What is a Domain Name System (DNS)?
What Is the Domain Name System (DNS)?
The domain name system (DNS) makes it possible for browsers, apps, and servers to load internet resources. Think of it like a phonebook—except instead of associating a person’s name with a phone number, it maps a domain name (e.g., okta.com) to an internet protocol (IP) address that can be understood by systems.
We benefit from the domain name system every time we use the internet—whether we’re searching, shopping, or streaming. In fact, it’s because of the DNS that we don’t have to memorise complex IP addresses (e.g., 104.18.211.105) to access sites and services.
In this post, we’ll take a closer look at how the domain name system works and offer some best practices for DNS configuration and security. But before we can do that, it’s important to understand some key terms.
Domain name system terms and definitions
What is a domain name?
In the simplest terms, a domain name is a website address. These are made up of three essential parts:
- Third-level domains (also known as subdomains) help to organise a website. While “www” is the most common, there are several others available to use. The following URLs use “support”, “docs”, and “help” as third-level domains:
- support.okta.com
- docs.google.com
- help.shopify.com
- Second-level domains are unique to each website and typically contain the name of a business or product. In the URL www.okta.com, “okta” is the second-level domain.
- Top-level domains (TLDs) indicate where a website is hosted. Examples include .com, .org, and .net, among others.
What is an IP address?
IP addresses (expressed as a string of numbers) enable internet-connected devices—from mobile phones to servers—to locate and identify computer services and communicate with other devices.
What is a DNS server?
There are four types of DNS servers—also known as domain name system servers or nameservers—that run behind the scenes, translating domain names into IP addresses which in turn allows users to access web resources.
To understand how each of them works together, we’ll use a library analogy:
- DNS resolver: Think of the DNS resolver as the librarian. Much like a librarian helps you find a book in the stacks, the DNS resolver receives a query for a specific website and helps to identify where it’s located.
- Root nameserver: The root nameserver is akin to a library index, which lists the section of the library where the book might live. The root nameserver directly responds to requests for records and points the resolver towards the location (TLD nameserver) of an IP address. Fun fact: there are only 13 root nameservers in the world.
- TLD nameserver: This server can be thought of as a bookshelf or stack in the library. TLD nameservers are reflected in the last portion of domain (e.g., okta.com is associated with the “.com” TLD nameserver) and have access to all .com authoritative nameservers.
- Authoritative nameserver: The authoritative nameserver, meanwhile, is like a dictionary on that shelf. If it has access to the requested web address, it will answer the query, translating it into an IP address, then returning it to the DNS resolver.
How does the DNS work?
The domain name system works like a regular directory. But since the internet is made up of such a huge network of websites and resources—today, there are more than 350 million domain names—it needs to be distributed across different DNS servers, which are further organised into smaller DNS zones.
Much like it wouldn’t make sense for a single phone book to contain every phone number in the world, there is no single DNS server that holds all the records on the internet. Instead, each of them must work together to convert web addresses into IP addresses.
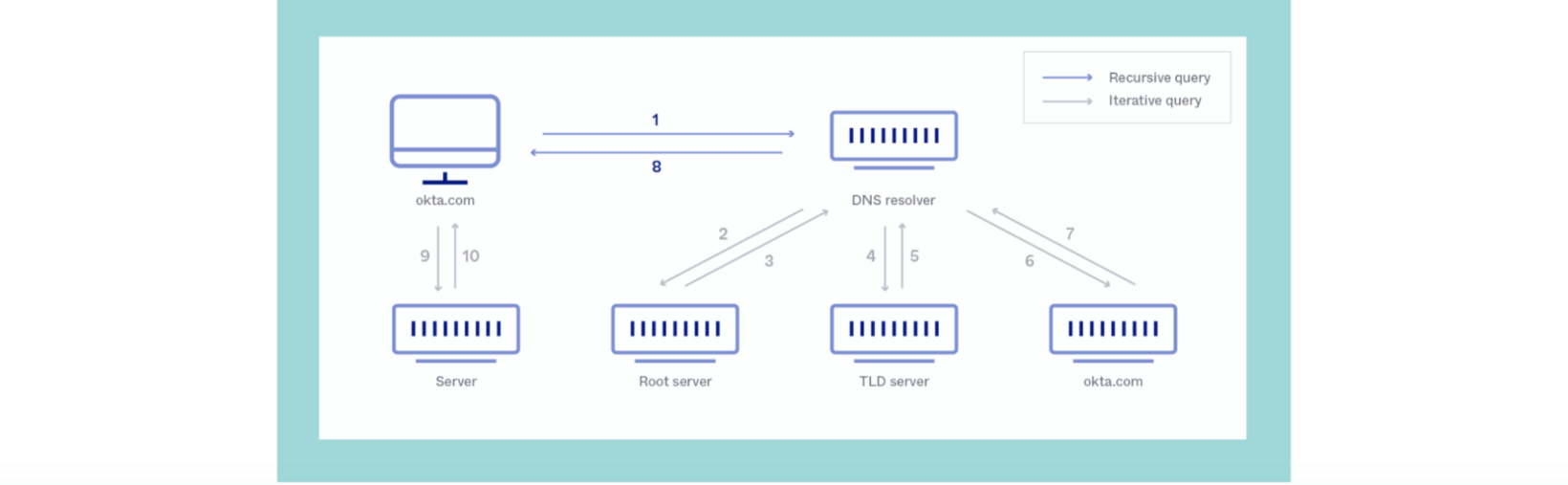
There are seven steps that occur in a DNS lookup:
- A user types a website address into their web browser and hits enter.
