ARP poisoning (also known as ARP spoofing) is a cyber attack carried out through malicious ARP messages
An ARP attack is difficult to detect, and once it's in place, the impact is impossible to ignore.
A hacker that successfully implements either ARP spoofing or ARP poisoning could gain control of every document on your network. You could be subject to spying, or your traffic could grind to a halt until you give the hacker what's requested for ransom.
We'll walk you through how an ARP attack works, and we'll give you a few solutions you can implement right away to keep your server safe.
What Is an ARP?
In 2001, developers introduced the address resolution protocol (ARP) to Unix developers. At the time, they described it as a "workhorse" that could establish IP-level connections to new hosts.
The work is critical, especially if your network is constantly growing, and you need a way to add new functionality without authorizing each request yourself.
The basis of ARP is media access control (MAC). As experts explain, an MAC is a unique, hardware-level address of an ethernet network interface card (NIC). These numbers are assigned at the factory, although they can be changed by software.
In theory, an ARP should:
- Accept requests. A new device asks to join the local area network (LAN), providing an IP address.
- Translate. Devices on the LAN don't communicate via IP address. The ARP translates the IP address to a MAC address.
- Send requests. If the ARP doesn't know the MAC address to use for an IP address, it sends an ARP packet request, which queries other machines on the network to get what's missing.
This functionality saves network administrators a lot of time. Requests are handled behind the scenes, and the network does all the cleanup required. But dangers exist.
ARP Attacks: Key Definitions
A malicious developer, hoping to gain access to important data, could expose vulnerabilities and sneak inside, and you may never know it's happening.
Two types of ARP attacks exist.
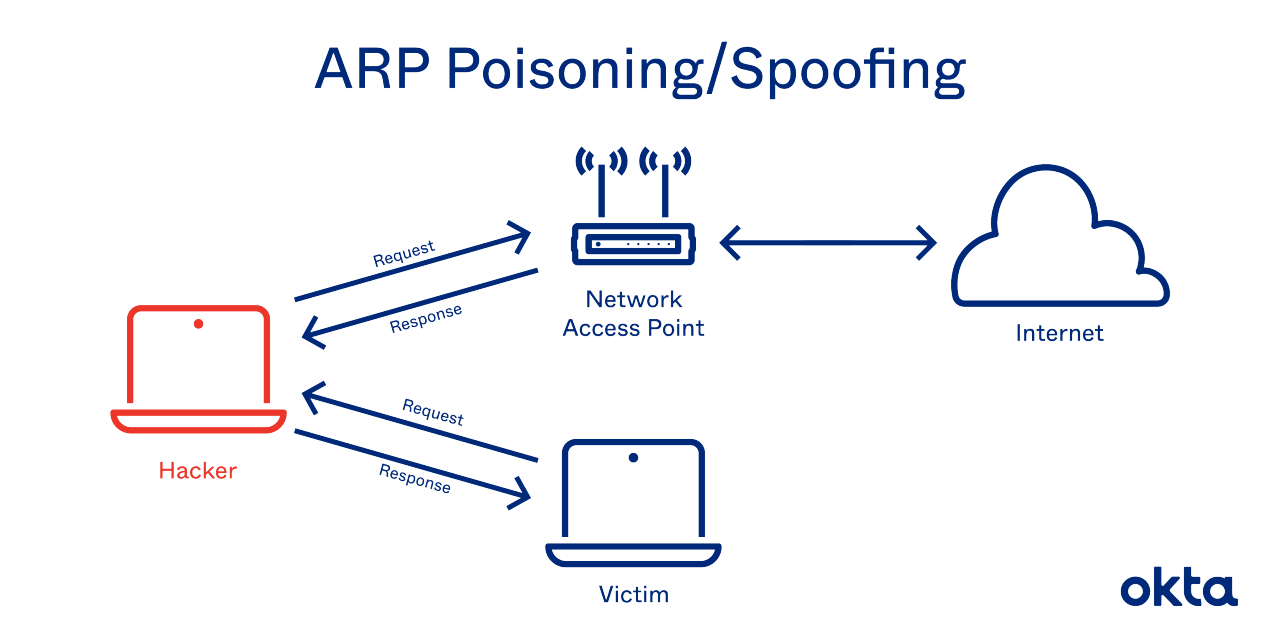
- ARP spoofing: A hacker sends fake ARP packets that link an attacker's MAC address with an IP of a computer already on the LAN.
- ARP poisoning: After a successful ARP spoofing, a hacker changes the company's ARP table, so it contains falsified MAC maps. The contagion spreads.
The goal is to link a hacker's MAC with the LAN. The result means any traffic sent to the compromised LAN will head to the attacker instead.
