Using Personal Identity Verification (PIV) Credentials to Enable Passwordless Authentication
In 2004 President George W. Bush issued Homeland Security Presidential Directive 12 (HSPD 12) that mandated all federal employees and contractors to be given a common identification card that can be used anywhere and everywhere. Acting upon this directive, the Information Technology Laboratory of the National Institute of Standards and Technology (NIST) -- working in conjunction with private industry and other federal agencies developed a standard for a common government-wide identification system.
The standard, Federal Information Processing Standard (FIPS) for a personal identity verification (PIV) system, is based on the use of smart cards with a X.509 compliant certificate and key pair. That is, a physical card containing a digital file that can only be accessed by the owner. It can be used to verify that the PIV credential was issued by an authorized entity, has not expired, has not been revoked, and holder of the credential is the same individual it was issued to.
Similar cards and tokens leveraging the X.509 certificates for personal identification are widely used throughout EU, Latin America, and Asia, all with good reason. Certificates stored on smart cards protected with a personal identification number (PIN) is regarded as one of the strongest multi-factor authentication (MFA) methods available, and in many cases also one of the easiest for end users to use since they can replace username and password completely. For this reason, they have become the de facto standard for payment and ATM cards worldwide.
Challenges with PIV
However, independent software vendors (ISVs) have not widely adapted PIV authentication for their cloud applications, as they have found it cumbersome and difficult to implement securely. And legacy custom applications have not had access to any tools that would enable them to do so either. This has left end users forced to keep using username and password in conjunction to their more secure and modern PIV credentials.
At Okta, we endeavor to connect you to everything that matters, securely and seamlessly. We are happy to announce that we now support support PIV Authentication to make this even easier. Now, end users of federal customers can use their PIV cards already issued to them to authenticate to any app integrated with Okta.
End User Experience
Once your organization has configured PIV authentication, all end users will see a button labelled “PIV Card” on the Okta login screen. When they click it, they will be prompted by the browser for a certificate. They choose the certificate stored on their PIV card, enter their PIN, and they’re in—no username or password required!
If your organization is using Okta to log in to an application like Office 356, accessing that application directly will redirect you to the Okta authentication screen where you can use PIV as the credential.
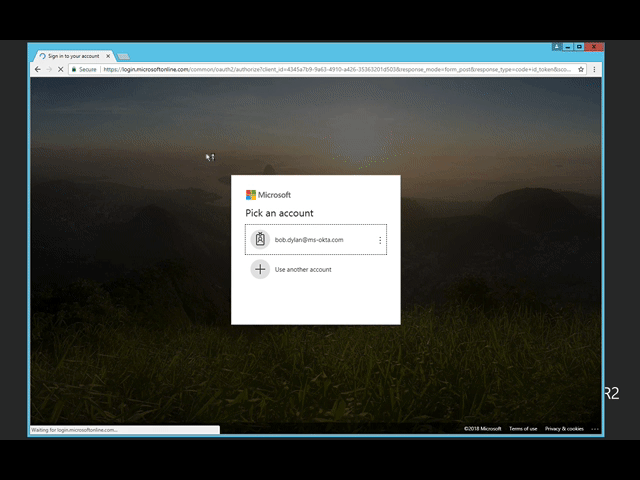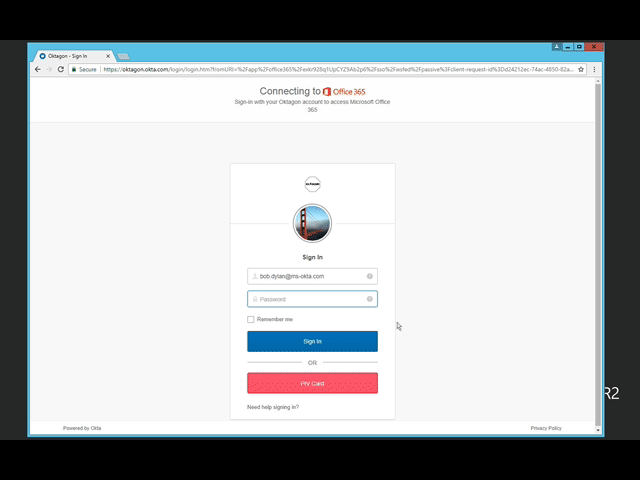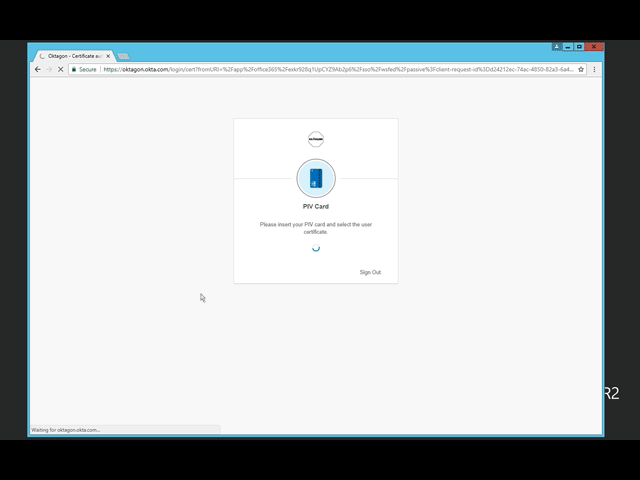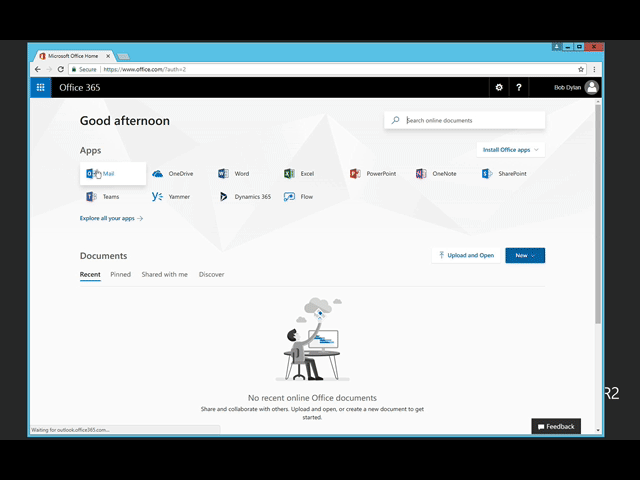
That means you can now add strong secure PIV authentication to any app in the Okta Integration Network. This will help organizations raise their security level by finally getting rid of usernames and passwords. And even if your organization does not use PIV or CAC cards, this feature will make it easy to add support for cards or tokens, as long as they adhere to the X.509 standard.
For more information, read on in the Okta Community.To get started with Okta, choose your free trial here.

