Executive Summary
Okta Threat Intelligence has been actively tracking a financially motivated threat actor known as O-TA-054 (aka Payroll Pirates) since August 2024.
O-TA-054 leverages phishing campaigns to target employees of organizations operating in different industries, including Okta customers. These campaigns use lures that impersonate banking, human resources (HR) and employee rewards applications, as well as government self-service websites. Distribution of these phishing sites occurs via malicious Google advertisements (malvertising)[1].
The primary objective of O-TA-054 is to manipulate victims’ banking details across HR systems and payroll-related services, unemployment benefits programs, health savings accounts, and retirement accounts to steal victims' funds [2].
In an April 2025 campaign, O-TA-054 leveraged phishing pages that mimicked the Okta Sign-In Widget of the targeted organizations. This allowed the threat actor to steal credentials and take over employee accounts, then pivot to target Workday applications, with the objective of manipulating banking details to divert salaries.
This advisory details the observed Tactics, Techniques, and Procedures (TTPs) and provides relevant Indicators of Compromise (IOCs) associated with this active threat.
Threat Analysis
Analysis of the April 2025 campaign has identified the following infrastructure used to host the malicious phishing pages, which present a fraudulent Okta Sign-In Widget:
- 172.67.148[.]2 - AS13335 - Cloudflare, Inc.
- 77.37.76[.]235 - AS47583 - Hostinger International Limited
- 67.205.29[.]179 - AS26347 - New Dream Network, LLC
- 147.93.54[.]103 - AS47583 - Hostinger International Limited
- 178.218.166[.]217 - AS12417 - Plus Hosting Grupa d.o.o.
Account takeover activity:
Following the successful compromise of credentials, the threat actor(s) have been observed attempting, and successfully authenticating, from the following IP addresses:
- 104.136.213[.]185 - AS33363 - Charter Communications, Inc
- 12.183.232[.]42 - AS7018 - AT&T Enterprises, LLC
- 160.7.237[.]192 - AS36223 - Spanish Fork City
- 162.251.115[.]229 - AS11059 - MIFFLIN COUNTY WIRELESS LLC
- 168.235.210[.]141 - AS13428 - Surf Air Wireless, LLC
- 172.220.33[.]240 - AS20115 - Charter Communications LLC
- 174.68.140[.]219 - AS22773 - Cox Communications Inc.
- 212.102.44[.]112 - AS60068 - Datacamp Limited
- 45.48.112[.]118 - AS20001 - Charter Communications Inc
- 45.49.235[.]225 - AS20001 - Charter Communications Inc
- 71.224.199[.]104 - AS7922 - Comcast Cable Communications, LLC
- 74.101.135[.]58 - AS701 - Verizon Business
- 98.54.180[.]132 - AS7922 - Comcast Cable Communications, LLC
The threat actor uses a mix of VPN and residential proxy IP addresses when signing in to compromised accounts to enhance anonymity and evade traditional detection mechanisms.
Once the threat actor compromised the employee's account, they pivoted to Workday and updated the banking information to divert their salary.
Phishing Kit Characteristics:
- The analyzed phishing kit appears to be relatively simple, focusing on direct credential capture without the implementation of an Adversary-in-the-Middle (AitM) proxy.
- The phishing pages are often located within the /online/ directory. The root directory often hosts a benign landing page, with thematic variations (e.g., retail, workforce, reward) that we assess to be tailored to the targeted organization, potentially as a form of obfuscation.
- The phishing page is allegedly designed to handle various MFA methods: phone (text and call), Okta Code, and Okta Push, with different sections displayed based on user interaction.
- Upon clicking the "login" button, the script captures the username and password and sends them via a POST request to xxx.php.
- After the initial login, the script polls the check.php endpoint periodically to determine the next stage.
- Based on the response from check.php, the user is either prompted for an MFA method or, if an error occurs, the page reloads.
- The polling mechanism involving check.php suggests a server-side component tracking the login and MFA process.
