Real-time, inline protection that keeps pace with your business
Today's complex Identity threat landscape demands streamlined security practices and an evolving, multi-layered defense-in-depth strategy to identify and mitigate cybersecurity threats. Okta’s comprehensive security strategy addresses these threats at multiple levels, including at the edge, using blocklist zones, configuring ThreatInsight, automated rate limiting, Okta sign-on policies, and strong-factor authentication.
But what about risk post authentication? This critical phase of the Identity lifecycle is traditionally a blind spot for security solutions. Enter Okta's new Workforce Identity product: — Identity Threat Protection with Okta AI. We’ll explore how Identity Threat Protection addresses the need for continuous security beyond initial authentication.
Let's explore the platform within the context of MediaXMedia, an enterprise-level SaaS company that uses Okta Workforce Identity to secure its workforce. We’ll experience this journey through the lenses of two MediaXMedia employees. First, we’ll examine the end-user experience through the insights of Tina Smith, a sales engineer. Then, we’ll shift to the administrative experience from the perspective of Jim Frost, a SecOps team lead.
The end-user perspective
First, let’s explore the day-to-day journey of an end-user. Tina Smith is a sales engineer with MediaXMedia. Tina is a passionate sales engineer who loves to help clients understand and use MediaXMedia’s products, which solve real-life problems and visibly impact clients' businesses. Here’s how Identity Threat Protection provides robust security throughout Tina’s day without impeding her productivity.
Morning: Adaptive authentication in action
8:00 a.m.: Tina logs in to her Okta Dashboard from home using a phishing-resistant authentication factor.
10:00 a.m.: She arrives for her first visit at a prospective client’s office in the city.
10:05 a.m.: Tina attempts to access a new application via the Okta dashboard.
- ITP detects a change in the context of her existing session and prompts her for step-up inline authentication.
The Identity Threat Protection advantage
- Continuous risk evaluation: IP change detected mid-session.
- Precision risk response: Triggered step-up authentication for added security.
- User experience: Tina, aware of MediaXMedia’s security protocols, quickly completes the additional verification.
Afternoon: On the go
3 p.m.: Tina boards a flight to Chicago for another client meeting.
3:30 p.m.: Using in-flight Wi-Fi, she accesses her work email and Slack via Okta FastPass on her mobile device without additional authentication.
3:45 p.m.: Attempting to open Salesforce, Tina encounters another step-up authentication prompt due to a change in context.
The Identity Threat Protection advantage
- Continuous risk evaluation: New network context identified.
- Precision risk response ensures appropriate security measures without disrupting Tina’s workflow.
An unexpected threat
4:30 p.m.: Tina checks her personal email on her BYOD device, enrolled in MediaXMedia’s MDM solution.
4:35 p.m.: Excited about a concert, Tina unknowingly clicks a link in a phishing email, compromising her device.
4:36 p.m.: Tina’s actions trigger a security alert.
The Identity Threat Protection advantage:
- The endpoint solution detects the severe threat and signals Identity Threat Protection.
- Universal Logout is executed across all of Tina’s devices and supported applications.
- Tina is logged out of Okta, Google Workspace, and Slack on her laptop and mobile device.
Resolution
5:30 p.m.: As Tina lands in Chicago, the SecOps team has already neutralized the threat.
6:00 p.m.: Secure and back online, Tina is ready for her next meeting.
Tina’s reflections
That was an action-packed workday for Tina. She’s thankful to her security team for neutralizing the security threat without disrupting her work. They enabled her to focus on what she does best: showing prospective customers the power of her company’s SaaS platform without worrying about her device or sessions being compromised.
The Admin perspective
With the ever-evolving security landscape, including the rise of artificial intelligence (AI), nation-state attacks, and insider threats, Jim and his team face the constant challenge of fending off increasingly sophisticated attacks. To address this, the team has rolled out passwordless and phishing-resistant authentication throughout MediaXMedia. With this, Jim believes that he’s achieved complete protection of identities within his organization. However, he’s aware that attackers are increasingly finding new ways to breach organizations, and they’re now targeting post-authentication. Jim’s team recently rolled out Identity Threat Protection. Let’s go through a day in his life.
