ICMP (internet control message protocol) is a communication system with many functions.
Your system is prepared to send data to another system. Will the messages go through properly? Or is something blocking clear and crisp communication?
Devices use the Internet Control Message Protocol (or ICMP) to share status information just like this. The protocol could be critical if your network encounters a communication problem, and you need to diagnose it quickly.
Every day, the average employee wastes 22 minutes on IT issues. If you're running the network, keeping things running smoothly is critical. ICMP can help you do just that.
But ICMP does have a dark side. Sometimes, hackers use it to flood your server with so many requests that you lose connectivity altogether.
What Is the ICMP Protocol?
In 1981, the Network Working Group developed the Internet Control Message Protocol to help interconnected devices communicate quickly and easily.
As the developers pointed out, ICMP isn't made to make a network more reliable. Instead, it's designed to help teams troubleshoot and fix problems quickly so they can stay online.
ICMP is used by network devices, including computers and routers. You might use the system for:
- Diagnostics. Find out if a server is open and accepting messages. If it's not, find out why.
- Error reporting. Determine why some or all of your data isn't reaching the intended recipient.
- Speed. Find out how long it takes for a packet to move from one place to another.
Three functions are critical in the ICMP protocol. They are:
- Ping. Send a message to a destination server. You'll get a copy of that message back in return. This command helps you determine availability and speed.
- Traceroute. Send a request and get a note back from every router that handles the request en route to your requested destination.
- Unreachable. In the midst of a traceroute, you may hear that your destination can't be reached. When this happens, you'll be blocked from sending more messages to that location.
ICMP messages are often used to help teams understand whether the data they send is received at all, and if it is, whether it gets there in a timely way. Messages you get back refer to IP operations.
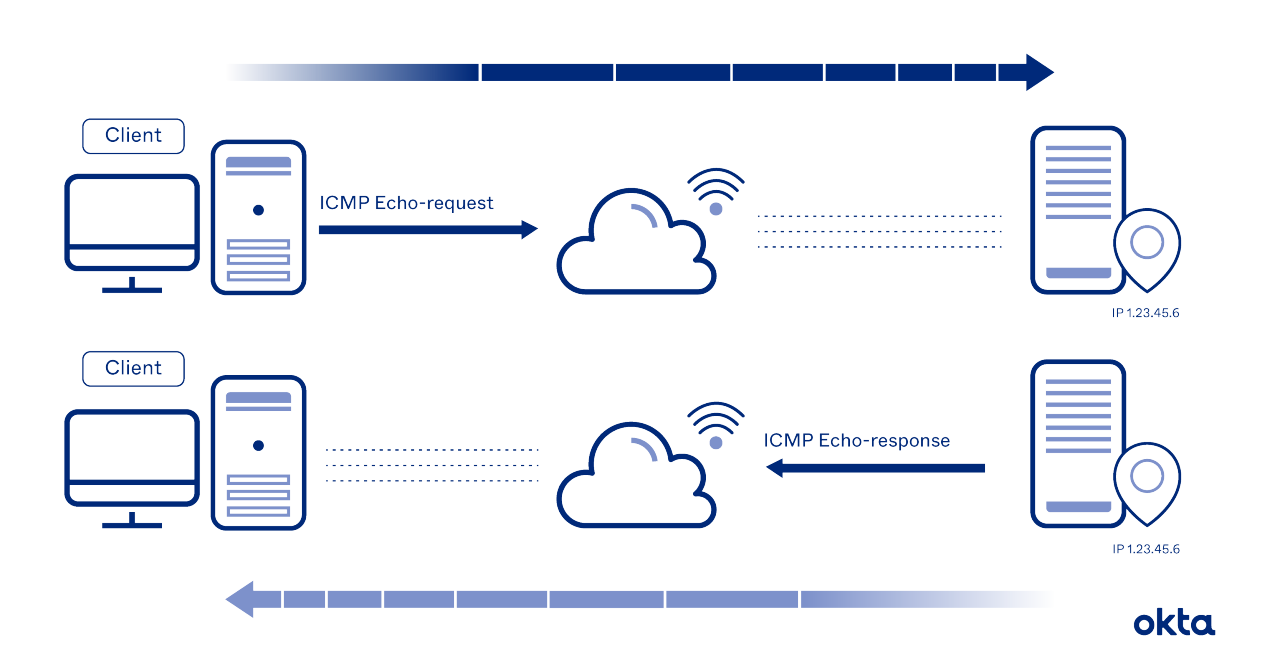
How Does Internet Control Message Protocol Work?
The ICMP protocol requires no handshakes or formal connections. Instead, it operates as a connectionless protocol. And the data you get back is in numeric form. You'll need to decode it to make sense of it.
Developers often use charts to explain what ICMP messages look like.
Each message is made up of four parts.
- Type: This field contains a number that defines the message's general category.
- Code: This field contains a number that offers more information about the message's type.
- Checksum: This field contains a numeric representation of security. Errors or mismatches here indicate that the data has been tampered with.
- Content: Additional information may appear here, depending on your type and code content.
Imagine that your message contains this data:
- Type: 3
- Code: 3
- Checksum: 3 3
You've been told that your destination is unreachable due to an unavailable destination port, and the message hasn't been altered in transit.
ICMP files can take on a different look and feel depending on the type and the trigger. Some contain a summation of the first bits of data you sent, so you can verify the accuracy of the communication. Others don't.
Can an IMCP Packet Trigger an Attack?
If your server faces significant connection issues, your ICMP messages are critical. The data they hold can help you spot the problem and amend it. But the same system can also leave you vulnerable to takedowns.
In a hacker's hands, an ICMP can lead to distributed denial-of-service (DDoS) attacks. There is no known defense against a hack like this, researchers say. Prevention is your best bet.
ICMP attacks can involve:
- Floods. A hacker sends your server hundreds or even thousands of ping requests. Your server must respond to each one, and in time, the server can't handle any other task.
- Size. Hackers send packets larger than those allowed by your protocols. A so-called "ping of death" or "nuke" attack can take down your server in minutes.
- Spoofing. Hackers send ICMP packets with falsified IP addresses. The two begin to ping one another endlessly.
- Tracing. Hackers use the traceroute command to determine your network's topology. That data could be used in a later attack.
Attacks like this can spread. For example, some networks are set up to allow all servers to respond to a ping or request. A hacker's takeover of one server could move to the others, and that could take down your entire structure.
Prevention involves blocking. Allowing commands like traceroute or ping from the open internet could mean leaving your company open to attack. Block those commands when you can, and monitor your network carefully to ensure that you're not missing a hack unfolding right now.
Let Okta Help
For assistance with network communication issues, try Okta’s Access Gateway open virtual appliance.
Our tools are easy to use and understand, and we're always available to answer questions and help with setup concerns. Contact us to get started.
References
Wasted Workday: Employees Lose Over Two Weeks Each Year Due to IT-Related Issues. (March 2016). PR Newswire.
Internet Control Message Protocol. (September 1981). Network Working Group.
Internet Security. (2014). Network and System Security.
Detection and Prevention of ICMP Flood DDOS Attack. (March 2017). International Journal of New Technology and Research.
ICMP Attacks. (March 2018). Infosec.
ICMP Protocol and Its Security. Syracuse University.
What Are We Trying to Prevent? (2002). Managing Cisco Network Security (Second Edition).
Prevent Hacker Probing: Block Bad ICMP Messages. (October 2003). TechRepublic.


