Passwordless authentication: where to start
Let’s face it: we’re all tired of passwords. They’re a major pain for users and not nearly as effective at securing accounts as they pretend to be. Thankfully, there is a better way! We are excited to announce a new set of passwordless capabilities in Okta that will allow you to deliver seamless auth experiences to all users!
In this post, we’ll explore the different ways you can use Okta as the foundation to deliver a passwordless login experience and share how to get started with passwordless authentication.
Why go passwordless?
In my previous post, “What is Passwordless Authentication?”, I broke down some of the problems with passwords and the benefits of going passwordless.
To summarise, passwordless authentication is an emerging authentication method that is picking up steam because the proliferation of passwords has begun to hinder both user experience and security. Organisations that go passwordless benefit from threat-resistant login options, enhanced admin visibility and control, lower total cost of ownership and an excellent, scalable user experience.
Going passwordless with Okta
There are many different forms by which passwordless can be delivered. When you choose Okta as your identity platform, you get the flexibility in how you want to deliver a passwordless login experience.
Let’s go through the different methods by which Okta delivers passwordless.
1. Factor Sequencing
This is a new feature in Okta which allows organisations to deliver passwordless login experiences for their workforce and customers. Factor sequencing addresses two specific use cases:
1) End users can now use what was their secondary factor as their primary. For example, login into Okta with just username + Okta Verify or just username + SMS OTP, therefore bypassing the password.
2) Administrators can create a sequence of factors best suited for their user groups. For example, require Okta Verify + biometrics during login, or present Okta Verify before entering a password.
2. WebAuthn
WebAuthn is the new global standard of web based authentication. WebAuthn is a browser-based API that allows web apps to simplify and secure user authentication by using public-key cryptography to protect users from phishing. By combining WebAuthn with the factor sequencing capability mentioned above, users can authenticate to your apps using biometric factors that support WebAuthn, without entering a password. Examples of WebAuthn supported factors include Android Fingerprint, Touch Bar on MacBook and Windows Hello, as well as security keys such as Security Key by Yubico. You can learn more about WebAuthn here.
3. Email Magic Link
An Email Magic Link is an authenticated URL which can be sent to your customers and consumers to simplify the login process to your application with just one click. For example, a user may enter their email address into your application and, instead of entering a password, the Email Magic Link is delivered to their inbox to facilitate a passwordless login process. Once the user clicks on the link, they are redirected back to your application with a login session.
We’re working hard to deliver this feature for our customers and you can expect to see it available over the next few months.
4. Desktop Single Sign-On (IWA Web App & Agentless)
This is a feature you may already be familiar with because it has been in the product for a few years. With Desktop Single Sign-On, end users log into their Windows or MacOS machine with their Active Directory credentials, which automatically logs them into Okta-managed apps. This means they do not need to enter any additional credentials when opening up their browser and accessing an Okta-managed app.
5. Smart Card/PIV Card
This is another feature which has been in the product for a few years. With this feature enabled, end users log into Okta with a PIV card or other smart card, therefore bypassing any password requirement. The PIV and/or smart card is the user’s primary login factor. This feature can be used with any x.509 compliant digital certificate.
6. Device Trust integrations
You may already be using Device Trust, but did you know Device Trust can also be used to deliver a passwordless login experience on desktop and mobile? When using Okta’s SAML based approach to Device Trust, you can use the built-in passwordless login capabilities within technologies like VMware Workspace ONE to deliver seamless login experiences on managed devices.
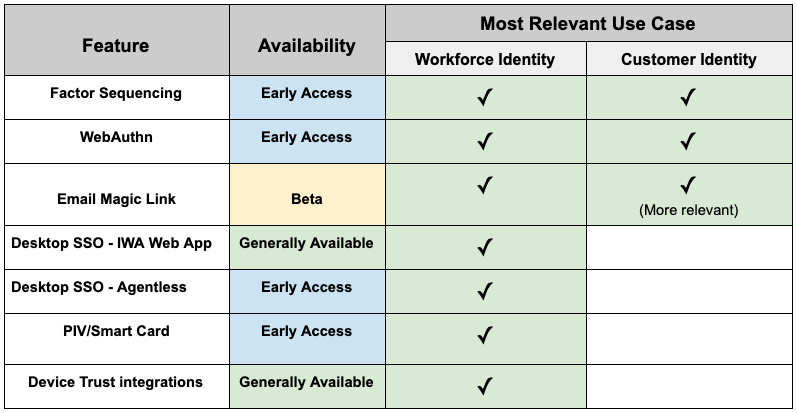
To recap, here is an overview of the current availability of the features mentioned above and which feature is most applicable to each use case.
What does going passwordless mean for your business?