- JavaScript and AJAX are used for the core functionality of the phishing page and communication with the attacker's infrastructure.
<script type="text/javascript" src="https://code.jquery.com/jquery-3.7.0.min.js"></script>
<script type="text/javascript">
$('a').click(function(e){
e.preventDefault();
});
$('#input36').click(function(){
$('label[for='+ this.id +']').toggleClass('checked');
});
$(document).on("click", '#nextButton', function(e) {
e.preventDefault();
var username = $('#input28').val();
if(username.length > 3) {
console.log(username);
$('.loginBlock').hide();
$('.passBlock').show();
$('.identifier').html(username);
} else {
return;
}
});
$('.button-show').click(function(){
var type = $('#input77').attr('type');
if(type == "text"){
$('#input77').attr('type','password');
} else {
$('#input77').attr('type','text');
}
});
$(document).on('click', '.js-cancel', function(e) {
location.reload();
});
$(document).on('click', '.js-switchAuthenticator', function(e) {
$('.methodBlock').show();
$('.phoneMethodsBlock').hide();
$('.phoneCodeBlock').hide();
$('.oktaCodeBlock').hide();
$('.oktaPushBlock').hide();
});
$(document).on("click", '#loginButton', function(e) {
e.preventDefault();
var username = $('#input28').val();
var password = $('#input77').val();
if(username.length > 3 && password.length > 3) {
$('#loginButton').attr('disabled','disabled');
console.log(username,password);
Figure 1: JavaScript code to post credentials using the xxx.php
Background
O-TA-054 has been actively targeting organizations across various industries, including wholesale trade, finance and banking, retail, construction and engineering, transportation, and government entities. Our analysis indicates a significant focus on the financial and banking sectors, human resources and payroll-related services, as well as governmental self-service websites.
The threat actor tactic involves the creation of phishing sites impersonating the targeted organizations’ login pages, in addition to login pages of HR and payroll-related services, such as MyPAU, Kaiser HR (Kaiser employee portal), PrimePoint HR, Streamline Payroll, Dayforce, and HCMBamboo HR. This focus highlights the threat actor's intent to exploit employee data and financial information.
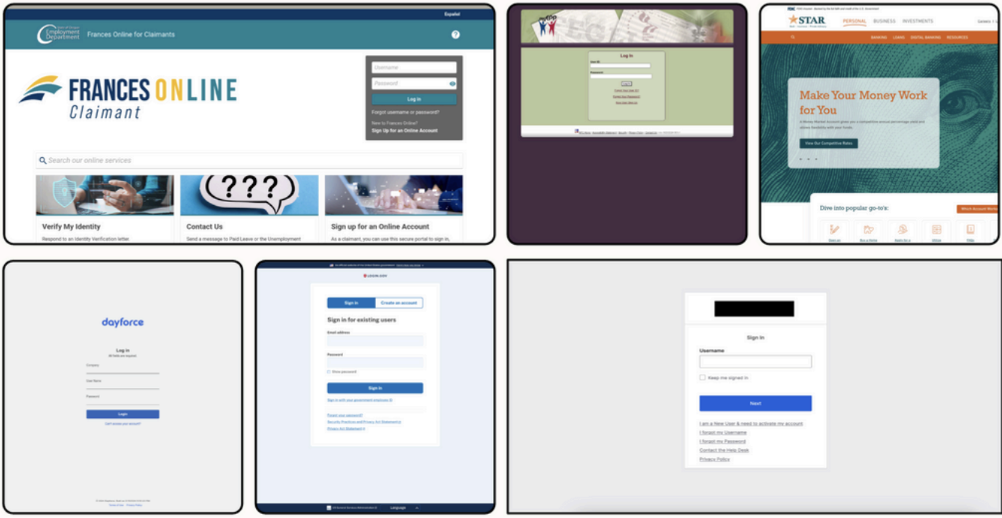 Figure 2. Impersonation phishing site login pages
Figure 2. Impersonation phishing site login pages
O-TA-054 primarily leverages malvertising campaigns through Google Ads to distribute malicious advertisements. These malicious advertisements impersonate legitimate company and government service websites, often appearing as sponsored at the top of search results with look-alike domains. Unsuspecting employees searching for HR portals or other financial services click these ads and are directed to the phishing sites. These fake login pages are designed to deceive victims into entering their credentials and other sensitive financial information, which are then intercepted by the threat actor, allowing them to take-over the employees account [1][2][3].
