Multi-factor Authentication: Because Phishing Happens
You’re at your desk, neck deep in deadlines (because aren’t we all) and suddenly, a notification appears. You have new mail! At first glance, it looks like the mundane Microsoft service notification email you usually ignore. Then, a moment of panic. What?! They’ve blocked my email?!? I need that! I have important things to do!
You scroll quickly down the message. Great! A link to unlock my messages! Your usual Office 365 login page pops up, and you quickly enter your password.
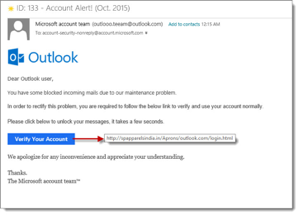
…and now you have a problem. Because that message you initially thought was from Microsoft was actually a credential phishing email. And now someone’s got your username and password.
It’s that easy. And it happens to the best of us. Whether it's because we didn't pause to think as we race through the day checking things off our to-do list, or innate human curiosity got the best of us, there are some links we can’t help clicking. The link to address a wrongful purchase. An "unsubscribe" link. Yes, even an email from an ex asking you to check out her new business. Phishing lures come in all shapes and sizes, and attackers wouldn’t keep using them if they didn’t work.
So what can organizations do to keep from getting phished when clicking has become second nature to most of us? User awareness, education, and having the right tools in place are good places to start.
Protect Your Organization from Phishing
Step one here is to protect your employees. As attacks move from targeting infrastructure to people, it’s critical to address the human element. It’s far more likely for someone to (unknowingly) hand over their credentials than for hackers to break into the network through a vulnerability. Every organization should have a security policy that addresses cybersecurity and phishing in particular. Training should be done on a regular basis so all employees are aware of not only the risks of phishing but their part in keeping the organization secure.
Some companies will also conduct phishing exercises on their employees to keep them on their toes and help them recognize the telltale signs of a phishing lure (inconsistent spelling and grammar, links whose URLs don’t point to where they should when you hover over them, emails that convey a sense of urgency and requesting some action like account verification). A clear process should also be defined for users to report suspicious emails and notify the security team if they suspect their credentials have been compromised.
Employee awareness and education is an important component, but it’s not foolproof. Phishing lures have gotten quite sophisticated and often near impossible to differentiate at first glance between the legitimate site they’re spoofing. Plus, it doesn’t protect against credential theft from personal accounts where the employee used the same credentials as their corporate account. A more realistic mindset may be to assume attackers are already attempting to phish your users (they probably are), and take proactive steps to protect resources in the event credentials are compromised. A relatively simple, yet highly effective way to do this is to enable multi-factor authentication (MFA), or better yet, Adaptive MFA, in front of your applications. (Unsure about what’s what? We’ve got a great blog post on the difference between MFA and Adaptive MFA.)
Add Multi-Factor Authentication for Increased Security
With MFA, users are prompted for another factor after entering in their credentials. So even if their credentials are compromised, there is much less chance of data exfiltration as the attacker would also need to know the second factor, often a one-time passcode, physical token, or even biometric, in order to gain access. For the admin, this can mean the difference between simply resetting the user’s password or launching a full-blown investigation and response, which can also be an expensive PR nightmare.
If you have Adaptive MFA deployed, you have yet another advantage with the granularity of your policies. Since an attacker would typically have very different usage behavior and location/device context than that of the legitimate user, an attempt at logging in would trigger the Adaptive MFA step-up authentication prompt. While this would obviously foil the attacker’s attempt at logging in, security teams would still get visibility into anomalous authentication attempt in the logs and be able to investigate whether the organization is actively being targeted.
While threat actors often have specific victims in mind for spear phishing campaigns, anyone can be the target of a broadscale phishing attack. Okta Adaptive MFA can help prevent unauthorized access to resources in the event of a credential compromise. Our identity data can also be integrated other tools in your security ecosystem like SIEMs to aid in the detection and remediation of security events. To protect your organization from the consequences of phishing, check out our product page and implement Adaptive MFA today.

