What is OpenID Connect?
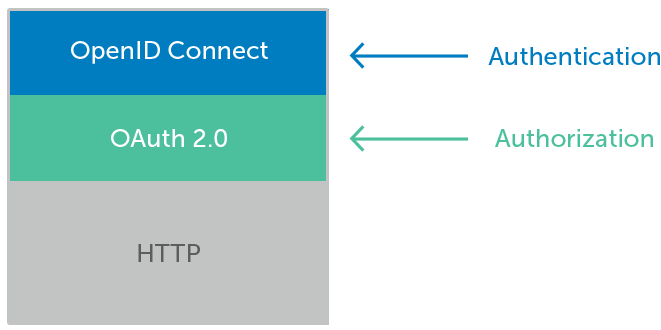
What Does OpenID Connect add to OAuth 2.0?

OAuth 2.0 and OpenID Connect
What is the OpenID Foundation?
The OpenID Foundation is an open standards working group crafting specifications around OpenID and promoting its adoption. OpenID Connect is their primary standard, which defines establishing authentication through the OAuth2.0 framework. The OpenID Foundation provides certifications through a full test suite based on the requirements laid out in the specifications they publish.