The power of collaboration shines at Gartner IAM 2025
The Gartner IAM Summit in London (March 2025) highlighted a significant industry shift towards interconnected, real-time security, with overwhelming interest in the OpenID Foundation's Shared Signals Framework (SSF) and Continuous Access Evaluation Profile (CAEP).
Moving beyond theory, the summit showcased working, interoperable implementations from pioneers like Okta, Google, IBM, Omnissa, SailPoint, and Thales, proving the standards' practical viability and Okta's commitment to open ecosystems.

Today, we’ll explore how Okta is actively championing and implementing open standards like SSF and CAEP, as demonstrated at Gartner IAM 2025, to forge a more interconnected, responsive, and secure digital ecosystem for organizations and their users.
We’ll delve into the standards themselves, trace Okta's consistent leadership in interoperability, showcase how these standards power Okta's solutions like Identity Threat Protection, and articulate the profound benefits this collaborative approach brings.
What’s the need for the new standards?
Traditional protocols like SAML and OAuth typically validate access only at the moment of login. However, a user's security context can change significantly during a session (e.g., their device might become non-compliant, or suspicious activity might be detected). Without a mechanism like CAEP, applications and services continue to trust the initial authentication, potentially leaving doors open for attackers operating with outdated session data.
SSF and CAEP allow systems like identity providers, mobile device management platforms, or security analytics tools (Transmitters) to notify relying parties like applications, VPNs, or API gateways (Receivers) about these critical changes in real-time. This enables continuous evaluation and dynamic adjustment of access rights based on the most current information. This represents a fundamental shift from static, point-in-time security decisions towards dynamic, continuous risk assessment throughout the session lifecycle.
Understanding the standards: The foundation for real-time security
Let’s dive into how the SSF and the CAEP are at the heart of this evolution.
Shared Signals Framework (SSF): The secure communication backbone
Think of SSF as the secure, standardized communication highway for security information. It's an OpenID Foundation standard that defines how different systems, designated as transmitters (sharing information) and receivers (consuming information), can exchange security-relevant signals or events in near real-time. It leverages secure webhooks and established protocols (supporting push and poll delivery models) to ensure reliable communication. The actual event messages are packaged as Security Event Tokens (SETs), which are based on the JSON Web Token standard, ensuring data integrity and authenticity.
The fundamental purpose of SSF is to dismantle the data silos that plague traditional security architectures. By enabling different tools — from identity platforms to endpoint security solutions — to speak a common language, SSF facilitates coordinated threat detection and response, fostering a more unified and effective security posture. It provides the essential "digital plumbing" required for true security interoperability
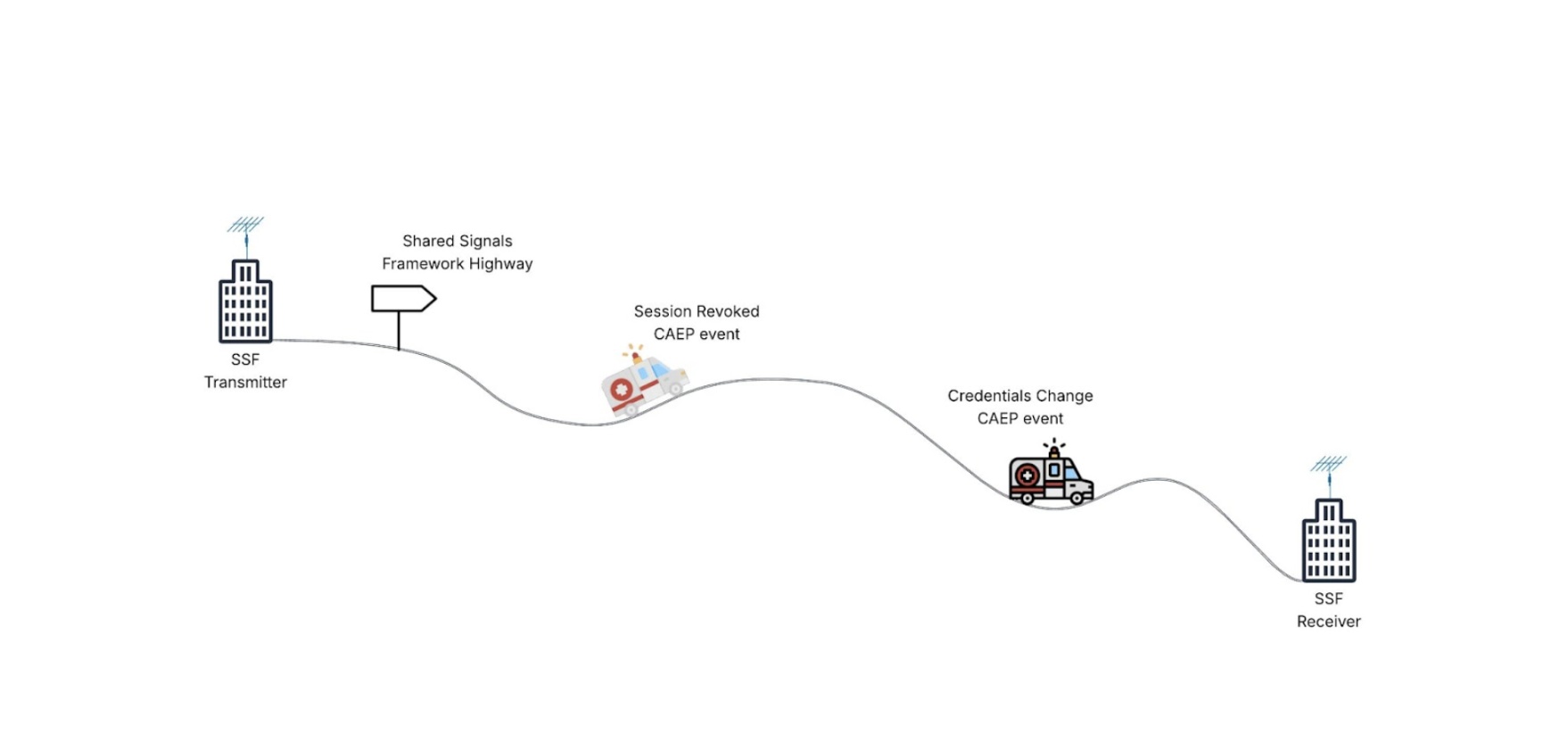
CAEP: Enabling dynamic trust
While SSF provides the framework for communication, CAEP defines a specific set of event types transmitted using SSF. CAEP focuses specifically on events and context changes that occur during an active user session, after the initial authentication has taken place.
The types of events defined by CAEP illustrate its power:
Event Type | Description | Example Use Case |
session-revoked | Signals that a specific user session should be terminated immediately | User logs out elsewhere; admin terminates session; high-risk behavior detected |
