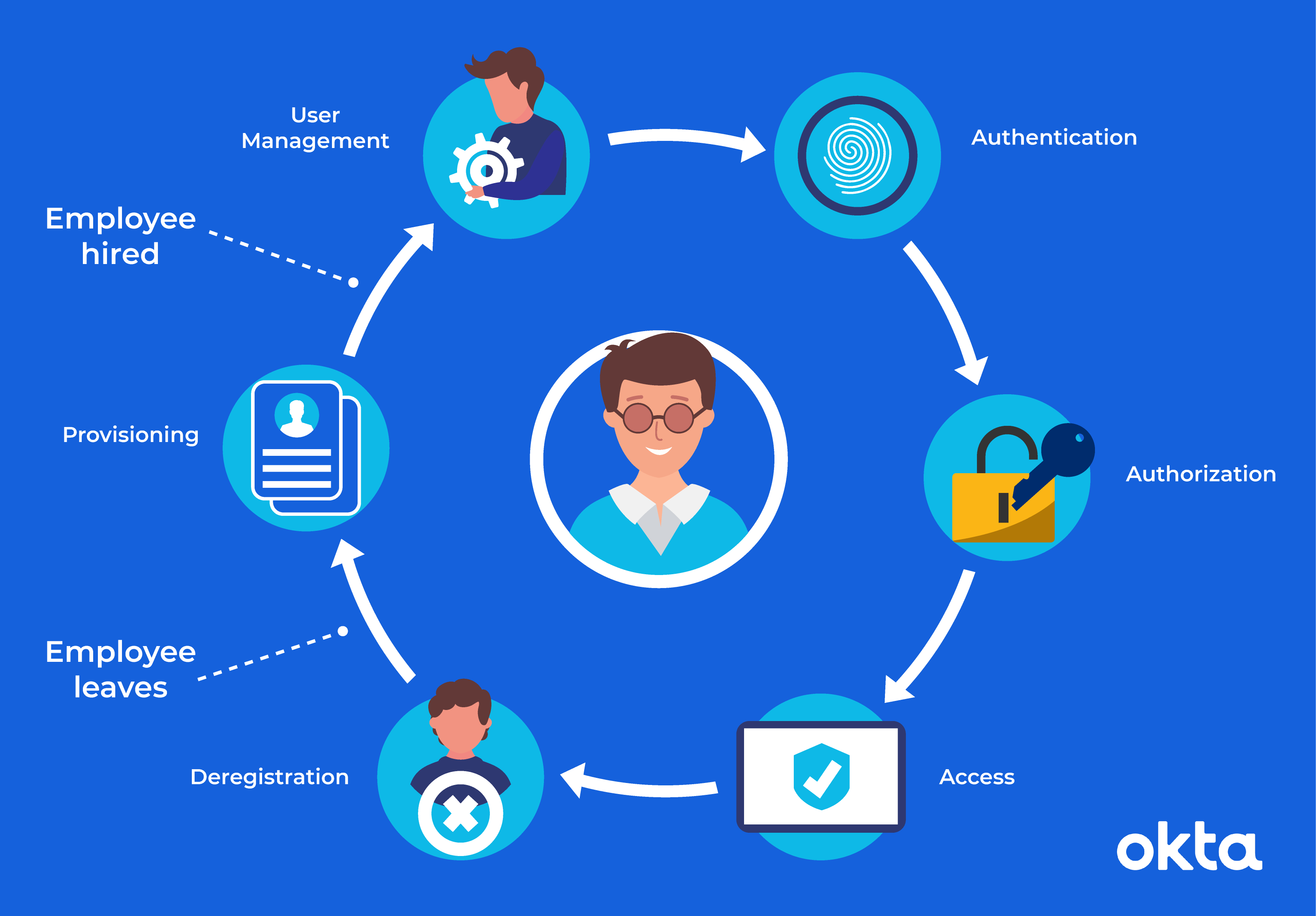
How Does Identity Governance Work?
Your job as an IT professional involves balancing two competing objectives. On the one hand, you must support productivity with quick access to appropriate files. On the other, you must defend your company's private and sensitive documents. And you must work quickly, so you keep the trust and support of your superiors.
Identity governance solutions make your job easier.
Think of identity governance as an umbrella term that encompasses many smaller processes. They all work together to offer robust security while maintaining access.
Identity governance products typically contain features such as:
- Administration. You determine valid users within the system, and you can delete them as needed.
- Analytics. Reports help you understand when pieces of your network are accessed, when they are changed, and who is doing the work.
