An advanced persistent threat (APT) is a form of attack carried out by experts over a long stretch of time.
Unlike other forms of hacking you're accustomed to facing as a small business owner, an advanced persistent threat often comes from experts. Typically, these initiatives are launched by nations or nation-states. The hackers themselves know they'll never be arrested for their work. And they have all of the resources of a kingdom to help them.
The basic concepts of advanced persistent threats aren't new. Analysts from the United States Air Force coined the term back in 2006. They were talking about attacks against one government launched by another.
But APT security has moved to the top of the to-do list for many private companies. A major attack discovered in December of 2020 targeted “government, consulting, technology, telecom and extractive entities in North America, Europe, Asia, and the Middle East.” As a result, many security analysts realized they needed to keep their companies safe.
Could You Face Advanced Persistent Threats?
A common APT target is a government agency. Large corporations are considered valuable assets too. Launching an attack takes time and resources, and most entities are concerned with making the most of their hard work and investment.
But some APT attackers use a supply-chain approach. They attempt to overturn smaller companies that hold contracts with their main target. Each one they take over brings them closer to the final goal.
You might be at risk if you work for:
- Defense contractors. The data you hold is valuable, but your connection to larger agencies is even more so.
- Financial services companies. Banks, including investment banks, have valuable assets. But you could also have sensitive information that could be used in forming a bigger attack.
- Legal agencies. The information you have on your clients and competitors could be incredibly useful to APT actors.
- Utilities. Pulling down a major network, such as a telecom connection or a power grid, could be very useful in a major attack.
In essence, almost any company out there could face an attack like this at some point.
What Does an Advanced Persistent Attack Look Like?
The words "advanced" and "persistent" are critical to remember as you think about APTs. These are attacks that use the newest technology, and the goal is to remain within your system as long as possible to extract valuable assets.
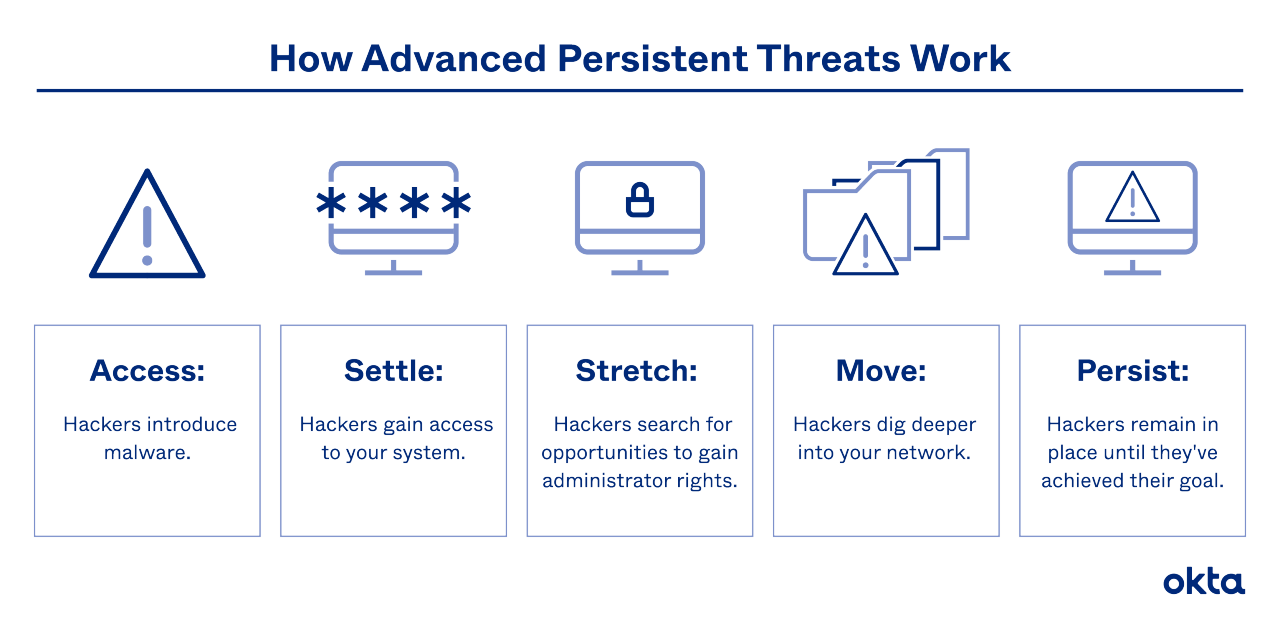
A typical attack moves in five stages.