credential-change | Notifies of changes to user credentials (password reset, multi-factor authentication (MFA) enrollment/removal) | Force re-authentication after password change; update session based on MFA status |
device-compliance-change | Indicates a change in the security posture or compliance status of a device | Block access from non-compliant device; trigger step-up authentication if check fails |
token-claims-change | Signals that attributes or claims associated with the session have changed | Update user permissions in an app based on a change in group membership or role |
assurance-level-change | Indicates a change in the level of assurance for the user's authentication method | Require step-up authentication if assurance level drops below policy requirements |
= NEW = risk-level-change | Indicates risk level associated with the subject changed | Risk engine identified a real time anamoly/detection for the user, device, session, or tenant |
The latest CAEP version will also define a brand new risk-level change event. This event will help software vendors communicate risk or a threat level detected in real time.
It's also important to note that SSF isn't limited to CAEP. It also encompasses the Risk Incident Sharing and Coordination (RISC) profile, which focuses on broader account-level events like credential compromise or account disablement. This dual focus on session-level (CAEP) and account-level (RISC) signals demonstrates a holistic approach within SSF, providing a comprehensive framework for sharing diverse security intelligence.
The Zero Trust connection
The principles of SSF and CAEP align perfectly with the core tenets of a Zero Trust security architecture: "Never Trust, Always Verify." While initial authentication establishes a baseline, Zero Trust demands continuous verification of trust throughout a user's session. CAEP provides the standardized mechanism to achieve this "Always Verify" principle.By enabling the real-time exchange of context changes – relating to the user, their device, their credentials, or their behavior – CAEP allows organizations to dynamically adjust access controls and enforce policies continuously, rather than relying on potentially stale, point-in-time authentication decisions. Trust is no longer static; it's modulated based on real-time signals.
The value proposition: Why interoperability matters
The industry-wide shift towards standards like SSF and CAEP, championed by Okta and its partners, delivers compelling benefits for organizations:
- Enhanced security effectiveness: Breaking down silos means security tools can share context. An alert from an EDR about malware on a device can be instantly shared via SSF/CAEP with Identity Threat Protection with Okta AI (ITP), which can then restrict that user's access to sensitive applications. This collaborative defense provides a more holistic view of threats and significantly reduces the risk of attackers exploiting gaps between tools. It also helps minimize attacker dwell time by enabling faster detection.
- Real-time response and mitigation: Speed is critical in cybersecurity. SSF/CAEP facilitates near real-time communication, replacing slow batch processes or manual data correlation. When a risk is detected — a compromised credential, a device falling out of compliance, a user logging in from a suspicious location — automated actions like session revocation or enforced MFA can be triggered immediately via CAEP signals. This dramatically shrinks the window of opportunity for attackers.
- Simplified security operations: Managing a complex web of custom, point-to-point integrations between dozens of security tools is a significant operational burden. Standardized protocols like SSF simplify this dramatically. A common framework for exchanging signals reduces integration complexity, lowers maintenance overhead, and frees up security teams to focus on higher-value tasks like threat analysis and policy refinement. This shift allows organizations to focus less on building the "plumbing" and more on leveraging the "intelligence" derived from the shared data.