- Identity management. You ensure that people verify that they are who they claim to be before they gain access.
- Role-based administration. Access to large swaths of the system is determined by the work people do within specific job titles.
When complete, your system helps you understand who has access to what within the server. Rules come from that understanding, and they help you spot early warning signs of security failure. Your system also helps you build strong rules regarding approval processes and oversight roles.
As your system grows, and machine learning helps the system understand even more than you might at first glance, some routine tasks move into the identity governance system and out of your to-do list.
For example, a user might query the system for access to a novel file rather than asking you for help. The system can grant or deny permissions based on learning done over time.
Your governance system can also help you prove compliance with data protection laws, such as the Health Insurance Portability and Accountability Act (HIPAA). That can help you win partnerships or clients in the healthcare space that you might not otherwise be able to.
It could also save your company money. Experts say multiple HIPAA violations could cost a company as much as $25,000. Firm rules and strong reporting make that less likely.
You could use your identity governance system to provide reports regarding:
- Access to a specific file. Offer timestamped data about who did work within the system.
- Standard access. Share information about the departments or job titles that typically work with a set of files, such as health care records.
- Requests. Demonstrate the methods you use to protect data when people ask to see or download it.
Normally, these papers take weeks or months to pull together. But robust identity governance programs handle the work much quicker.
Blending Identity Governance With Existing Systems
A typical identity governance solution is deployed in conjunction with your current systems. Don't think of them as replacing your identity management and audit programs. Instead, think of identity governance as an umbrella covering all of the methods you use to deliver swift access while maintaining security.
In your current identity and access management system, you might have the ability to:
- Add users. When someone joins your organization, you determine what they can do within the system.
- Delete users. When someone shouldn't have access to a specific section of the server or shouldn’t have a login at all, you remove them from active files.
- Manage groups. When a set of people needs to reach part of your server, you grant that access to the entire group.
- Handle problems. When people lose passwords, or they need to reach into something you're blocking, they come to you for assistance.
Work within a standard office, filled with rows of employees, and tackling this work might seem easy. But the explosion of remote work brings additional challenges.
The 2020 coronavirus pandemic put remote work in the spotlight, as everyone needed to work from home. And studies suggest that 99 percent of companies that used a VPN during that time will continue to do so when virus concerns ease.
Handling the demands of remote employees, including some in different time zones, becomes almost impossible. And in an enterprise setting, you may have far more employees than IT professionals.
Deploying an identity governance system means automating workflows and adding technological capabilities. The system will tackle some requests without any help from you, and all along, it will learn more about how to keep your company safe.
Benefits of Identity Governance
Identity governance programs are made with the needs of IT departments, compliance departments, and end users in mind. The benefits are vast, although they can vary from company to company.
Common benefits associated with identity governance include:
- Automation. With roles clearly defined, the system can determine what type of people need access to specific types of files. The access is granted or rescinded accordingly, without a great deal of IT planning and reporting.
- Time savings. More than 75 percent of IT professionals say their job is stressful. They have too many demands coming to them around the clock, with no relief in sight. Handing off common tasks (such as password requests) to a machine means freeing up time and lowering stress levels for your IT team.
- Proven compliance. Firm plans that are outlined and maintained protect sensitive documents. And reports help you showcase the hard work when it's time to prove that you are following data protection laws.
- Robust safety. Computers see things that pass humans by. While you might approve a one-off request from a person you know and like, a program might see the intent behind that request. Safer files are the result.
Your company might experience benefits not mentioned here. When the system is deployed, you may wonder why you didn't get started sooner. But know that you will need to do hard work to get started.
You must have firm process and governance rules in place that will overlay your identity governance program. Without them, your system won't know what rules to enforce. You'll also need to find a partner you can trust.
We can help. The Okta Identity Cloud is a neutral and independent platform that offers secure connection to the right people at the right time. Automation makes administration easy, and our SSO procedures put security first. Find out more about what we can do for you.
References
What Happens if You Break HIPAA Rules? (April 2018). HIPAA Journal.
Business VPN Usage Likely to Remain High Even as the Pandemic Subsides. (May 2020). TechRadar.
Working Remotely Due to Coronavirus? This Technology From Your Employer Is Key. (March 2020). CNBC.
What Is a Business VPN, and How Can It Secure Your Company? (November 2018). Forbes.
Is IT Work Getting More Stressful, Or Is It the Millennials? (May 2015). Computerworld.
Building a Successful Identity Governance and Administration (IGA) Framework. CIO Review.