Morning: Start the day with coffee and observability
8:00 a.m.: MediaXMedia leverages best-of-breed security vendors to protect diverse threat surfaces. Before ITP, Jim and his team had to spend several hours reviewing dashboards and logs across their XDR, ZTNA, SOAR, CASB, and network tools to determine if any entities across these threat surfaces were at risk. Identity Threat ProtectionI simplifies this work by converging all Identity-related information into the Okta Identity Threat Protection dashboards and reports. A user’s risk in Okta is the convolution of Okta’s own first-party risk and risk seen across all threat surfaces determined by MediaXMedia’s security stack. The SecOps team now uses Identity Threat Protection to streamline how they assess user risk.
- Automated risk calculation: The Risk Engine computes risk across three categories — login, session, and entity — categorizing each as low, medium, or high.
- Continuous evaluation: The risk level is calculated in real time, even if the user is not interacting with Okta. Policy evaluations consume this risk and continuously execute to ensure that the representation of the user’s security posture is always upheld throughout the lifecycle of access.
- Comprehensive detection: Okta’s native first-party signals cover all tactics, techniques, and procedures on the Identity plane. Okta has contributed immensely towards standards like Continuous Access Evaluation Protocol, resulting in integrations with the top security vendors in the industry to share third-party risk signals over the Shared Signals Framework (SSF), ensuring comprehensive coverage of tactics, techniques, procedures(TTPs) intersecting with the Identity plane like device, network, application and data. For those security vendors that are not yet on SSF, Okta offers simple API daisy-chaining mechanisms to integrate risk with Identity Threat Protection.
Jim’s team has observed that certain activities categorized as medium or high risk are, in reality, standard behavior for some users. For example, as a member of the sales team, employees like Tina regularly travel to specific locations, leading to post-authentication IP changes that are expected. To improve the accuracy, Jim has multiple levers. His team can flag false positives identified by the AI engine and provide direct feedback to the risk engine. Additionally, they can configure IP exempt zones or trusted proxies to exclude traffic coming from these IPzaZS’s from being considered for ITP evaluations.
