Executive Summary
Okta Threat Intelligence has observed a social engineering actor abusing the messaging services of attacker-controlled Slack tenants to redirect targeted users to AitM phishing proxies.
Since July 2025 we have observed a cluster of threat activity, tracked
as O-UNC-031, that has used these techniques to target companies in the cryptocurrency, fintech, and customer relationship management (CRM) sectors.
The threat actor employs sophisticated techniques, including the use of Evilginx AitM (Adversary-in-the-Middle) proxy, to harvest user credentials.
The primary objective appears to be unauthorized access to corporate accounts.
Threat Analysis
Abuse of Slack messaging services
A central element of the attack chain is the abuse of legitimate Slack resources. O-UNC-031 creates their own Slack workspaces, which serve as the primary platform for delivering phishing lures to targeted users.
To enhance the credibility of their malicious communications, the threat actor impersonates legitimate administrators and other employees from the targeted companies.
This impersonation takes the form of entering the names of these individuals as the "admin" of attacker-controlled Slack workspaces. The threat actors further bolster the deception by uploading profile pictures of the impersonated individuals, likely sourced from publicly available information.
Once the malicious Slack workspace is configured, the attackers invite targeted users to join the workspace. We observed invitations sent to both the corporate or personal email addresses of targeted users.
Irrespective of whether the targeted user accepts this invitation, the mere act of inviting the user using trusted methods of communication (Slack’s notification features) creates compelling opportunities for phishing.
The threat actor embeds malicious phishing links directly within legitimate email notifications from Slack, making it significantly more challenging for targets to discern malicious intent.
The threat actor sends these specially-crafted phishing messages via direct messages or via @channel mentions to targeted users from within the attacker-controlled workspace. The notifications sent from Slack contain phishing links that redirect users to fake authentication or company login pages described below.
The phishing domains we observed used the following patterns:
- okta-integrations.com
- <target>-onelogin.com
- <target>admin.io
- <target>-okta.com
- slack-<target>.com
- <target>employees.com
- <target>okta.com
Common social engineering pre-texts we observed include:
- informing targets about a purported "payroll processing system" change, requiring them to "connect [their] Okta account to the new payroll system".
- Notifying recipients of "outstanding performance" and inclusion in a new "exclusive new Slack workspace," prompting them to connect their Okta account.
- Examples of phishing URLs used in lures we observed included:
- https://<phishing domain>/slack/connection/2138-4f92-acb7-bk51/,
- https://<phishing domain>/integration/slack/<target>/,
- https://<phishing domain>/integration/payroll/<target>/.
Notably, a phishing attack we tested in our own environment did not require the targeted user to join the workspace to be served up links to phishing pages:
- The Slack workspace allowed an authenticated user to send direct messages (DMs) to a user that had not yet accepted an invitation to join the channel.
- The Slack workspace sent email notifications to the invited user every time they were sent a DM in the workspace, even if they had not yet accepted the invitation.
- By enabling Markdown (called “Markup” in Slack), we were able to modify the text that appears in a hyperlink to make a malicious URI appear benign. We observed attackers using this method of deception.
Slack has removed the attacker-controlled tenants we observed in this campaign.
Adversary-in-the-Middle Phishing
To bypass traditional MFA protections, the threat actor deploys Evilginx, an AitM phishing proxy. This tool allows them to intercept and steal credentials, including multi-factor authentication (MFA) tokens. Evilginx is not effective, however, against Okta customers when users are enrolled in Okta FastPass, passkeys or Smart Cards and phishing resistance is enforced in policy.
Okta Threat Intelligence observed Evilginx employed to mimic a range of login pages, such as Okta Sign-In widgets and other targeted company authentication portals. That being said, we cannot rule out the use of additional phishing kits by this threat actor.
