Okta Passkey Management: A New Feature Flag
Apple recently announced support for Multi Device FIDO credentials - also called passkeys. Passkeys allow users a passwordless login to all of their iOS and macOS devices. Passkeys provide a better user experience across websites and apps, and enhance security by virtue of being a standards-based technology that–unlike passwords–is resistant to phishing.They address two major pain points and simplify them from an end user standpoint - account registration and login. However, they can also introduce security risks for organizations that rely on device-bound credentials. This post broadly covers how and why authentication mechanisms have evolved to where they are today, how passkeys work, what kinds of security issues some organizations might face with the introduction of passkeys, and how Okta can help address these issues.
The evolution of authentication mechanisms
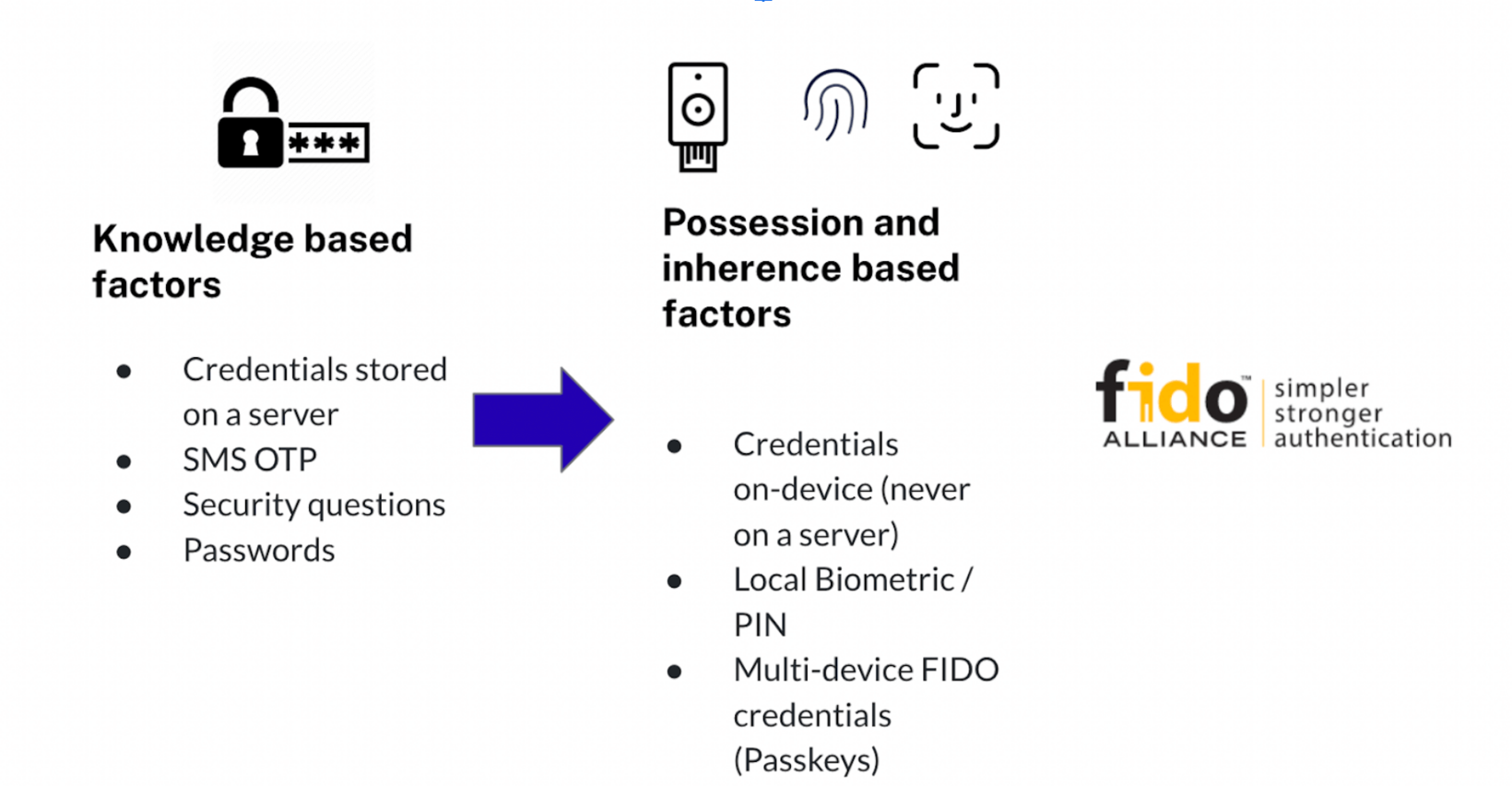
Organizations have historically relied on passwords–shared secrets for authentication. To combat credential-related attacks and improve authentication security, organizations started employing multi-factor authentication–authentication using a combination of factors instead of just one. You’ve probably experienced this in the form of an SMS based one-time Password (OTP) that you were asked to enter after entering your password, or a code you entered using an authenticator app.