Now that you’re familiar with how Okta can help you deliver a passwordless login experience for users, customers and consumers, let’s cover how the use cases differ in Workforce Identity vs Customer Identity.
You’ll find that all the features mentioned above could be used for Workforce Identity use cases but, on the Customer Identity side, some of these features are not as relevant.
For your workforce:
You can pick and choose which features make the most sense based on your organisation’s needs and how your IT landscape is set up. Here is an example of how you may configure a few of these features for Workforce use cases -
- Login to Windows 10 machines that are joined to your Active Directory and you’re automatically authenticated to Okta. When an end user is in the office network and logs into their device using Active Directory credentials, they will not see any additional browser prompts for authentication when accessing Okta managed apps. (Desktop SSO)
- Log into Okta via Touch Bar on your MacBook. End users open up a browser, enter their username and will be prompted for their fingerprint before logging into Okta. (WebAuthn)
- A passwordless login experience to native mobile apps (i.e. Outlook, Salesforce, Box etc) for iOS and Android devices that are managed by Workspace ONE UEM. Workspace ONE can facilitate a passwordless login experience via One Touch SSO. (Device Trust integrations)
For your customers:
You can pick and choose which forms of passwordless make the most sense for your app and for B2B vs B2C use cases. Here is an example of what your partner logins and app logins could look like for Customer use cases -
- Partners accessing a resource federated to your Okta org will enter their username and to proceed with login they need to provide just an SMS OTP or just Okta Verify Push. (Factor sequencing)
- Your web app uses Okta for authentication and, to provide a secure, seamless login experience for users, you have enabled Windows Hello. Your app users need only to enter their username and from there they will log into your app via Windows Hello face recognition. (WebAuthn)
- You’ve built a native mobile application and want to deliver a great login experience for users who are either 1) registering to your app for the first time, or 2) logging back into your app after their session token has expired. During the registration process, they just need to enter their email and will receive a link in their inbox to authenticate and establish a session token for your app. If the same user ever needs to log out and log back in, they will have a new link sent to them which they can use to re-authenticate into the app. (Email Magic Link)
How do I get started with passwordless?
By now, you’re sold on the benefits of passwordless logins. Since Factor Sequencing and WebAuthn are newer additions to the product, let’s take a look at how you can enable and set up these two.