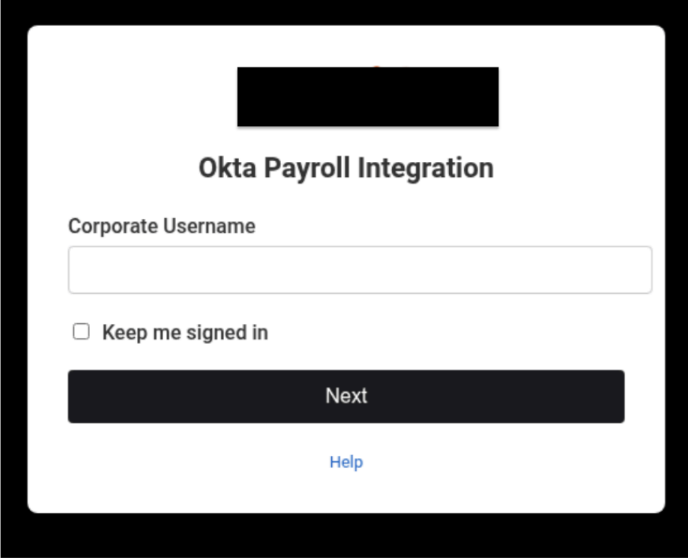 Figure 1: A O-UNC-031 phishing page impersonating Okta
Figure 1: A O-UNC-031 phishing page impersonating Okta
No FastPass please, we're trying to phish you
Okta Threat Intelligence observed phishing lures in this campaign that explicitly instructed targets not to utilize the “Okta FastPass feature”.
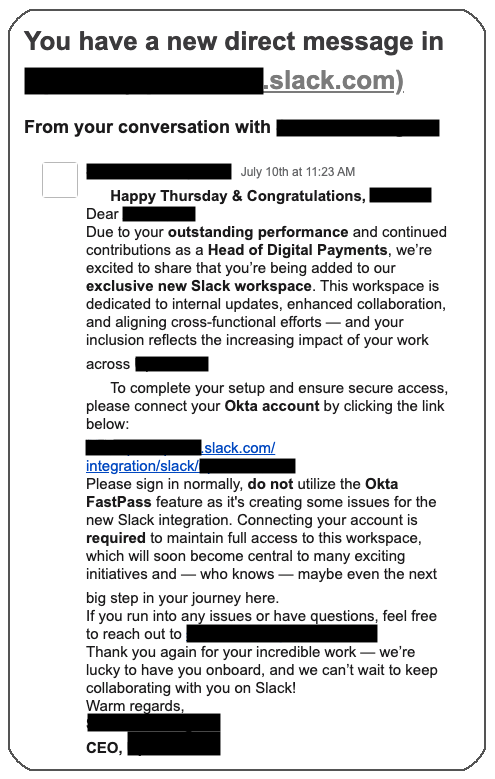 Figure 2: A O-UNC-031 phishing lure sent via a Slack notification
Figure 2: A O-UNC-031 phishing lure sent via a Slack notification
This indicates the threat actor is aware that Okta FastPass is able to both block and detect AitM phishing attempts, but equally that some Okta customers do not enforce phishing resistance in all authentication policies. When phishing resistance is not enforced, a threat actor can try to convince a user to sign-in using a lower assurance factor (Push, OTP, SMS etc).
(Editor’s note: to enforce phishing resistance, an administrator must check the “Phishing Resistant” possession factor constraint, as per the image below.)
