Lightweight directory access protocol (LDAP) is a protocol that makes it possible for applications to query user information rapidly.
Someone within your office wants to do two things: Send an email to a recent hire and print a copy of that conversation on a new printer. LDAP (lightweight directory access protocol) makes both of those steps possible.
Set it up properly, and that employee doesn't need to talk with IT to complete the tasks.
What Is LDAP?
Companies store usernames, passwords, email addresses, printer connections, and other static data within directories. LDAP is an open, vendor-neutral application protocol for accessing and maintaining that data. LDAP can also tackle authentication, so users can sign on just once and access many different files on the server.
LDAP is a protocol, so it doesn't specify how directory programs work. Instead, it's a form of language that allows users to find the information they need very quickly.
LDAP is vender-neutral, so it can be used with a variety of different directory programs. Typically, a directory contains data that is:
- Descriptive. Multiple points, such as name and location, come together to define an asset.
- Static. The information doesn’t change much, and when it does, the shifts are subtle.
- Valuable. Data stored within the directory is critical to core business functions, and it's touched over and over again.
Sometimes, people use LDAP in concert with other systems throughout the workday. For example, your employees may use LDAP to connect with printers or verify passwords. Those employees may then switch to Google for email, which doesn't rely on LDAP at all.
LDAP isn't new. The definitive whitepaper that describes how directory services work and how LDAP should interface was published in 2003. Despite its age, LDAP is still in widespread use today.
The LDAP Process Explained
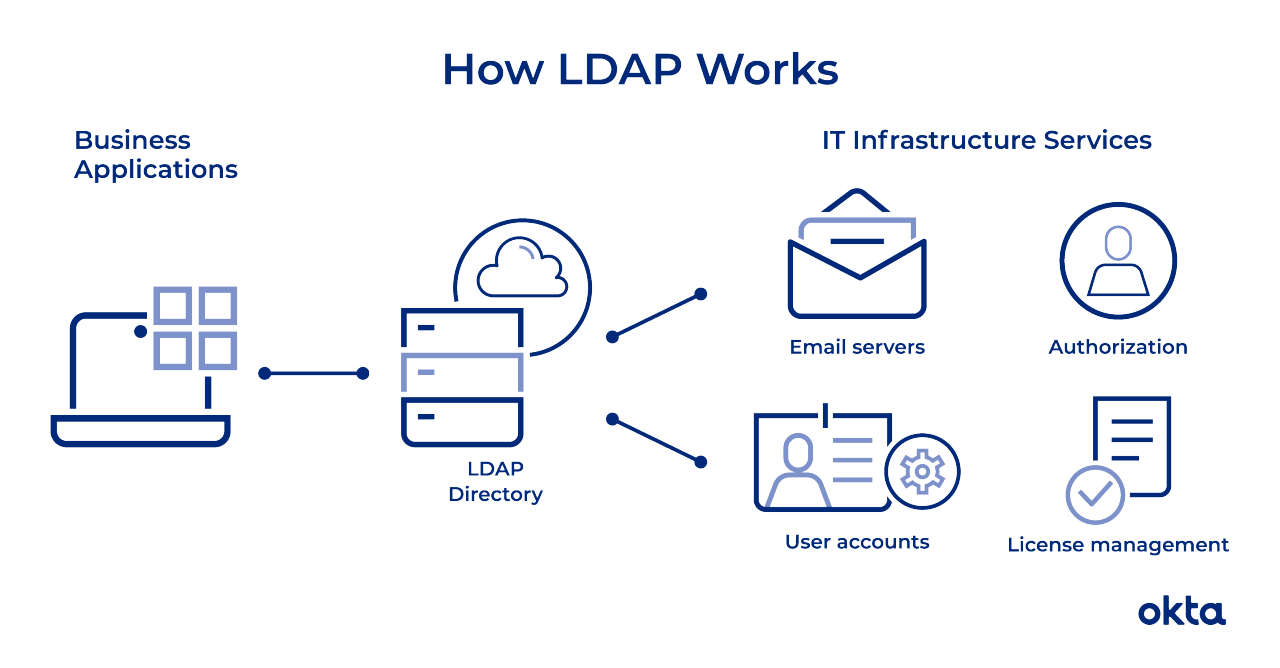
The average employee connects with LDAP dozens or even hundreds of times per day. That person may not even know the connection has happened even though the steps to complete a query are intricate and complex.