- Fostering innovation and choice: Open standards combat vendor lock-in.When security tools can readily interoperate via SSF/CAEP, organizations gain the freedom to choose best-of-breed solutions that best meet their specific needs, knowing they can integrate them effectively. This fosters a healthier, more competitive ecosystem, encouraging vendors to innovate and accelerating the adoption of cutting-edge security technologies.
- Building a "trust fabric": The ultimate outcome of widespread SSF/CAEP adoption is the creation of a "trust fabric," a term highlighted at the Gartner event.This represents a dynamic, interconnected security ecosystem where signals flow seamlessly between trusted entities. Each participating system contributes to and benefits from the collective intelligence, enabling continuous evaluation and adaptive security postures across the entire environment.Okta's ITP, acting as a central hub for signal aggregation and response, is a key enabler of this fabric. The value of this fabric grows exponentially with each new participant, creating a powerful network effect that benefits the entire community.
Okta in action: Consistent leadership in interoperability
Okta's commitment to SSF and CAEP is not a recent development. Rather, it’s a consistent thread woven through our product strategy and industry engagement.
Gartner IAM 2025 Showcase
Okta's participation in the March 2025 Gartner IAM London SSF/CAEP interop showcase was a clear demonstration of this ongoing commitment. Beyond the interoperability demonstrations, Okta’s very own Arkadiusz Krowczynski also presented a dedicated session titled “Identity Threat Protection: Okta's AI Revolution in Identity Security.” This event builds upon a strong history of championing and demonstrating SSF/CAEP interoperability in March 2025, in London, and also in December 2024, Grapevine, Texas
This consistent, public participation in interoperability events serves multiple strategic purposes. It showcases Okta's technical leadership and the maturity of its implementations. Crucially, it also actively encourages and validates the efforts of other vendors, helping to build the broad ecosystem adoption necessary for standards like SSF and CAEP — and by extension, Okta's own advanced features that rely on them — to deliver maximum value.
Okta Identity Threat Protection: Standards in practice
Okta Identity Threat Protection stands as a prime example of how Okta translates its commitment to open standards into tangible customer value. Identity Threat Protection is designed to detect, assess, and respond to identity threats across the entire authentication lifecycle — before, during, and after login.
Critically, Identity Threat Protection leverages these real-time, cross-ecosystem insights to enable continuous monitoring and dynamic response, directly implementing the core principles of CAEP.
Imagine a scenario where an employee's device inadvertently downloads malware. An integrated endpoint detection and response (EDR) solution detects this threat. Acting as an SSF transmitter, the EDR tool immediately sends a CAEP device-compliance-change or risk-level-changed event through the Shared Signals Pipeline, signaling that the device is no longer secure. Okta Identity Threat Protection, as an SSF receiver, ingests this critical signal.
Okta AI then assesses the heightened risk associated with the user and their compromised device. Based on predefined policies, Identity Threat Protection can then automatically trigger a CAEP session-revoked event, terminating the user's active sessions across connected applications to prevent lateral movement or data exfiltration by the malware.
This rapid, automated response, orchestrated through open standards, significantly mitigates the potential damage from the malware infection. By championing and implementing SSF/CAEP, Okta enhances its product offerings and fosters the broader ecosystem adoption necessary for these standards to deliver maximum security value.
Okta aims to orchestrate and interpret signals from diverse security domains, providing a unified view of identity risk and enabling coordinated responses across the entire ecosystem.
Okta's enduring commitment to a secure, open future
Okta's sustained leadership in promoting and implementing the SSF and CAEP was prominently displayed at the Gartner IAM Summit 2025. This commitment is part of a broader strategy to foster a more secure and interoperable digital ecosystem. By embedding these open standards into core products like Okta Identity Threat Protection, Okta enables real-time, collaborative defense for its customers.
Furthermore, Okta's foundational involvement in the OpenID Foundation's Interoperability Profiling for Secure Identity in the Enterprise working group signals a long-term vision for comprehensive, end-to-end security standards. This forward-looking approach underscores Okta's belief that SSF and CAEP are vital steps towards a future where security is inherently integrated and adaptive. Okta remains dedicated to driving this collaborative industry effort, recognizing that shared standards are essential for creating a resilient and safer digital world for all.
Learn more
- Explore Okta's commitment to CAEP and SSF (December 2024): https://www.okta.com/blog/2024/12/oktas-commitment-to-caep-and-ssf-pioneering-secure-interoperable-identity-standards/
- Learn about Okta's initial SSF interoperability showcase (February 2024): https://www.okta.com/blog/2024/02/unifying-efforts-amplifying-security-shared-signals-interoperability/
- Discover Okta Identity Threat Protection: https://www.okta.com/platform/identity-threat-protection/