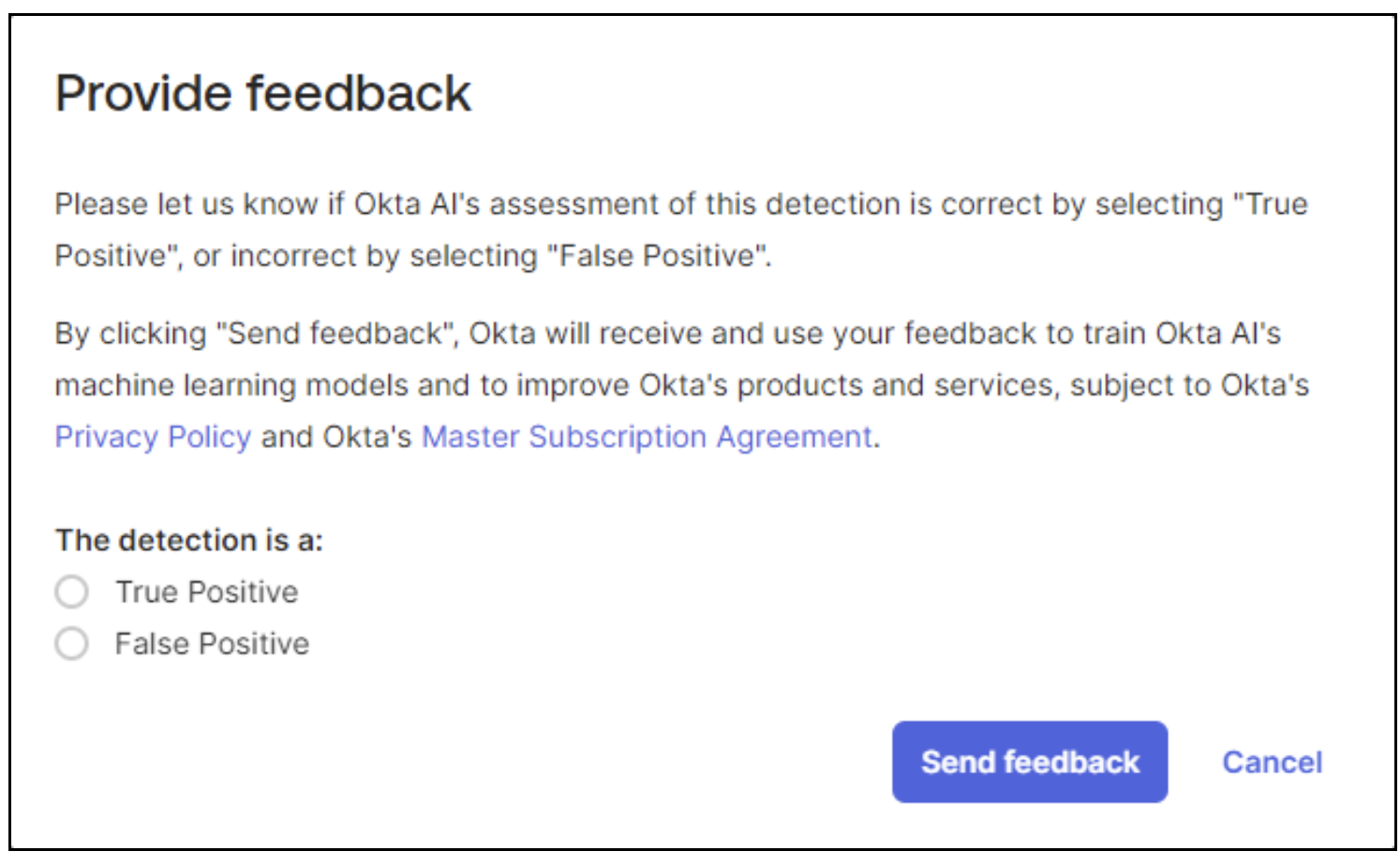
9 a.m.: Subsequently, the SecOps team reviews the Entity Risk detections dashboard/report, which enables them to monitor high-risk detections, their origins, and the corresponding adaptive policy triggers. With Okta’s precise Risk Response capabilities, Jim’s team gains a nuanced and flexible security approach. This integration offers several advantages:
- Receive real-time risk alerts directly in the Okta admin console
- Gain a holistic view of MediaXMedia’s security landscape
- Initiate automated remediation actions based on predefined policies.
|
The Shared Signals Pipeline ensures that threat intelligence flows immediately and seamlessly between systems, enhancing MediaXMedia’s overall security posture. |
To illustrate the effectiveness of continuous risk evaluation, consider a scenario where a user logs in to Salesforce in the morning and uses the application throughout the day. Traditionally, if their session were compromised (e.g., through cookie theft), the threat might remain undetected until the Endpoint Detection and Response solution flags potential malware, which could take hours. This delay in detection poses a significant challenge, as subsequent remedial actions — such as session termination, adjustments to user groups, Okta workflow triggers, and account locks will not be taken in time.
Without Identity Threat Protection, Jim’s security team would encounter considerable difficulties, including
- Time-consuming manual analysis of data from multiple systems
- Hours spent identifying potential security issues
- Delays in running remediation playbooks
- Risk of unchecked damage due to delayed response times
SecOps teams need inline, real-time Identity Threat Detection and Response (ITDR) to address evolving threats effectively. Without inline ITDR, detection delays create substantial vulnerabilities, allowing malicious actors to inflict harm, rendering reactive measures such as session termination, account locks, or access changes ineffective in preventing data breaches or system compromises. Additionally, these delays impact productivity, as security teams spend valuable time investigating incidents instead of focusing on key priorities of the business.
In 2024, it took organizations an average of 194 days to identify a data breach and 64 days to contain it — yet attackers often need only hours to fully compromise an environment. This stark contrast underscores the urgent need for real-time ITDR to minimize exposure and prevent serious damage.
