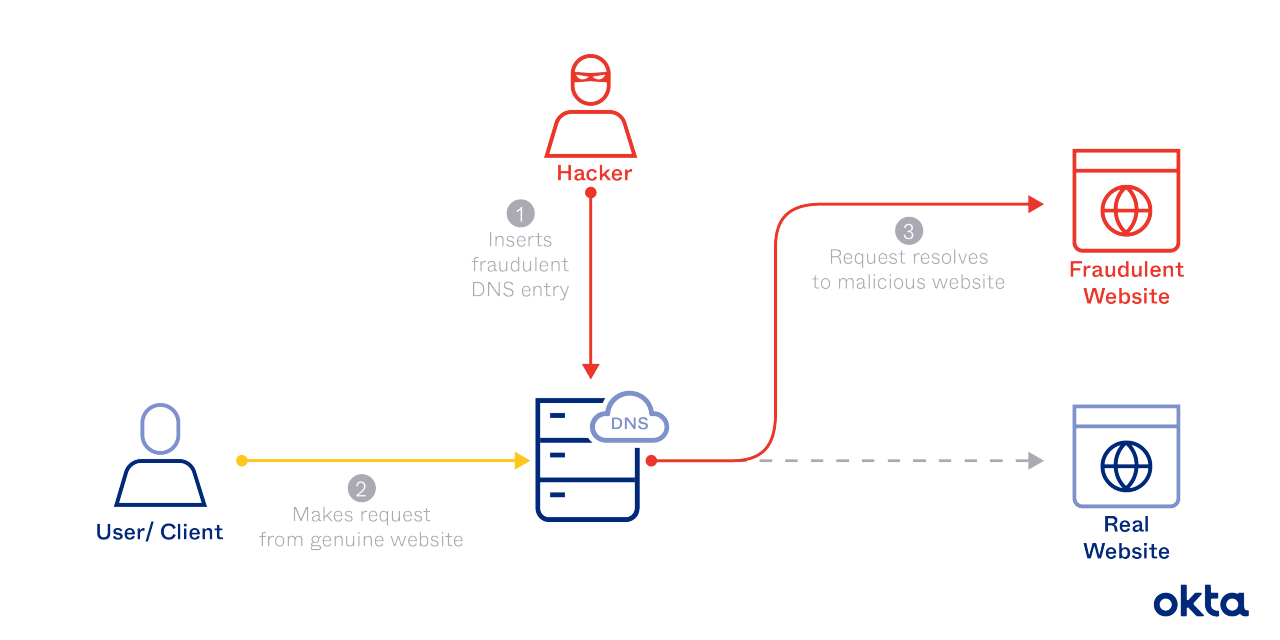
During a DNS poisoning attack, a hacker substitutes the address for a valid website for an imposter. Once completed, that hacker can steal valuable information, like passwords and account numbers. Or the hacker can simply refuse to load the spoofed site.
Someone browsing the web may never know that DNS spoofing is happening. The person may visit a site that looks perfectly normal, and even functions somewhat normally, so everything seems safe.
Or that person may find that a beloved site just won't load. That person may try again for a time or two, but anger could be directed at the company for hosting a site that doesn't work.
Preventing DNS poisoning starts by blocking DNS spoofing. We'll tell you all about how to do just that.
What Is DNS Poisoning?
DNS poisoning is a hacker technique that manipulates known vulnerabilities within the domain name system (DNS). When it's completed, a hacker can reroute traffic from one site to a fake version. And the contagion can spread due to the way the DNS works.
The Chinese government uses DNS poisoning to block access to sites that hold content that officials find objectionable. Users in China may think they have the right address (such as https://www.facebook.com). But due to spoofing, when they type in this address, they head to a completely different server. That server loads something different altogether.
In 2014, Chinese spoofing spread into the wider world. At one point, reporters say, this problem impacted about a seventh of all internet users across the globe. None could load the sites they wanted to see, including Facebook and Twitter.
How Does a DNS Work?
Web developers are encouraged to use short, user-friendly web addresses as they develop their sites. Doing so could help them perform better in search queries, and their addresses help consumers know what pages contain before they click on them. But other computers don't understand the addresses humans use. A DNS helps.
Every time you type an address into your browser:
- A DNS server is contacted. Your computer must reach out to the DNS server for more information.
- The DNS looks up a numerical address. Computers understand server addresses made up of numbers and dots only. If you've never searched for this site before, your computer will ask another server for help.
- A DNS resolver completes the query. Your human-optimized address is switched to a numerical version.
- You're sent to your site. With the correct numerical address, you head to the proper server that hosts your website.
- Data is stored. The internet server you use has a DNS server that stores translations from human addresses to numeric versions. The results of your search are stored here.
This work happens in seconds, and you may not notice the delay. But behind your screen, your computer is reaching out to others to understand where you should go next and what should happen.
The DNS system was developed in 1983, when the internet contained far fewer websites and servers. The developers never dreamed that anyone would want to play with the system or defraud users, so no security measures were built in.
What Does DNS Cache Poisoning Look Like?
You ask to visit a site, and your server picks up a hacker's response. That falsified data is stored, and DNS cache poisoning is complete.
A hacker could do this by:
- Impersonating a server. Your DNS server submits a query for a translation, and the hacker responds very quickly with the wrong answer, long before the correct server can do so.
- Tying up the server. In 2008, researchers discovered that hackers could send thousands of queries to a caching server. Hackers then send thousands of false responses, and in time, they gain control of the root domain and the entire site.
- Exploiting open ports. In 2020, researchers discovered that hackers could send thousands of queries to DNS resolver ports. In time, with this attack, they discover which port is open. Future attacks will focus only on this port.
DNS poising attacks occur because the system is insecure. Your computer holds conversations with servers via the user datagram protocol (UDP). This allows for quick, efficient communication. But no security measures are built in. Your computer doesn't verify the identity of the server it talks to, and it doesn't validate the data that comes back.
Forgery in this environment is relatively easy. If you're not required to prove your identity, and the server you talk to could be owned by anyone at all, you could get falsified information and never know it.
Your DNS Spoofing Plan
If you're a network administrator and your site goes down, your visitors won't blame hackers for the problem. They will blame you and your company. Preventing cache poisoning is critical, but it's not easy.
You could:
- Control your own DNS servers. You'll own the information stored as a result of each query, and you can check it for quality and authenticity on a schedule you set.
- Limit queries. Refuse DNS requests over open ports. You won't get bombarded with queries that could contaminate your data, and you'll be less likely to endure a takeover.
- Look into software. Some DNS software comes with protections built in. Talk with the developers, and ensure you're getting everything you paid for.
Officials are also working on solutions. Domain name system security extensions (DNSSEC) were developed by ICANN, and when they are implemented, they will utilize validation. You'll know that the entity you're working with is authentic, and the data you accept can be trusted.
DNSSEC must be widely deployed to offer full protection. If you require authentication but no one else does, you won't be able to serve up sites on demand. Officials are hoping more companies will use this technology in the future.
Help From Okta
Configuring and protecting a DNS server properly takes time, talent, and persistence. If you don't have the time or expertise to tackle these tasks, we can help.
Our proven techniques can keep your sites up and your data secure. Contact us to learn how Okta can help defend against DNS poisoning.
References
DNS Poisoning Suspected Cause of Huge Internet Outage in China. (January 2014). eWeek.
URLs. MOZ.
Brief History of the Domain Name. Harvard.
How DNS Cache Poisoning Works. (October 2008). Networkworld.
DNS Cache Poisoning, the Internet Attack From 2008, Is Back From the Dead. (November 2020). ARS Technica.
