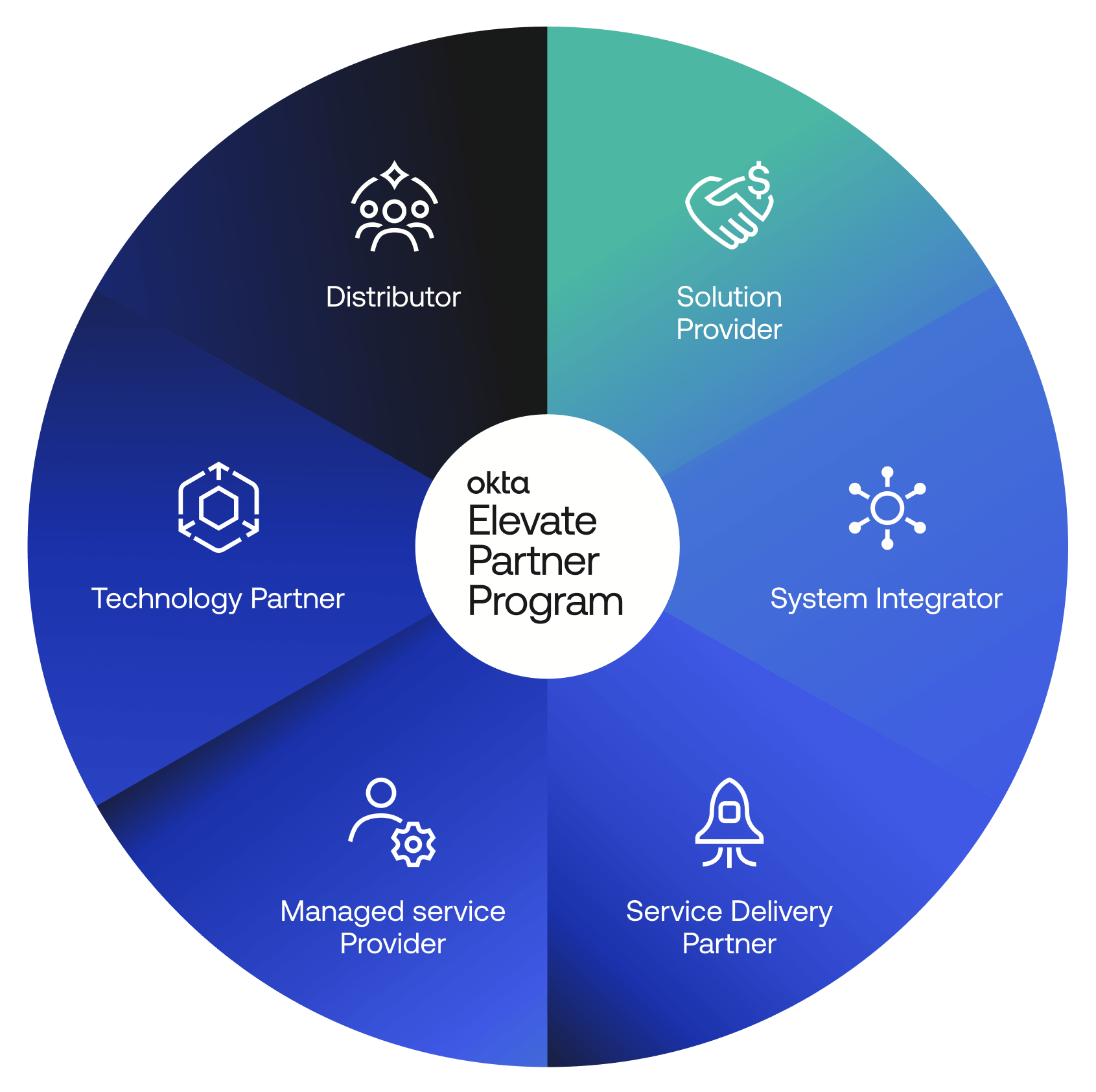
Okta Elevate Partner Program
Our partner ecosystem is more than an extension of our sales team—it’s a vital component of our growth and innovation strategy.
Our strategy
Okta is committed to a partner-first growth strategy – evolving our go-to-market motion, co-investing across the ecosystem, and elevating the partner experience.
We’re building a global ecosystem of the world’s foremost identity experts and application developers with a clear and definitive goal: to free anyone to safely use any technology.