In contrast, Identity Threat Protection's Continuous Risk evaluation offers these benefits:
- Automated analysis of security data occurs in real-time across the organization
- Rapidly identified potential threats
- Policy-driven remediation actions triggered instantly or inline
- Significantly reduced window of vulnerability
This proactive, automated methodology enables Jim's team to stay ahead of potential threats, allowing them to concentrate on addressing genuine risks promptly while minimizing the impact of security incidents on MediaXMedia's operations.
Jim’s team has already configured Identity Threat Protection policies tailored to address specific cybersecurity threats. Okta’s precision risk response capabilities provide MediaXMedia with a nuanced and flexible approach to responding to these threats. These options include:
- Universal Logout: Ability to terminate active application sessions and revoke Okta's Identity Provider (IDP) session across all devices for applications that support the Universal Logout framework. You no longer have to wait for application access to expire.
- Inline MFA: For instances categorized as medium risk events, the team can minimize significant end-user disruptions by simply requesting inline step-up authentication.
- Workflow-driven responses: In elevated risk events, Jim’s team uses Okta Workflows to automatically trigger alerts, generate JIRA tickets, and segregate high-risk users into restricted access groups.
This multi-tiered approach allows Jim’s team to respond proportionately to different threat levels. For instance, when Identity Threat Protection identifies a change in risk, network zone, device, or behavior, it can automatically launch mitigation and remediation actions that Jim's team has configured according to MediaXMedia's security requirements.
In practice, this means:
- For low-risk changes: The system might simply log the event for later review.
- For medium-risk events: Users might be prompted for additional authentication.
- For high-risk situations: The system could automatically revoke sessions via Universal Logout or leveraging Workflows, restrict access, and alert the security team for immediate investigation.
11 a.m. - 4 p.m.: Meetings and other security-related tasks
Afternoon : Neutralize Identity threats for MediaXMedia users
4:36 p.m.: Receive Slack notification that user “Tina Smith” has a compromised device. This risk was transmitted via JamF over the Shared Signals Framework. Identity Threat Protection has automatically set her user risk level to HIGH and moved her to the “quarantine users” group in Okta, and she has lost access to all her applications.
4:40 p.m.: Remediation workflows triggered automatically by Mobile Device Management system. Once the device is clean, the user is removed from the quarantined group. Her risk in Okta is reset to LOW, restoring her access to necessary applications. Automated email sent to Tina explaining what had happened. The threat to Tina’s user identity has been neutralized.
Evening: Follow the sun
5 p.m. and onward: Security never sleeps. MediaXMedia’s distributed global security team takes over, ensuring continuous coverage, just like Okta Identity Threat Protection.
Jim’s reflections
Normally, piecing together the threat investigation for a user's access journey like Tina Smith’s would have taken his team several hours. With ITP, this was detected and remediated in minutes. Because they were able to react in time, they managed to prevent additional compromise such as lateral movement, privileged access, and data exfiltration. His team truly begins to appreciate the value delivered with inline, real-time, and comprehensive protections offered by Identity Threat Protection that also integrate well with their security stack. They love the Identity Threat Protection dashboard, which has become a one-stop shop to determine risk for their users across threat surfaces.
Identity Threat Protection’s sophisticated machine learning methodologies evaluate session risks in real time. By analyzing extensive data sets, Okta's AI models identify irregular patterns and anticipate potential threats proactively. Through AI-enhanced risk scoring, each session's risk level is continuously assessed by considering user behavior, device context, and network details.
This adaptive scoring mechanism allows for swift adjustments to security protocols, bolstering defense mechanisms without disrupting user interactions. The utilization of machine learning algorithms aids in discerning between normal and suspicious activities with heightened accuracy, thereby prioritizing authentic threats while minimizing unwarranted disturbances to legitimate users.
Now that you have read about a day in the life of Jim, our SecAdmin and Tina, our end user, you can see how Okta Identity Threat Protection with Okta AI significantly enhances MediaXMedia’s security posture and, at the same time, does not impede end users from securely accessing essential resources.






