a simple binary number concept developed for the first computers designed after World War II. Every computer instruction is translated into a sequence of 0s or 1s.
In quantum computing, meanwhile, instructions can be in a state of 0 and 1 at the same time. This allows them to work on millions of computations in parallel, exponentially speeding up the time it takes to process a task. This new approach to computing is predicted to radically change areas such as drug discovery, stock market prediction, gene sequencing, and, of course, cryptography—a key component of cybersecurity.
Cryptographic algorithms today
Cybersecurity doesn’t just use cryptography—it’s built on it. Cryptographic algorithms like AES-256, RSA, and SHA-256 are most popularly used to build security layers. Their design relies heavily on mathematics, particularly prime factorization (breaking down a large number only as a product of smaller prime numbers) to create public-private key pairs. For conventional computers, this is so computationally expensive as to be essentially impossible.
The impact of quantum computing on cryptography
Because quantum computing speeds up prime number factorization, computers enabled with that technology can easily break cryptographic keys by quickly calculating or exhaustively searching secret keys. A task considered computationally infeasible by a conventional computer becomes painfully easy, compromising existing cryptographic algorithms used across the board.
In the future, even robust cryptographic algorithms will be substantially weakened by quantum computing, while others will no longer be secure at all:
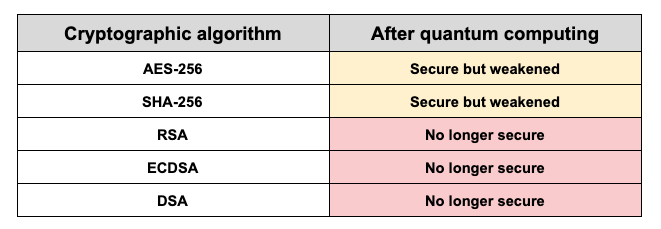
As quantum computing is further developed and emerges beyond the scope of research labs and academic journals, the real-world implications of weakened cryptographic algorithms could be critical. It is predicted that within the next decade, these machines will be available to government agencies and large companies around the world, giving them unprecedented access and power. Quantum computing represents a big leap for mankind, but a grave concern for the algorithms we rely on for cybersecurity.
Defending against quantum computing attacks
These changes represent a seismic shift for cryptography, prompting a complete rethink on how we approach cybersecurity. Like any good challenge, cryptographers are already investigating possible approaches to counter the threat of quantum computing.
Advanced cryptography
The most straightforward post-quantum cryptography approach is based on creating algorithms that are hard even for quantum computers to break. The benefit of his approach is that would also work with conventional computers.
Lattice-based algorithms
Another option is to replace cryptographic algorithms entirely and move instead towards lattice-based algorithms. The algorithms—usually only discussed in research circles—are built with security in mind and without relying on an assumption of where computational power might end up.
Organizations like Google have started testing post-quantum cryptography methods that leverage lattice-based algorithms, and the NSA, NIST, and other governmental agencies are also actively invested in their development. NIST has been developing systems to evaluate these new algorithms, and expects to publish its findings within 2022 to 2024.
White hat quantum hacking
Another nascent research arena is white hat quantum hacking. Private researchers and academics are spending a considerable amount of time to test and find weaknesses in these emerging algorithms before broader consumption begins.
Quantum computing is coming—but not just yet
While it may sound as if an impending cybersecurity apocalypse is around the corner, it’s important to note that quantum computers have a long way to go. Early models such as the D-Wave 2000Q look a lot like the early conventional computers. They’re large, expensive, and must be maintained in pin-drop silence in supercooled rooms. The good news is that post-quantum cryptography is expected to evolve concurrently to the threat it’s aimed to battle, preparing us well before widespread deployment.
Cybersecurity vendors and cloud identity providers play a vital role in the consumer and employee journey. Ensuring the integrity of authentication and communications is mission-critical. Continuous testing for current encryption schemes, securing key exchanges, and the gradual adoption of emerging cryptographic algorithms are key strategies that must be part of any playbook. Organizations also need to invest in resources that protect stored encrypted communications and secure user data. These areas cannot remain vulnerable to tomorrow’s computing power.
With a mission to connect everything, the sanctity of authentication and Multi-Factor Authentication flows are critical to Okta. We’ll continue to ensure today’s authentications are tested and secure, while also keeping an eye out for what the future holds.
To learn more about how you can securely authenticate your users and protect your organization from an attack, explore our solutions.