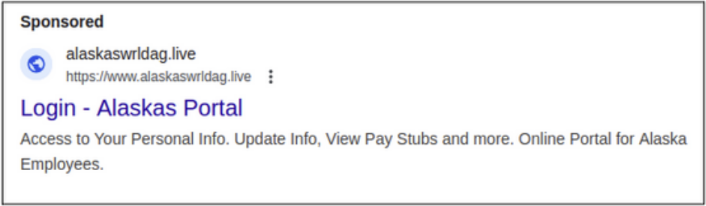 Figure 3. Impersonation search results for Alaskas Portal
Figure 3. Impersonation search results for Alaskas Portal
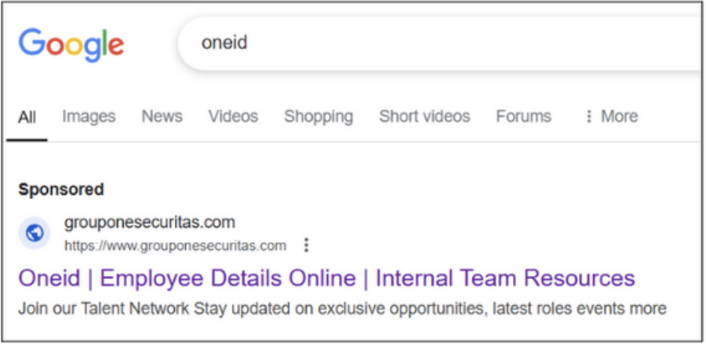 Figure 4. Impersonation search results for Oneid
Figure 4. Impersonation search results for Oneid
The successful compromise allows the threat actors to manipulate the victim's financial details for the purpose of stealing their funds.
What We’re Doing
We’re actively engaged in the following activities to mitigate this threat:
- Continuously monitoring for newly registered phishing domains and infrastructure associated with this campaign.
- Proactively filing abuse reports with relevant registrars and hosting providers to initiate takedown requests for identified malicious sites.
- Providing guidance and assistance to organizations to enhance the security of their Okta environments and investigate any suspicious activity related to potentially compromised accounts.
Customer Recommendations
Protective Controls:
- Enroll users in strong authenticators such as Okta FastPass, FIDO2 WebAuthn and smart cards and enforce phishing resistance in policy.
- Okta authentication policies can also be used to restrict access to user accounts based on a range of customer-configurable prerequisites. We recommend administrators restrict access to sensitive applications to devices that are managed by Endpoint Management tools and protected by endpoint security tools. For access to less sensitive applications, require registered devices (using Okta FastPass) that exhibit indicators of basic hygiene.
- Deny or require higher assurance for requests from rarely-used networks. With Okta Network Zones, access can be controlled by location, ASN (Autonomous System Number), IP, and IP-Type (which can identify known anonymizing proxies).
- Okta Behavior and Risk evaluations can be used to identify requests for access to applications that deviate from previously established patterns of user activity. Policies can be configured to step-up or deny requests using this context.
- Train users to identify indicators of suspicious emails, phishing sites and common social engineering techniques used by attackers. Make it easy for users to report potential issues by configuring End User Notifications and Suspicious Activity Reporting.
We’re actively engaged in the following activities to mitigate this threat:
- Document, evangelize and adhere to a standardized process for validating the identity of remote users that contact IT support personnel, and vice versa. Take a "Zero Standing Privileges" approach to administrative access. Assign administrators Custom Admin Roles with the least permissions required for daily tasks, and require dual authorization for JIT (just-in-time) access to more privileged roles.
