Ransomware is malware that encrypts your data. A private (and closely guarded) key can make your files readable once more. But hackers typically won't give you that key unless you give them something in return.
A ransomware attack is always serious, and some companies are prepared to pay anything to get their files back again. But you can close vulnerabilities that leave you open to attack. And if you are hacked, you'll need to take quick action to restore normalcy.
What Is Ransomware?
You click and click and click, but you can't see your files. Instead, you see a threatening message that demands money.
What's happening?
You could be dealing with ransomware.
To execute an attack, hackers install malicious software into your system. All you'll see is a demand for money. Pay the fee, and you'll gain access again.
Ransomware might involve:
- A dark screen. You're tapping away on your files, and everything fades to black. All you can see is a demand for money or a set of instructions.
- Endless popups. Your device is flooded with windows containing messages, video, or pornography.
- Malfunctioning devices. Some devices won't turn on at all, or they make horrible noises you can't stop.
The first documented ransomware attack happened back in 1989, and it became widely popular (and feared) in 2012. At this point, millions of people have lived through an attack like this.
How a Ransomware Attack Works
Hackers are clever, and they have all sorts of tricks they can use against you. Ransomware attacks stem from ordinary, everyday activities that you may never suspect or think twice about.
Ransomware is usually deployed in one (or both) of two ways:
- Manual deployment. Here, a hacker gains administrative access to a system and places ransomware on targeted systems.
- Automated deployment. A system is compromised and ransomware installed via the system.
Your servers could be infected via:
- Popups. You're visiting a website, and you see a screen informing you that you're infected with a virus. Tap a button, the message says, and you'll eliminate the threat.
- Email messages. You're sent a note saying that you won money or you need to authorize a delivery. You're shown a button to click.
- Phishing (deception). A website you visit often is hacked. While it looks very similar to your prior visits, tapping buttons leads to unexpected behaviors.
Once you engage with the lure set out by the hacker, your tap leads to the installation of malware. You may not notice this is happening, but your computer is gaining a new friend that quickly encrypts all of your files so you can’t access them.
When the program is complete, you're shown a demand for money. Ransom amounts vary, but most hackers ask for small amounts from individuals. You might be asked for $400 to get your files back.
Large companies with plenty of files see much larger monetary demands. It's not uncommon to face requests of thousands of dollars, and the hacker might ask you to pay with bitcoin.
Ransomware Recovery & Removal
It's easy to think of attacks as simple, amateurish attempts at extortion. Unfortunately, most hackers tap into sophisticated tools that are nearly impossible to replicate or defeat.
If you are attacked, experts recommend these steps:
- Restart. Use Windows' Safe Mode when you restart.
- Scan. Tap into any antivirus program you have, and run as many tests and cleanup functions as possible.
- Restore. If you still can't access files, pull things back to your last saved version.
Every step an individual takes won't help if the malware originates at the server. If your entire company's system is down, the IT team should spring into action to handle the problem. All users should disengage from the system while the team scrubs the virus and restores files.
Could You Be the Target of a Ransomware Attack?
Anyone with a functional computer and a set of files could be enticing to a hacker. You may think you have nothing to share, but a hacker wants your money. But plenty of hackers focus exclusively on big targets, including large corporations.
Hackers could focus on companies with:
- Sensitive files. Health care organizations must keep records safe or face significant reputation problems. Ransomware could put the entire organization's future at risk.
- Significant demand. Government agencies and other similar organizations need around-the-clock access to stay functional. A ransom could get paid quickly in this environment.
- Compromised information. Private detective agencies and security companies know a lot about their customers. Protecting data here could be critical to staying in business.
Analysts say we could be entering a new wave of ransomware attacks. Hackers can build one simple tool (like a global email) and pull in hundreds or thousands of victims all at once. Large companies will pay more than $1 billion to get data back. Hackers just can't resist this payday.
And plenty of companies have fallen victim in the past. In 2017, in one of the most infamous ransomware attacks, more than 200,000 computers in more than 150 countries were struck with the WannaCry ransomware bug. The hackers made plenty of money, and many companies were left with useless files unless they paid.
How to Handle a Ransomware Attack
If you're tempted to pay the hackers to get your files back, you're not alone. But government agencies don't recommend this approach. Your payments encourage hackers to target others in the future, and many criminals ask for even more money when they realize an organization is willing to pay.