At the end of a successful ARP attack, a hacker can:
- Hijack. Someone may look over everything that heads to the LAN before releasing it.
- Deny service. Someone may refuse to release anything from the infected LAN unless some kind of ransom is paid.
- Sit in the middle. Someone conducting a man-in-the-middle attack can do almost anything, including altering documents before sending them out. These attacks both threaten confidentiality and reduce user confidence. They are among the most dangerous attacks anyone can perpetrate.
If a hacker wants to take over an end host, the work must be done quickly. ARP processes expire within about 60 seconds. But on a network, requests can linger for up to 4 hours. That leaves plenty of time for a hacker to both contemplate and execute an attack.
Known ARP Vulnerabilities
Speed, functionality, and autonomy were the goals when ARP was developed. The protocol wasn't made with security in mind, and it's proven very easy to spoof and tweak for malicious ends.
A hacker needs just a few tools to make this work.
- Connection: The attacker needs control of one LAN-connected machine. Better yet, the hacker is directly connected to the LAN already.
- Coding skills: The hacker must know how to write up ARP packets that are immediately accepted or stored on the system.
- Outside tools: A hacker could use a spoofing tool, such as Arpspoof, to send out falsified or otherwise inauthentic ARP responses.
- Patience. Some hackers breeze into systems quickly. But others must send dozens or even hundreds of requests before they fool the LAN.
ARP is stateless, and networks tend to cache ARP replies. The longer they linger, the more dangerous they become. One leftover reply could be used in the next attack, which leads to ARP poisoning.
No method of identity proofing exists in a traditional ARP system. Hosts can't determine if packets are authentic, and they can't even determine where they came from.
ARP Poisoning Attack Prevention
Hackers use a predictable series of steps to take over a LAN. They send a spoofed ARP packet, they send a request that connects to the spoof, and they take over. The request is broadcast to all computers on the LAN, and control is complete.
Network administrators can use two techniques to detect ARP spoofing.
- Passive: Monitor ARP traffic and look for mapping inconsistencies.
- Active: Inject falsified ARP packets into the network. A spoofing attack like this helps you identify weak points in your system. Remediate them quickly, and you could stop an attack in progress.
Some developers attempt to write their own code to detect a spoof, but that comes with risks. If the protocol is too strict, excessive false alarms slow down access. If the protocol is too permissive, attacks in progress get ignored, as you have a false sense of security.
Encryption may be helpful. If a hacker digs into your system and gets only garbled text with no decode key, the damage is limited. But you must apply encryption consistently for full protection.
Use of a VPN could be an exceptional source of protection. Devices connect through an encrypted tunnel, and all communication is immediately encrypted.
Protection Tools to Consider
Plenty of companies provide monitoring programs you can use to both oversee your network and spot ARP problems.
These are common solutions:
- Arpwatch: Monitor ethernet activity, including changing IP and MAC addresses, via this Linux tool. Look over the log every day, and access timestamps to understand just when the attack happened.
- ARP-GUARD: Tap into a graphic overview of your existing network, including illustrations of switches and routers. Allow the program to develop an understanding of what devices are on your network and build rules to control future connections.
- XArp: Use this tool to detect attacks happening below your firewall. Get notified as soon as an attack begins, and use the tool to determine what to do next.
- Wireshark: Use this tool to develop a graphic understanding of all the devices on your network. This tool is powerful, but you may need advanced skills to implement it properly.
- Packet filtering: Use this firewall technique to manage network access by monitoring incoming and outgoing IP packets. Packets are allowed or stopped based on source and destination IP addresses, ports, and protocols.
- Static ARP: These ARPs are added to the cache and retained on a permanent basis. These will serve as permanent mappings between MAC addresses and IP addresses.
Work With Okta
We know you're required to keep your systems safe and secure. We also know you may be unsure of where to begin and what steps to take right now. We can help. Discover how Okta can help prevent ARP poisoning attacks.
References
ARP Networking Tricks. (October 2001). Computerworld.
Domain 4: Communication and Network Security (Designing and Protecting Network Security). (2016). CISSP Study Guide (Third Edition).
Fact Sheet: Man-in-the-Middle Attacks. (March 2020). Internet Society.
On Investigating ARP Spoofing Security Solutions. (April 2010). International Journal of Internet Protocol Technology.
Traditional ARP. (January 2017). Practical Networking.
Address Resolution Protocol Spoofing Attacks and Security Approaches: A Survey. (December 2018). Security and Privacy.
ARP Attack Detection Limitations. Security the Infosec Bag.
Arpwatch Tool to Monitor Ethernet Activity in Linux. (April 2013). TecMint.
ARP-GUARD Datasheet. ARP-GUARD.
Home. XArp.
Home. Wireshark.