- Apply IP Session Binding to all administrative apps to prevent the replay of stolen administrative sessions.
- Enable Protected Actions to force re-authentication whenever an administrative user attempts to perform sensitive actions.
Observing and responding to phishing infrastructure:
- Review application logs (Okta logs, web proxies, email systems, DNS servers, firewalls) for any evidence of communication with any such suspicious domains.
- Monitor the domains regularly to see if the contents change.
If content hosted on the domain violates copyright or legal marks, consider providing evidence and issuing a takedown request with the domain registrar and/or web hosting provider.
References
[1] Lowe’s employees phished via Google ads
https://www.malwarebytes.com/blog/news/2024/09/lowes-employees-phished-via-google-ads
[2] Cyber Criminals Impersonating Employee Self-Service Websites to Steal Victim Information and Funds
https://www.ic3.gov/PSA/2025/PSA250424
[3] Hunting Payroll Pirates: Silent Push Tracks HR Redirect Phishing Scam
https://www.silentpush.com/blog/payroll-pirates/
Appendix A: Indicators of Compromise
| Type | Indicator | Comment | Seen at |
|---|---|---|---|
| IP address | 172.67.148[.]2 | AS13335 - Cloudflare, Inc. | 2025-04-19 |
| IP address | 77.37.76[.]235 | AS47583 - Hostinger International Limited | 2025-04-22 |
| IP address | 67.205.29[.]179 | AS26347 - New Dream Network, LLC | 2025-04-18 |
| IP address | 147.93.54[.]103 | AS47583 - Hostinger International Limited | 2025-04-19 |
| IP address | 178.218.166[.]217 | AS12417 - Plus Hosting Grupa d.o.o. | 2025-04-18 |
| IP address | 104.136.213[.]185 | AS33363 - Charter Communications, Inc | 2025-04-17 |
| IP address | 12.183.232[.]42 | AS7018 - AT&T Enterprises, LLC | 2025-04-15 |
| IP address | 160.7.237[.]192 | AS36223 - Spanish Fork City | 2025-04-18 |
| IP address | 162.251.115[.]229 | AS11059 - MIFFLIN COUNTY WIRELESS LLC | 2025-04-16 |
| IP address | 168.235.210[.]141 | AS13428 - Surf Air Wireless, LLC | 2025-04-14 |
| IP address | 172.220.33[.]240 | AS20115 - Charter Communications LLC | 2025-04-18 |
| IP address | 174.68.140[.]219 | AS22773 - Cox Communications Inc. | 2025-04-17 |
| IP address | 212.102.44[.]112 | AS60068 - Datacamp Limited | 2025-04-14 |
| IP address | 45.48.112[.]118 | AS20001 - Charter Communications Inc | 2025-04-15 |
| IP address | 45.49.235[.]225 | AS20001 - Charter Communications Inc | 2025-04-15 |
| IP address | 71.224.199[.]104 | AS7922 - Comcast Cable Communications, LLC | 2025-04-18 |
| IP address | 74.101.135[.]58 | AS701 - Verizon Business | 2025-04-15 |
| IP address | 98.54.180[.]132 | AS7922 - Comcast Cable | 2025-04-16 |
A note on estimate language
Okta Threat Intelligence teams the following terms to express likelihood or probability as outlined in the US Office of the Director of National Intelligence, Intelligence Community Directive 203 - Analytic Standards.
| Likelihood | Almost no chance | Very unlikely | Unlikely | Roughly even chance | Likely | Very likely | Almost certain(ly) |
|---|---|---|---|---|---|---|---|
| Probability | Remote | Highly improbable | Improbable | Roughly even odds | Probable | Highly Probable | Nearly Certain |
| Percentage | 1-5% | 5-20% | 20-45% | 45-55% | 55-80% | 80-95% | 95-99% |