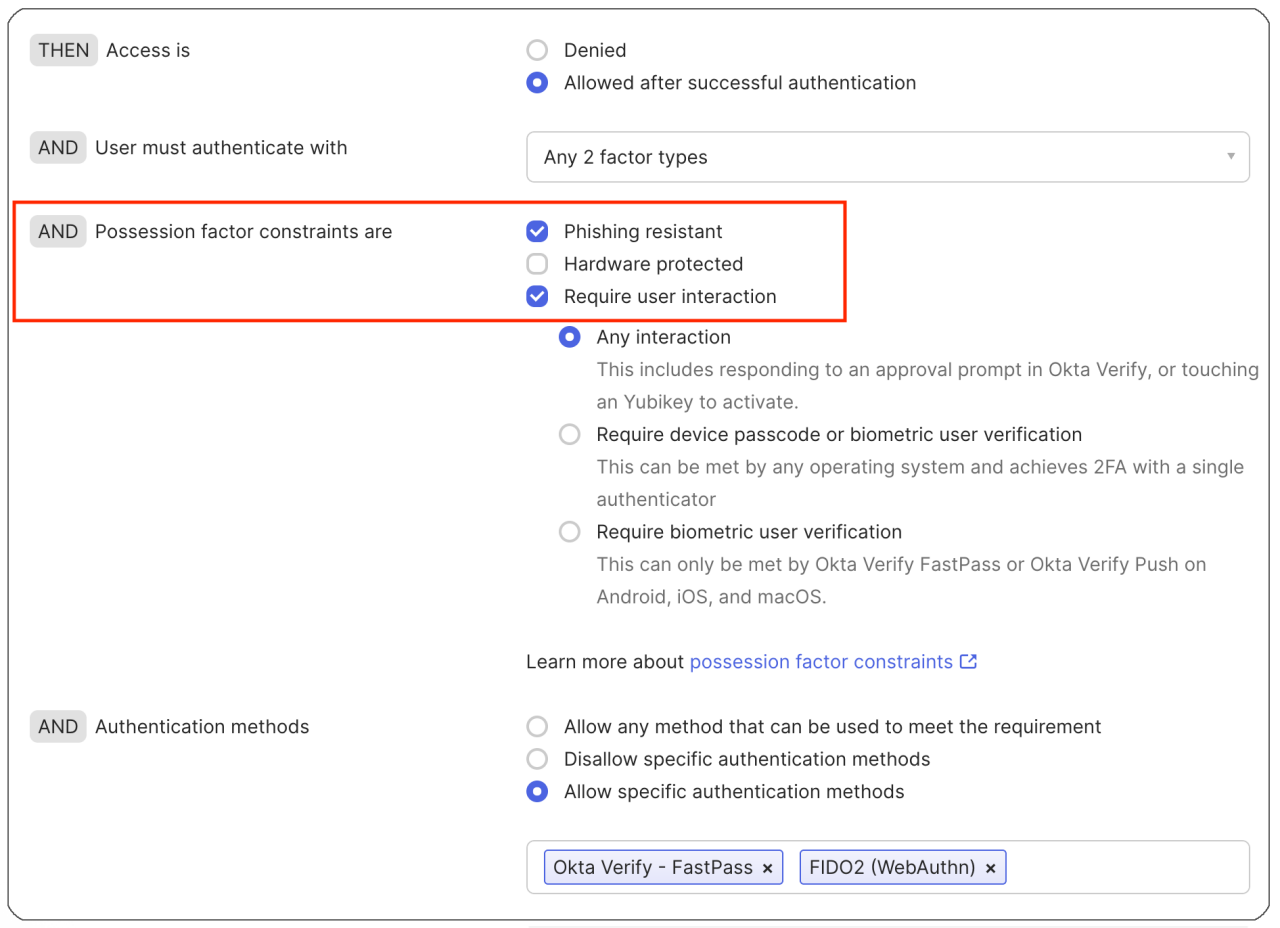 Figure 3: Screenshot from an Okta Identity Engine authentication policy rule
Figure 3: Screenshot from an Okta Identity Engine authentication policy rule
Other Tactics, and Procedures
The phishing domains used by this threat actor were often hosted on virtual private servers (VPSs) acquired from services like BitLaunch. The use of providers like BitLaunch is advantageous for the threat actor due to their support for cryptocurrency payments, which enhances anonymity, and the ability to rapidly deploy VPS for short-lived campaigns. Similarly, domains are typically registered through NICENIC INTERNATIONAL, likely favored by the threat actor because it also accepts cryptocurrency payments and may offer perceived lax or slow abuse response procedures, or specific privacy features.
The WHOIS information for these domains has been observed to include the following registrant information:
- Registrant State/Province: kond
- Registrant Country: AW
Following the successful harvesting of a target’s user credentials, O-UNC-031 has been observed to use Mullvad VPN and residential IPs for their authentication attempts to the targeted organizations.
Threat Response
What we’re doing:
We’re actively engaged in the following activities to mitigate this threat:
- Continuously monitoring for newly registered phishing domains and infrastructure associated with this campaign.
- Proactively filing abuse reports with relevant registrars and hosting providers to initiate takedown requests for identified malicious sites.
