An intrusion protection system (or IPS) monitors your network around the clock, searching for signs of an intruder or an attack. When something suspicious is found, you're notified while the system takes steps to shut the problem down.
An attack typically involves a security vulnerability. You may not know it's there, and even if you do, you may be leery of applying a patch that could make things worse.
But if you wait to apply a patch, or you don't react to a breach right away, you could allow hackers to take over your system. They could disable all rights and permissions, and they might ask you to pay a hefty ransom before restoring your service.
An IPS doesn't wait for your reaction. When a threat appears, the system moves to block it.
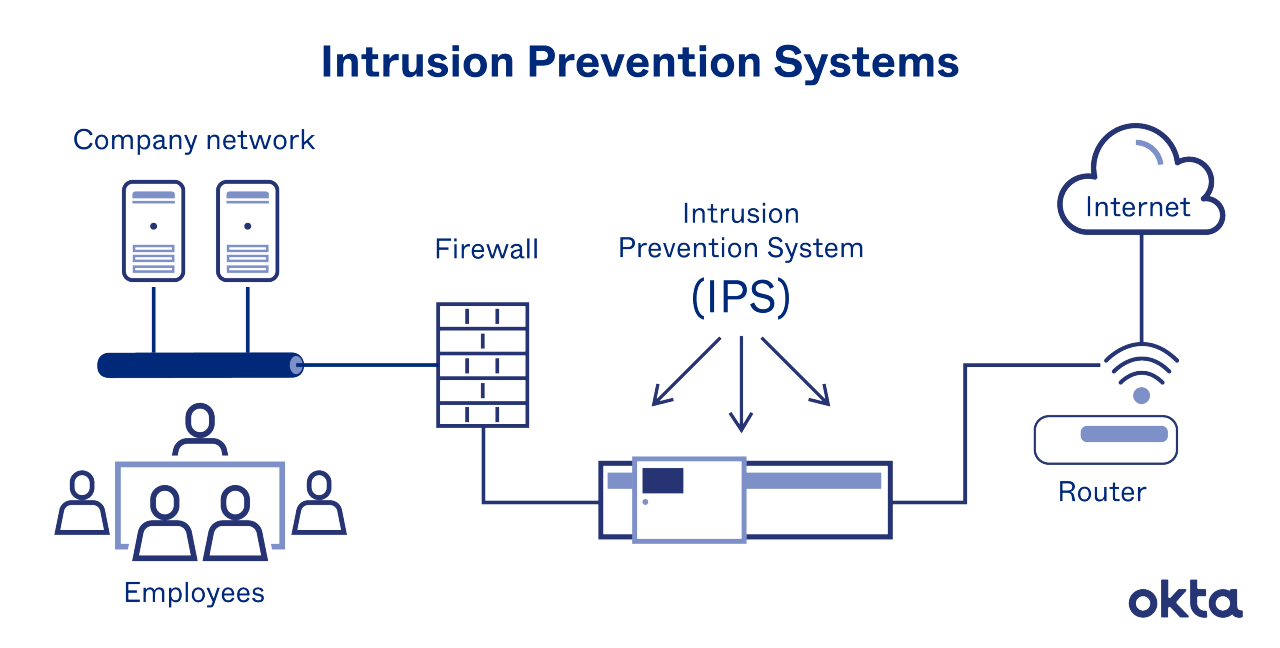
How Does an Intrusion Prevention System Work?
An IPS sits inline, typically right behind your firewall. Every packet must move past it, and as it moves, each packet is inspected. When an anomaly is spotted, the IT administrator is notified. At the same time, the IPS deactivates the threat.
Working in today's IT environment is incredibly stressful. Nearly 30 percent of survey respondents said they've dealt with illnesses related to stress. And 40 percent said they missed time with their families due to work.
An IPS can't eliminate all workplace stress. But the system is always working to protect against an invasion. And once it's set up, you aren't required to weigh in each time a problem is found. The system will work as programmed whether you're available to help or not.
An IPS is typically designed to spot attacks based on:
- Signature. Well-known and successful attacks come with a recognizable code or signature. The system knows these markers, and when they're spotted in your traffic, reactions begin.
- Anomalies. The system samples traffic and looks for episodes that seem somehow different or unusual. Anything out of baseline triggers a response.
Both methods come with strengths and weaknesses. A signature-based system analyzes traffic quickly, and it results in few false positives. But anomaly-based systems are better at spotting new threats. That advanced protection can come with a higher false-positive rate.
When the IPS detects a problem, it responds by terminating the source of the traffic. Then, the system reconfigures the firewall to prevent a future attack, and it scours the network to remove any malignant code records. All work done is logged for your review.
IPS Security & Other Systems
An IPS can work alone, scouring your network and taking action as needed. But it's not unusual for teams like yours to combine an IPS with other types of protections.
One such combination is an IPS/IDS. An intruder detection system (IDS) also scours your network for malicious actors. But when problems are found, an IDS does nothing but tell you about it. No corrective measures are taken unless you program them yourself.
Combining an IPS and an IDS can mean eliminating risks while allowing crucial connections to happen without interference.
While some companies believe in combinations like this, solution fatigue sets in for others. On average, enterprises use 75 different security products on their servers. It's almost impossible to respond to every alert and request when so many programs are in play.
Unified threat programs (or UTMs) combine many different devices, including:
- IDS
- IPS
- Firewalls
- Antivirus scans
- Virtual private networking (VPN)
One dashboard offers a complete look at the state of security for the enterprise, and alerts come in through a unified platform as well. For those weary of too many logins, a UTM could be an ideal solution.
Okta's Solution Set
At Okta, we use identity-driven solutions to support your IPS. With our help, you can both prevent and defend against future cyber attacks. And we'll make sure your system gives you just what you need and nothing you don't. Find out more.
References
Timing the Application of Security Patches for Optimal Uptime. (2002). 2002 LISA XVI.
Is IT Work Getting More Stressful, or Is It the Millennials? (May 2015). Computerworld.
Cybersecurity Spotlight: Signature-Based vs. Anomaly-Based Detection. Center for Internet Security.
Defense in Depth: Stop Spending, Start Consolidating. (March 2016). CSO.