These methods, while improving security, can severely affect user productivity and are not phishing resistant. Additionally, many MFA authentication mechanisms still rely on a password as one of the authentication factors, which still creates a security vulnerability.
The recent phishing attacks on Uber, Twilio, and Cloudflare show that as authentication mechanisms have evolved, so have the attack methods. A new and worrying trend is the rise of one time password interception bots along with OTP interception services for sale on the dark web, which specifically aim to intercept TOTPs and use them along with the password in real time, for account takeovers.
To address over-reliance on passwords and other such issues, the Fast Identity Online (FIDO Alliance), an open industry association formed to help improve authentication security and reduce the world’s over-reliance on passwords, began publishing a set of specifications for passwordless and phishing-resistant authentication.
Today, most major browsers have implemented or are implementing the finalized WebAuthn specification, for the first time making a standardized, web-integrated, phishing-resistant authentication mechanism broadly available to relying parties and their users–without the need for special reader hardware, or driver installation.
Impact on 2FA and barriers to adoption
In theory, FIDO-based solutions can drastically increase the security of consumer two-factor authentication by providing phishing resistance, regardless of whether those use cases care about hardware-based sign-in credentials or not. But two major problems have obstructed adoption:
- Recovery issues: Credentials managed by those platform authenticators (authenticators built into devices that the user already owned) are lost when the user replaces or loses the device. Because of this, the user can’t rely on platform authenticators when signing into a mission-critical application for the first time from a brand new device). There is no alternative to having to re-enroll each new device, no easy way to recover from lost or stolen devices.
- Reliance on hardware than can be easily lost or stolen: To ensure phishing resistance, users need to carry around a secure hardware key that can be used as a roaming authenticator–a cross-platform authenticator that can be used to authenticate across multiple devices and is specifically designed to be mobile.
WebAuthn–the enabler for passkeys and passwordless authentication
WebAuthn is a crucial enabler for secure, passwordless authentication. It stands for Web Authentication API and is a specification written by the W3C and FIDO, with the participation of Google, Mozilla, Microsoft, Yubico, and others. WebAuthn allows servers to register and authenticate users using public key cryptography instead of a password. It allows for web applications to simplify and secure user authentication by using registered devices (phones, laptops, etc) as authentication factors. You can read more about how WebAuthn works and best practices recommended by Okta in a handy guide here: How WebAuthn Works.
Multi-device FIDO Credentials (passkeys) and passwordless authentication
Both of the gaps identified earlier in FIDO-based solutions are addressed with multi-device FIDO credentials, also referred to as passkeys. A multi-device FIDO credential is basically a FIDO credential that is backed up (usually to the user’s platform account (e.g., Google Account or AppleID) in a manner that the user is then able to restore the credential to, and use from, another device.
From a user experience standpoint, this will be similar to how one interacts with a password manager today to help them securely enroll and sign into websites from different devices– only it will be far more secure as the server is issued a public key instead of a password. Furthermore, unlike a password manager, there won’t be a need to actually create and save a password as an authenticator–the device biometrics will be used instead. This makes mounting attacks much harder and much more expensive and significantly changes the economics of the attack for bad actors.
Passkeys are primarily meant to eliminate the single-device credential problem that can be a usability nightmare. Passkeys allow the FIDO credential to roam across multiple devices such as phones, tablets, or desktops, and even across different platforms. (Note that Apple has announced support for these already and Microsoft and Google are expected to follow soon.) Account recovery is no longer a problem because credentials are now backed up centrally and can survive the loss of their originating device. Multiple enrollments are not a pain for the same reason. Furthermore, users no longer need to carry around a hardware key and can fall back on their device biometrics for secure, phishing-resistant authenticators.
Potential enterprise security challenges with passkeys
The passkey solution to the usability issue of multi-device credentials can create a security challenge for some enterprise organizations. Since credentials are no longer device bound, users can enroll themselves using a managed device but then access mission critical applications from an unmanaged and unmonitored device that can create risks if that device is not bound by an organizational security policy.
Enterprises may not be comfortable with this change in security assumptions (platform authenticator keys being exportable from hardware), especially if they previously allowed WebAuthn platform authenticators to meet all assurance requirements for enterprise IdP or app sign-in.
Let's consider the example of Bob from Acme solutions. Bob joins Acme and is issued a company MacBook and iPhone. Bob successfully enrolls using passkeys and is now granted access to sensitive applications. The next week, Bob has urgent travel lined up and decides to access these applications with his personal iPad (an unmanaged device not issued by the company) while at the airport. Since passkeys are not device bound, Bob can use his iPad and access these sensitive applications. However, the iPad uses an older, vulnerable version of iOS and does not conform to the security posture requirements of the org; this is a serious security vulnerability. From an admin standpoint, this needs to be addressed immediately.
Organizations need to think through this scenario and other such scenarios resulting from allowing users like Bob to enroll passkeys, and plan their security solutions stack and access policies accordingly.