- Providing guidance and assistance to organizations to enhance the security of their Okta environments and investigate any suspicious activity related to potentially compromised accounts.
Protective Controls
Recommendations for customers
- Enroll users in strong authenticators such as Okta FastPass, FIDO2 WebAuthn and smart cards.
- Enforce phishing resistance in authentication policies and disable weaker sign-in methods.
- Okta authentication policies can also be used to restrict access to user accounts based on a range of customer-configurable prerequisites. We recommend administrators restrict access to sensitive applications to devices that are managed by Endpoint Management tools and protected by endpoint security tools. For access to less sensitive applications, require registered devices (using Okta FastPass) that exhibit indicators of basic hygiene.
- Deny or require higher assurance for requests from rarely-used networks. With Okta Network Zones, access can be controlled by location, ASN (Autonomous System Number), IP, and IP-Type (which can identify known anonymizing proxies).
- Okta Behavior and Risk evaluations can be used to identify requests for access to applications that deviate from previously established patterns of user activity. Policies can be configured to step-up or deny requests using this context.
- Train users to identify indicators of suspicious emails, phishing sites and common social engineering techniques used by attackers. Make it easy for users to report potential issues by configuring End User Notifications and Suspicious Activity Reporting.
- Document, evangelize and adhere to a standardized process for validating the identity of remote users that contact IT support personnel, and vice versa. Take a "Zero Standing Privileges" approach to administrative access. Assign administrators Custom Admin Roles with the least permissions required for daily tasks, and require dual authorization for JIT (just-in-time) access to more privileged roles.
- Apply IP Session Binding to all administrative apps to prevent the replay of stolen administrative sessions.
- Enable Protected Actions to force re-authentication whenever an administrative user attempts to perform sensitive actions.
Observing and responding to phishing infrastructure:
- Review application logs (Okta logs, web proxies, email systems, DNS servers, firewalls) for any evidence of communication with any such suspicious domains.
- Monitor the domains regularly to see if the contents change.
- If content hosted on the domain violates copyright or legal marks, consider providing evidence and issuing a takedown request with the domain registrar and/or web hosting provider.
Appendix A: Indicators of Compromise
This is an ongoing investigation, and additional IOCs may be identified as the campaign evolves. Organizations are advised to remain vigilant and implement the recommended mitigation strategies. Below are the IOCs observed.
| Type | Indicator | Comment | Seen at |
|---|---|---|---|
| IP address | 157.245.242[.]172 | Phishing infrastructure | Jul 11, 2025 |
| IP address | 157.245.227[.]25 | Phishing infrastructure | Jul 9, 2025 |
| IP address | 157.245.129[.]184 | Phishing infrastructure | Jul 9, 2025 |
| IP address | 64.190.113[.]119 | Phishing infrastructure | Jul 4, 2025 |
| IP address | 157.245.134[.]111 | Phishing infrastructure | Jul 4, 2025 |
| IP address | 167.99.236[.]196 | Phishing infrastructure | Jul 3, 2025 |
| IP address | 206.188.197[.]224 | Phishing infrastructure | Jul 2, 2025 |
| IP address | 50.189.65[.]60 | Phishing infrastructure | Jul 8, 2025 |
| VPN provider | Mullvad VPN | VPN provider | 2025-07 |
| Whois | kond | Registrant State/Province | 2025-07 |
| Whois | AW | Registrant Country2025-07 | 2025-07 |
Additional indicators are also available from an unredacted advisory that Okta customers can download at security.okta.com.
A note on estimate language
Okta Threat Intelligence teams the following terms to express likelihood or probability as outlined in the US Office of the Director of National Intelligence Community Directive 203 - Analytic Standards.
| Likelihood | Almost no chance | Very unlikely | Unlikely | Roughly even chance | Likely | Very likely | Almost certain(ly) |
|---|---|---|---|---|---|---|---|
| Probability | Remote | Highly improbable | Improbable | Roughly even odds | Probable | Highly Probable | Nearly Certain |
| Percentage | 1-5% | 5-20% | 20-45% | 45-55% | 55-80% | 80-95% | 95-99% |