Factor Sequencing
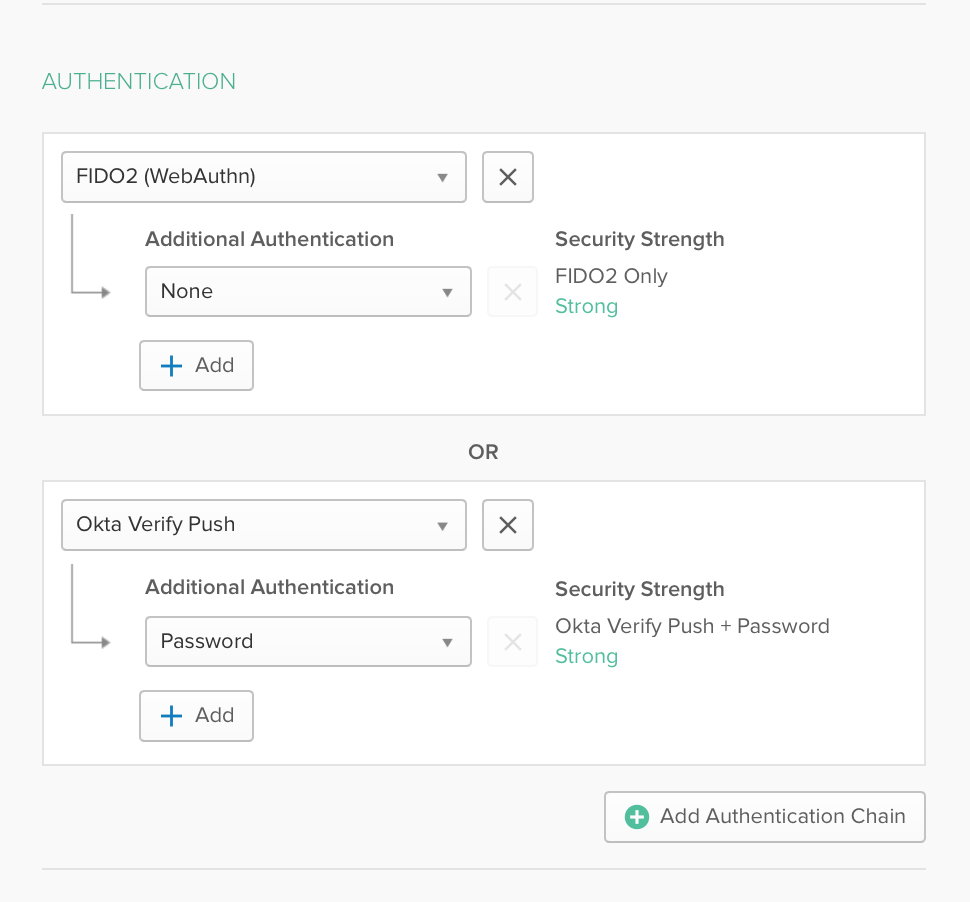
1. In your Okta admin console, go to Settings - Features. Enable the feature flag for Factor Sequencing.
2. Once you have enabled the feature flag, go to Security - Authentication. Click on the Sign On tab.
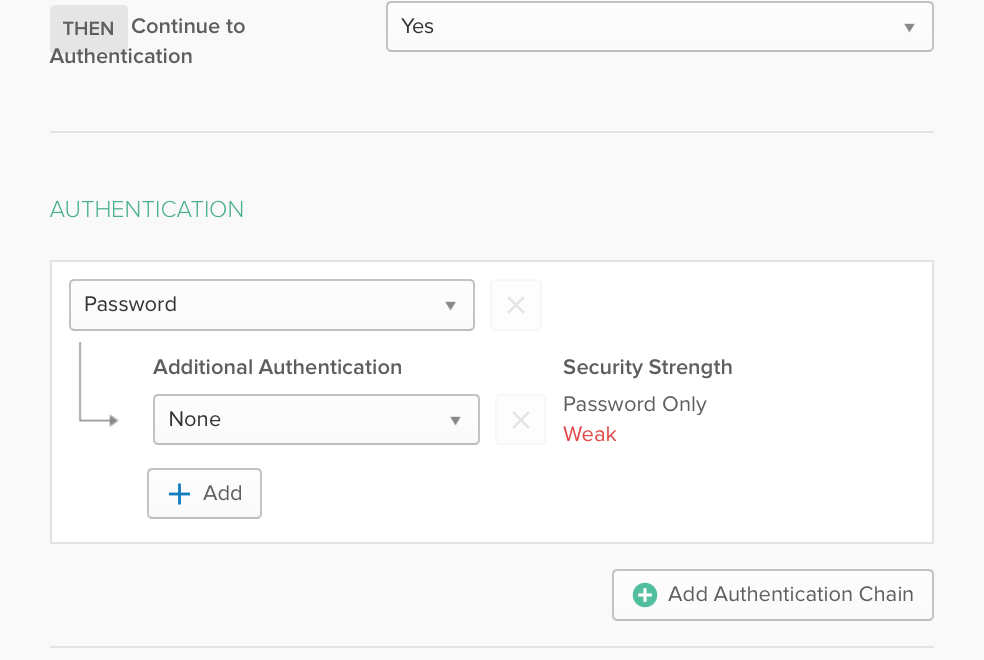
3. When you choose to create a new sign on policy, you will see a modification in the Rules UI that includes an Authentication Chain option.
4. Set an Authentication Chain - this is what your end users will experience when logging in. For example, “Okta Verify Push + None” or “SMS + None”. Save the policy.
That’s it! Now when users targeted with this new policy sign in, they will see the chain of factors you have specified based on the other parameters in the same policy (geolocation, IP etc).
webauthn
1. Contact Okta support to have this feature enabled on your org.
2. Now go to Security - Multifactor. In Factor Types, you’ll see a new option for FIDO2.0/WebAuthn. You may also want to set an enrollment policy for WebAuthn in Factor Enrollment at this time.
3. The rest of the steps exactly match the Factor Sequencing setup mentioned above. Go to Security - Authentication and click on the Sign On tab.
When you choose to create a new sign on policy, you will see a modification in the Rules UI that includes an Authentication Chain option.
Set an Authentication Chain that includes WebAuthn - this is what your end users will experience when logging in. For example, “WebAuthn + None” or “WebAuthn + Okta Verify Push”.
That’s it! Now when the users targeted with this new policy sign in, they will see the chain of factors you have specified based on the other parameters in the same policy (geolocation, IP etc).
Note: for both these features, your users must already be enrolled into the factor(s) defined in your chain or the login process will fail.
Learn more
We hope you are as excited as we are about going passwordless and that this post has been a helpful resource to get you started on that journey! As always, we welcome any feedback on the features mentioned above.
Be on the lookout for more content further breaking down the Workforce and Customer Identity use cases for Passwordless. In the meantime, explore the resources below for more information:
- Whitepaper - Moving Beyond Passwords
- Whitepaper - How to Go Passwordless with Okta
- Webpage - Okta Passwordless Authentication
- Blog Post - What is Passwordless Authentication?
- Data Study - The Passwordless Future Report