- Once the operating system has checked its cache, the request is sent to a DNS resolver (usually the user’s internet provider), which queries the DNS root nameserver.
- The root nameserver issues a response with the address of a TLD nameserver that stores the domain information.
- The resolver makes a request to the TLD, which responds with the IP address of the domain’s nameserver.
- The resolver then issues a request to the domain’s authoritative nameserver, which responds with the IP address for the requested website.
- The DNS resolver sends the IP address to the user’s web browser, finalising the mapping process.
- The browser makes a Hypertext Transfer Protocol (HTTP) request to the IP address, which enables it to render the website in the user’s web browser.
Carrying out this process every time you search for a website would be slow and frustrating. So DNS caching enables information about sites that a user regularly visits to be stored on their computer, which means they can access them quickly and easily.
DNS configuration and security best practices
The DNS is one of the most important parts of the internet’s infrastructure—without it, websites would be unreachable. It’s therefore important to restrict access, keep settings up to date, and use solutions like multi-factor authentication (MFA) to keep it secure.
Common threats to the DNS—and how to protect against them
There are a few ways that malicious actors attack DNS servers:
- Distributed denial of service (DDoS) attacks occur when bad actors attempt to disrupt traffic to a website. Preventing these requires a DDoS mitigation solution that filters out malicious requests from legitimate requests.
- DNS spoofing, also known as DNS poisoning or DNS cache poisoning, is when an attacker causes DNS servers to send incorrect responses to DNS queries. The attacker can then redirect users to malicious websites to steal personal information or force them to download malware. Protecting DNS server access with MFA, updating servers regularly, uninstalling unnecessary applications, and enabling domain name system security extensions (DNSSEC) can all help to prevent these attacks.
- DNS hijacking occurs when a computer is connected to a compromised or malicious DNS server. This sends incorrect IP addresses to the computer, which causes it to visit a different website than the user requested. DNS hijacking can be avoided using trusted DNS services, such as Google Public DNS, and checking a domain’s historical data for record changes.
5 ways to enhance DNS security
Preventing DNS attacks is critical as customers and website visitors will blame the affected company for them not being able to access their account or service. In addition to the above, organisations should follow these DNS best practices:
- Use isolated DNS servers: When companies manage a dedicated DNS server of their own, it enables them to control the information stored through each DNS query. And that means they can reduce their exposure to web application attacks.
- Update DNS servers: If you do decide to run your own DNS servers, they will require regular maintenance to prevent bugs and protect against vulnerabilities. Make sure you always have the latest versions.
- Implement dynamic DNS (DDNS) securely: DDNS will update nameservers automatically—often in real-time—and is a great way to minimise administrative overhead. That said, these updates also need to be properly secured to prevent malicious attacks.
- Limit DNS zone transfers: DNS zone transfers are essentially copies of DNS databases, which could give attackers a clearer view of your network. Limiting these transfers is one of the best ways to protect your DNS zones.
- Set DNS access controls: DNS servers can be configured to only allow access to the right accounts and users. Organisations can also invest in firewalls and other software to block connections from external hosts.
What’s next for the DNS?
When we think about the future of the DNS, we think about security—and that’s where domain name system security extensions come into play.
It’s important for DNS resolvers to verify that the data they’re requesting originates from where it says and to confirm that information hasn’t been intercepted or modified in transit. DNSSEC does this by using digital signatures, which secure every DNS zone with public and private DNS keys—making the internet a safer place to browse.
In addition, adopting DNSSEC is a crucial step toward achieving Zero Trust security. As cloud and mobile adoption continues to grow, businesses can no longer take a network perimeter-centric approach. Instead, they need to enable secure access to several types of users—from employees to partners and contractors—regardless of their location, device, network, or DNS server. With this approach, only the right people have the right level of access to the right resources in the right context.
Integrating your DNS provider and DNS security into your identity cloud will protect against common vulnerabilities. See our DNS integrations or learn more about Okta’s own approach to scaling DNS.