- Access: Phishing email, fraudulent apps, social engineering, and infected files give hackers an opportunity to introduce malware.
- Settle: With the malware up and running, hackers have easy access to your systems. The goal is to remain undetected, so hackers may use coding skills to cover their tracks.
- Stretch: Hackers search for opportunities to gain administrator rights.
- Move: Hackers tap into other servers, and they dig into deeper corners of your network.
- Persist: Hackers remain in place until they've achieved some sort of goal. Even then, they may create opportunities to return if needed.
Every attack looks a little different. Some hackers perform a reconnaissance step, for example, so they can collect data on your infrastructure and relationships.
But know that this is a long, drawn-out, and technical process.
Craft an APT Security Plan
Put the "persistent" in APT to work for you as you protect your company and your assets. You have time to both find and stop an attack.
Most companies have an arsenal of conventional security defenses, including:
- Signature-based antivirus tools.
- Intrusion detection programs.
- Virus scanners.
- Network-based inspection tools (for example NGFW).
Unfortunately, these conventional tools don't work against a standard APT. These attacks are sophisticated, and they're often launched by the best in the business. You'll need to think outside the box to truly protect your company.
Start by understanding the symptoms of an attack. You may notice:
- Late-night logins. Attacks are often launched by people living in far-flung time zones.
- Strange data movement. Large data streams move from a secure computer to an external monitor. You may also see aggregates of data waiting for export.
- Phishing targets. Most phishing campaigns are random. They're sent to anyone with the proper email suffix. But if you see a strategy to the notes, including emails sent to only senior officials, you could need help.
Some companies use deep learning to help them spot an attack in progress. Computers learn how the network should operate under normal conditions, and they learn to spot anomalies long before humans can pick up on them. Programs like this come with a success rate of more than 85 percent. But they can take you quite some time to build.
Hiring outside help may also be wise. The number of companies offering these services rises every year, and many have sophisticated programs you can use to monitor your system and react when needed.
But know that an attack you think you've blocked may remain in progress. Many of these hackers leave plenty of backdoors and traps, so they can come back as they please. You may close one of these entry points, but hundreds or thousands may remain.
If you've been attacked at least once, you're likely to face the problem again. The main question is when.
Employee education is critical. Many of these attacks begin with an official-seeming email message or innocent-looking attachment. Develop an always-under-attack mentality, and encourage every member of your organization to reach out to you first, long before they act on something that could ruin your company.
Where Do APTs Originate?
Any hacker with a bit of time and creativity could launch an APT. But typically, the majority of these issues originate overseas.
The majority of attacks originate in China, but other countries with active teams include the following:
- Iran
- North Korea
- Russia
- Uzbekistan
- Vietnam
A few APTs also seem to originate within the United States too. As the techniques grow in popularity, it's likely that more countries will play host to attacks.
Work With Okta
The threats from APTs are truly advanced and persistent. But with the help of an expert team, you can move past your fear and into the future.
Let us look over your security landscape and understand your current environment. Then, we'll build a wall of security just for you. Contact us to get started.
References
Assessing Outbound Traffic to Uncover Advanced Persistent Threat. (May 2011). SANS Technology Institute.
Advanced Persistent Threats (APTs). May 2020. Medium.
The Advanced Persistent Threat. (June 2013). Internet Security Alliance.
5 Signs You've Been Hit With an APT. (February 2019). CSO.
Early Detection of the Advanced Persistent Threat Attack Using Performance Analysis of Deep Learning. (September 2020). Cornell University.
Worldwide Advanced Persistent Threat Protection Industry to 2026: Key Drivers and Restraints. (January 2021). PR Newswire.