Okta Passkey Management features
To address this risky scenario, Okta is rolling out a Passkey Management feature that allows admins to block passkeys for new enrollments at an organizational level. This feature flag, when enabled by an administrator, will prohibit a user from enrolling with a multi-device FIDO credential such as passkeys and preempt any potential risks of unmanaged and insecure devices accessing sensitive applications. Note that this does not affect existing enrollments, which will continue to work according to their previous setup. We are working on enhancing this feature so it can also be applied to application sign-on policies in the future.
Admins can thus ensure that security policies are enforced on managed devices only and address the risk of unmanaged and potentially compromised devices accessing mission-critical applications and breaching sensitive data.
This Self Service feature flag is available in Okta Classic and Okta Identity Engine and can be accessed from the Settings page in the Admin Dashboard.
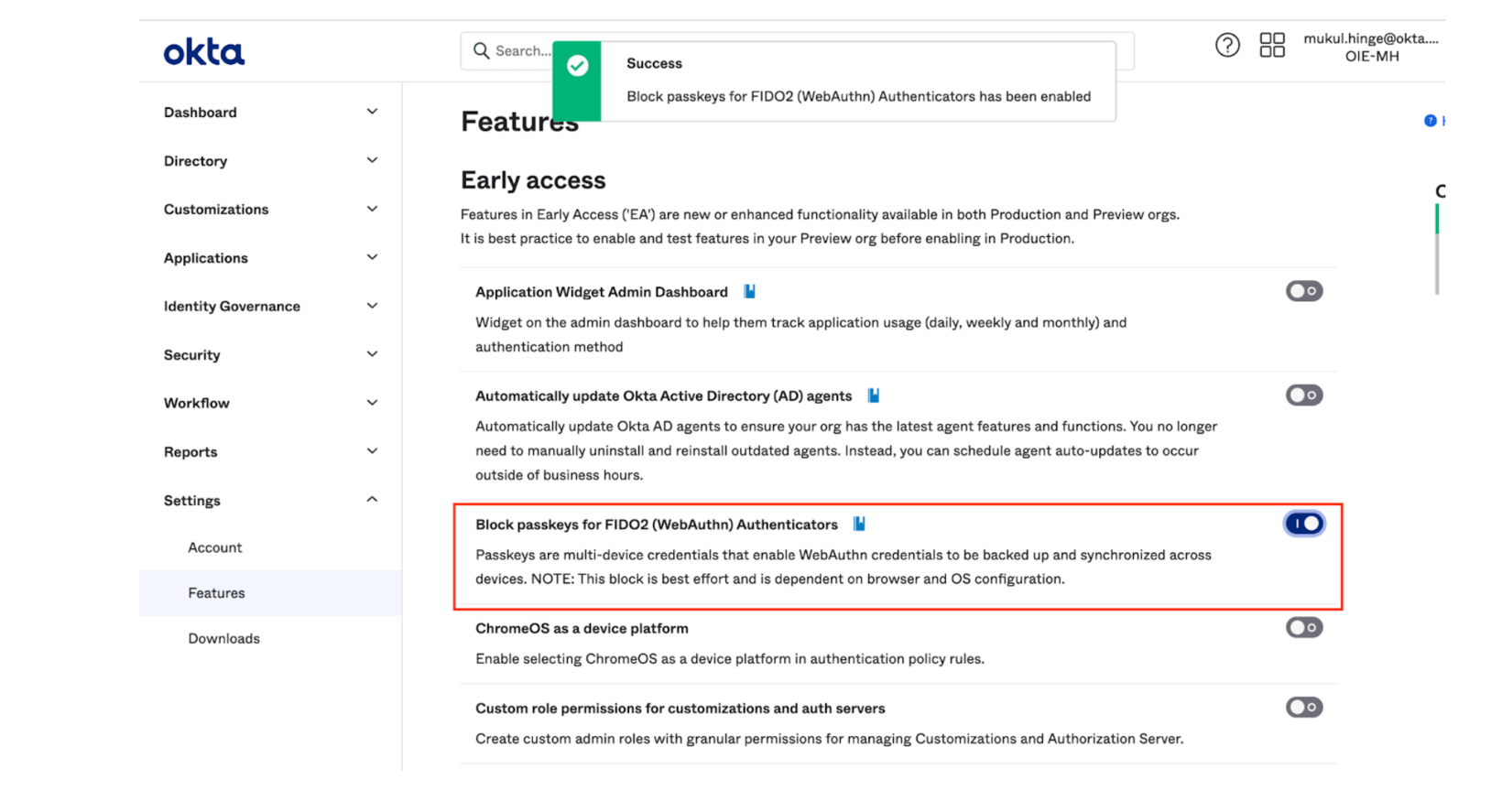
For additional information on this feature and detailed instructions on how to block or allow passkeys in your org, see WebAuthn (MFA) if you're using Okta Classic Engine, or Configure a FIDO2 (WebAuthn) authenticator if you're using Okta Identity Engine.

