Asymmetric encryption (also known as asymmetric cryptography) allows users to encrypt information using shared keys.
You need to send a message across the internet, but you don't want anyone but the intended recipient to see what you've written. Asymmetric encryption can help you achieve that goal.
Asymmetric cryptography techniques allow for extremely secure communication between two parties. Chances are, you've encountered this technology before, even if you never knew what it was called. For example, each time you visit a website with an address starting with "https," you're dealing with asymmetric encryption.
What Is Asymmetric Encryption?
As government officials explain, non-sensitive web traffic just doesn't exist. We share almost every part of our lives online, and we conduct extremely sensitive transactions every day. Both individuals and companies need robust security measures in an environment like this. Asymmetric encryption is made to help.
Security in an asymmetric encryption environment comes from two keys.
- Public key encryption: Anyone can see this and access it.
- Private key encryption: Only the authenticated recipient has access to it.
These two keys are separate but equal, and they're both required to decode a message. If you have only one, decryption is impossible.
Symmetric encryption is asymmetric encryption's counterpart. If you use symmetric encryption, one key both encrypts and decrypts data. A hacker with access to that one key can do both functions.
Asymmetric encryption relies on two keys. One encrypts, and the other decodes. The result is a stronger level of security.
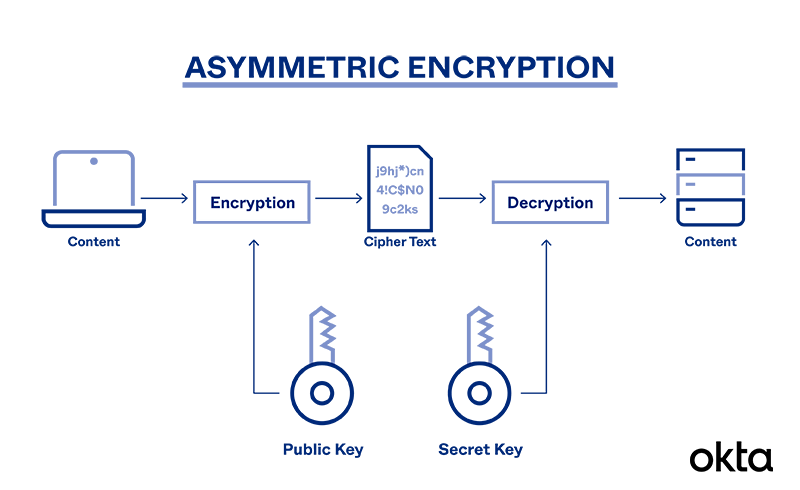
How Does Asymmetric Cryptography Work?
Sensitive messages move through a process of encryption and decryption with public and private keys.
An algorithm starts the process. A mathematical function generates a key pair. Each key is different, but they are related to one another mathematically.
Key generation protocols differ, and the keys they create are different too. In the Microsoft environment, for example, you need about four lines of code to start the development of a pair of asymmetric keys. Other programs work in a similar manner.
Imagine that someone wants to send an encrypted message to another person. The process looks like this:
- Registration: The user and the sender have connected with an official entity that generated both public and private keys.
- Lookup: The sender scours a public-key directory for the recipient's public key information.
- Encrypt: The sender creates a message, encrypts it with the recipient's public key, and sends it.
- Decode: The recipient uses the private key to unscramble the message.
- Reply: If the recipient wants to respond, the process moves in reverse.
Now, imagine that someone wants to communicate with an entity, not an individual. Certificates become important.
SSL certificates, commonly used by websites, work a bit like handshakes. An organization jumps through a hoop, such as registering with an entity and proving ownership, and a certificate is created. When a user accesses a site like this, the user's computer and the website verify private and public keys before information is passed. But once verification happens, the data passes through symmetric encryption, allowing for speed.
Web authentication is relatively easy to understand. We've all used it. But plenty of other entities use the technique to keep their users safe. Bitcoin, for example, leans heavily on asymmetric encryption. A transaction is associated with a public key, but a private key is required for a person to move that transaction from one account to another.
Pros & Cons of Asymmetric Encryption
All site administrators and security-minded individuals require some kind of encryption tool. But asymmetric solutions aren't right for everyone.
Pros
- Security: Without both keys, a hacker can only access useless data.
- Transparency: Public keys can be openly distributed, as losing them will not devolve into a security risk.
- Appearance: Weary consumers demand robust security. Zoom discovered this in 2020, for example, when reporters uncovered lapses in code that meant Zoom calls weren't truly encrypted end to end, as mentioned in their marketing materials. Delivering a truly secure environment is critical to many people.
Cons
- Speed: Systems need time for decryption. Users sending plenty of bulk files will have a long wait.
- Vulnerabilities: Lose a private key, and anyone who finds it can read all messages, even if they're private. A lost key can result in a man-in-the-middle attack too.
- Loss: If you lose your private key, you won't be able to decrypt messages sent to you.
- Long-term sustainability: In the future, quantum computing will break most asymmetric and symmetric approaches.
You may read through this list and decide that the benefits far outweigh the risks. But if you decide that the risks are too great, you could use symmetric encryption instead. You'll have lower risks that stem from loss and speed, but your data could be slightly less secure.
History of Asymmetric Encryption
The idea of protecting data isn't new. In fact, the concepts that lie beneath asymmetric cryptography were defined decades ago.
In 1977, two researchers at Stanford University published a paper with asymmetric encryption concepts clearly defined. They felt the new protocols were required, as consumers were moving from cash-only transactions to digital versions, and they needed ways to protect their finances.
In time, the ideas spread, and soon, individuals, public companies, and private endeavors all scrambled to implement this high level of security. In 1995, asymmetric encryption moved to the mainstream, as the HTTPS protocol was released for widespread use. Now, companies as large as Google use the technique to protect their communications.
We Can Help
Learn more about how Okta uses asymmetric encryption to protect your organization. We can help you understand what solutions work best for your organization, and we can implement them for you. Contact us, and we'll help.
References
Why HTTPS for Everything? CIO Council.
Generating Keys for Encryption and Decryption. (July 2020). Microsoft.
Public Key Directory. (March 2009). The Kumachan.
How to Choose Between These 5 SSL Certificates for Your Site. Neil Patel.
So Wait, How Encrypted Are Zoom Meetings Really? (April 2020). Wired.
New Directions in Cryptography. (November 1076). IEEE Transactions on Information Theory.
Half the Web is Now Encrypted. That Makes Everyone Safer. (January 2017). Wired.
Here's a Simple Introduction on How Browsers Encrypt Your Data. (January 2019). Anton Spaans.
