Credential stuffing is a popular type of cyberattack. It is the automated injection of breached username and password combinations in order to fraudulently gain access to user accounts.
Hackers want into your servers. You want to keep them out. You use a sophisticated password process, including a requirement for frequent credential changes. It seems like a foolproof system, but it comes with one major flaw.
If people reuse passwords (and many of us do), you could be open to a devastating attack.
More than 15 billion stolen credentials are available on black markets today. Often, hackers don't even need to pay for the weapons they can use against you. With this database, they could have the names/passwords of one of your employees. With a bit of hacking, they could spot your vulnerability and take over.
Credential stuffing attacks are devastating. But they can be prevented.
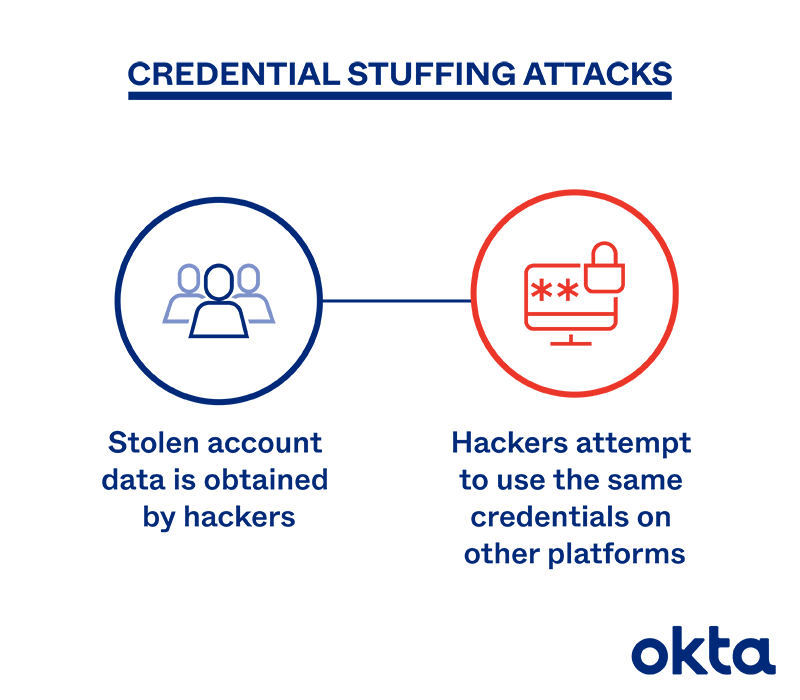
How a Credential Stuffing Attack Works
Credential stuffing involves stolen usernames or passwords. A hacker plugs the data into a bot and launches an attack to determine if the same combination opens up any other servers.
Every attack is different, but most follow this step-by-step plan:
- Discovery: A hacker finds a cache of username/password combinations exposed via some other attack.
- Modeling: The hacker runs a few tests to see if these combinations work on other websites.
- Large-scale work: The hacker uses tools to launch an attack against a server. All the stolen pieces come in as a flood of login attempts. If even one works, the hacker has access.
- Theft: The hacker looks for anything of value within the account, such as credit card numbers, Social Security numbers, and other login data.
- Ransom: The hacker points out the theft to the company and asks for a financial reason to give access back.
Credential stuffing is a form of brute-force attack. Hackers may only have one or two name/password combinations that work. But all of them are pointed at the server.
Can You Prevent Credential Stuffing?
No company wants data exposed. But preventing credential stuffing attacks means asking for help both from programmers and members. You must work in partnership to ensure that hackers don’t get a toehold into the company’s server.
Employees, users, and others with server passwords must:
- Craft unique passwords. Reusing information, even once, means exposing your servers to risk. It’s difficult to remember dozens of unique credentials, but a password manager can help you both create and store the data to make use easier.
- Change passwords often. Cycle through passwords frequently, and change them in meaningful ways. Don’t shift one letter or number, for example. Amend the entirety of the login.
- Turn on two-factor authentication. Get a notification on your phone or another connected device when you attempt to log in. This one small step can keep hackers away, and you might discover that plenty of people are trying to use your details.
At the enterprise level, companies can:
- Educate. Tell your users why good password practices are so important and develop guidelines that explain what they can do to help protect data.
- Watch attempts. Keep a close eye on login attempts. A spike could indicate that your company is under attack.
- Create custom solutions. You could use Captcha or another login hurdle to defeat bots. But some experts suggest that the best prevention tools are made from scratch.
A hacker may develop tools to get around common firewalls. If yours is new and unique, a hacker may simply choose to move on instead of spending time to defeat it.
These steps may not eliminate your risk of a data breach. But you could make your server a less attractive target to a hacker. That could save your company a great deal of heartache.
How Serious Is an Attack?
The Securities and Exchange Commission says credential stuffing attacks are on the rise. Large lists, including the Pemiblanc list that contains more than 111 million records, are to blame. With so much username/password data available, hackers can't seem to resist.
One of the biggest credential stuffing examples comes from May of 2014. Hackers got access to the credentials of three eBay employees, and they used that to gain access to the network and the database. Hackers held onto that access for a whopping 229 days.
In 2014, JPMorgan Chase endured a similar attack, but officials had no idea it was happening. A contractor discovered the breach, along with a cache of a billion stolen usernames and passwords.
It can take years to recover from a breach like this, and some of your customers may never fully forgive your violation of trust. When it comes to hacking, prevention is the best policy.
Get Help From Okta
Learn how Okta can protect your organization’s credentials and prevent attacks like credential stuffing. We'd love to walk through your processes and help you come up with a security system that works.
References
Digital Shadows Researchers Say Over 15 Billion Stolen Passwords Are Circulating on the Dark Web. (July 2020). CPO Magazine.
Taking the 'Stuff' Out of Credential Stuffing. (July 2020). Martech Today.
10 Tips to Stop Credential Stuffing Attacks. (February 2019). Medium.
Cybersecurity: Safeguarding Client Accounts Against Credential Compromise. (September 2020). U.S. Securities and Exchange Commission.
Credential Stuffing List Containing 111 Million Records Found Online. (July 2018). Tripwire.
Top 10 Data Breaches of 2020. (December 2020). Security Magazine.
How Worried Should I Be About My Password Being Compromised, Stolen in a Data Breach? Experts Say This. (December 2020). Forbes.
The Global Data Breach Notification Software Market Is Expected to Grow by $ 725.41 Mn During 2020-2024 Progressing at a CAGR of 17% During the Forecast Period. (December 2020). Yahoo! Finance.
The 15 Biggest Data Breaches of the 21st Century. (April 2020). CSO.
Luck Played Role in Discovery of Data Breach at JPMorgan Affecting Millions. (October 2014). The New York Times.