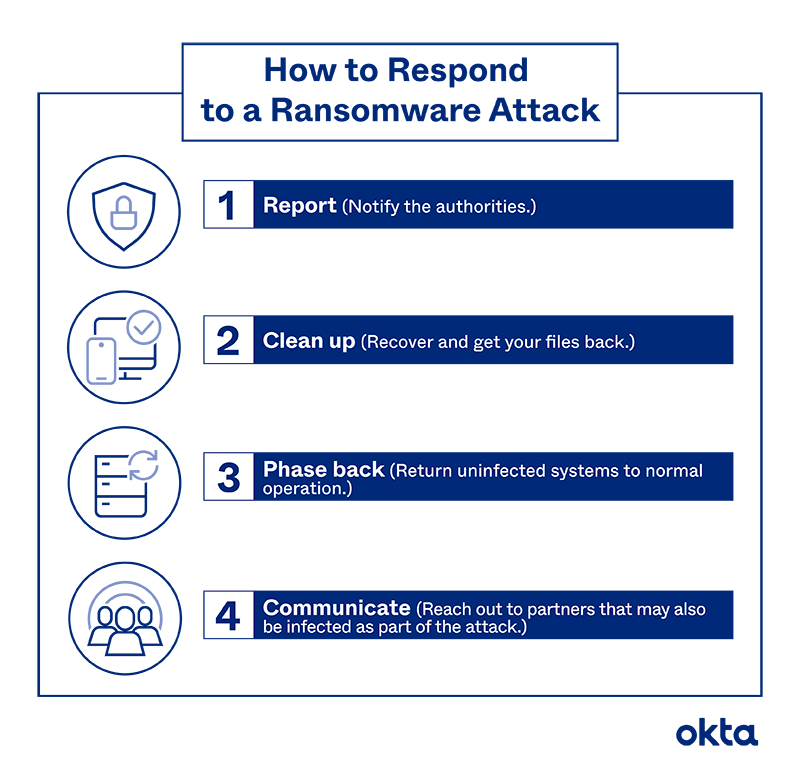
Instead, experts recommend a four-step recovery plan.
- Report. Notify the FBI or the Secret Service about the incident. Ransomware attacks are criminal events, and the authorities should get involved and press charges, when they can.
- Clean up. Ask an experienced advisor (such as one assigned to you from the FBI) to help you recover and get your files back.
- Phase back. As the work progresses, return uninfected systems to their normal operation levels.
- Communicate. Reach out to any business partners that may also be infected as part of the attack.
Every company has a different recovery timeline. You may have files cleaned up, malware removed, and systems operational in just a few days. For other companies, the work could take months or even years.
Prevent Ransomware Before It Begins
Cleanup after an attack isn't easy, and you may lose some kinds of files and data for good. Prevention is a better strategy, as you can halt the bad guys before they get started.
The Cybersecurity and Infrastructure Security Agency has a 16-page manual filled with instructions for companies hoping to strengthen their systems and avoid a future attack. The majority of the tips involve software.
Software shouldn't be static. Companies release patches to reduce vulnerabilities and block hacking attempts, but they won't help if you don't apply them. Ensure that you're always looking over every asset in your organization and enforcing update rules.
Your work is technical, but blocking an attack can also involve commonsense steps everyone in your organization should take. Hold training sessions with your staff and talk about these things:
- Email best practices: Remind your team to resist clicking on links embedded in email, especially if the notes come from someone outside the organization.
- Privacy: Emphasize the importance of keeping usernames and passwords secret.
- Software: Point out that antivirus scanners keep the whole company safe, and those systems should be allowed to do their work.
- Backups: If you are hacked, returning to saved versions may save you intense time and hassle. Encourage your team to follow archiving practices very carefully.
If your team understands the threats you face, you may have more eyes and ears watching for an attack. If they notice a problem, you could stop it before it spreads.
Help From Okta
Our products are made to reduce ransomware risks. We can help you stop leaning on passwords and start relying on technology.
Find out about the products we've used to protect other companies just like yours. And let us create a solution just for you. Contact us to get started.
References
A Brief Summary of Encryption Methods Used in Widespread Ransomware. (January 2017). Infosec.
Frequently Asked Questions: Ransomware. Berkeley Information Security Office.
How to Rescue Your PC from Ransomware. (April 2017). PC World.
Criminals to Favor Ransomware and BEC Over Breaches in 2021. (December 2020). Infosecurity.
Beazley 2018 Breach Briefing. Beazley.
Ransomware: What It Is and What to Do About It. U.S. Department of Homeland Security.
Ransomware Guide. (September 2020). Cybersecurity and Infrastructure Security Agency.
CISA Insights: Ransomware Attack. (August 2019). Cybersecurity and Infrastructure Security Agency.
Ransomware Protection and Containment Strategies: Practical Guidance for Endpoint Protection, Hardening, and Containment. (September 2019). Fireeye.