An LDAP query typically involves:
- Session connection. The user connects to the server via an LDAP port.
- Request. The user submits a query, such as an email lookup, to the server.
- Response. The LDAP protocol queries the directory, finds the information, and delivers it to the user.
- Completion. The user disconnects from the LDAP port.
The search looks simple, but a great deal of coding makes the function possible. Developers must determine the size limit of the search, the time the server can spend processing it, how many variables can be included in a search, and more.
A person hopping from company to company might run searches with LDAP in each location. But the way the searches work and how they function can be quite different, depending on how the LDAP is configured.
Before any search commences, the LDAP must authenticate the user. Two methods are available for that work:
- Simple. The correct name and password connect the user to the server.
- Simple Authentication and Security Layer (SASL). A secondary service, such as Kerberos, performs authentication before the user can connect. For companies that require advanced security, this can be a good option.
Some queries originate within the company's walls, but some start on mobile devices or home computers. Most LDAP communication is sent without scrambling or encryption, and that could cause security problems. Most companies use Transport Layer Security (TLS) to ensure the safety of LDAP messages.
People can tackle all sorts of operations with LDAP. They can:
- Add. Enter a new file into the database.
- Delete. Take out a file from the database.
- Search. Start a query to find something within the database.
- Compare. Examine two files for similarities or differences.
- Modify. Make a change to an existing entry.
LDAP Terms to Understand
The average person tapping away at a computer doesn't need to know the ins and outs of LDAP. But people who work on network security and access must have a deep understanding of core concepts and structure. And the language people use to describe LDAP can be impenetrable for novices.
Common terms you'll see as you begin to learn about LDAP include:
- Data models. What types of information sit within your directory? Models help you understand the facets within your LDAP. You could have general information (such as an object class), names (how each item is uniquely referenced), functions (how the data is accessed), and security (how users move through authentication).
- Distinguished name (DN). This is a unique identifier of each entry that also describes location within the information tree.
- Modifications. These are requests LDAP users make to alter the data associated with an entry. Defined modification types include adding, deleting, replacing, and increasing.
- Relative distinguished name (RDN). This is a way of tying DNs together while specifying relative location.
- Schema. The coding that underpins your LDAP is known as schema. You'll use this language to describe the format and attributes of each item that sits on the server.
- URLs. This is a string that includes the address and port of a server, along with other data that can define a group, provide a location, or refer an operation to another server.
- Uniform resource identifier (URI). This is a string of characters that defines a resource.
This is just a hint of the language you'll need to master to implement LDAP protocols properly. But since LDAP is an open-source protocol, plenty of documents exist that can help you get started and coding like a professional in no time.
LDAP vs. Active Directory
Some people use LDAP and Active Directory interchangeably, and the habit causes a great deal of confusion. These two tools work together, but they're definitely not the same thing.
Active Directory is a proprietary directory tool that is used to organize IT assets, such as computers, printers, and users. As a Microsoft product, it’s commonly used within the Windows environment. If you have ever worked with Windows on a network, this system underpins some of the data.
LDAP is a protocol that can read Active Directory, but you can also use it with other programs, including those based on Linux. As a vendor-neutral protocol, you could use this tool to work with all kinds of products that have nothing to do with Windows.
So LDAP and Active Directory work together to help users. But they don't compete with one another, and they don't do exactly the same thing.
LDAP + Okta
LDAP helps people access critical files. But since that data is sensitive, it's critical that you protect the information from those who might do you harm. If you're running in a hybrid environment with some parts of your data on the cloud, your risks are even more significant.
Okta can help you protect this critical information. Find out how.
References
What's LDAP? LDAP Linux How To.
A History and Technical Overview of LDAP. LDAP.com.
The LDAP Search Operation. LDAP.com.
Configuring Active Directory for LDAP Authentication. IBM.
Basic LDAP Concepts. LDAP.com.
LDAP URLs. LDAP.com.
Understanding LDAP Schema. LDAP.com.
How to Make Your Company's Single Sign-On Implementation as Smooth as Possible. (July 2016). Forbes.
Active Directory Domain Services Overview. (May 2017). Microsoft.
Understanding Active Directory. (March 2018). Medium.
What Is LDAP Authentication? (July 2018). Houston Chronicle.
Identity Awareness Works Hand In Glove With Digital Transformation. (April 2020). Forbes.
